Comprehensive security for digital transformation
To be successful in today’s hybrid work environment, IT and security teams need to rethink networking and security. This is where a zero trust architecture comes into play. Zero trust is a holistic security approach based on least-privileged access and the idea that no user or application should be inherently trusted. It assumes all connections are hostile and only grants access once identity and context are verified and policy checks are enforced.
Zscaler delivers zero trust through the Zero Trust Exchange—an integrated, cloud native platform that securely connects users, workloads, and devices to applications without connecting to the network. This unique approach eliminates the attack surface, prevents lateral threat movement, and protects against compromise and data loss.
THE SEVEN ELEMENTS OF ZERO TRUST
See a zero trust architecture in action
Verify identity and attributes
Control content and context
Enforce policy, per-session decision and enforcement
See it in action
See the Zero Trust Exchange in action
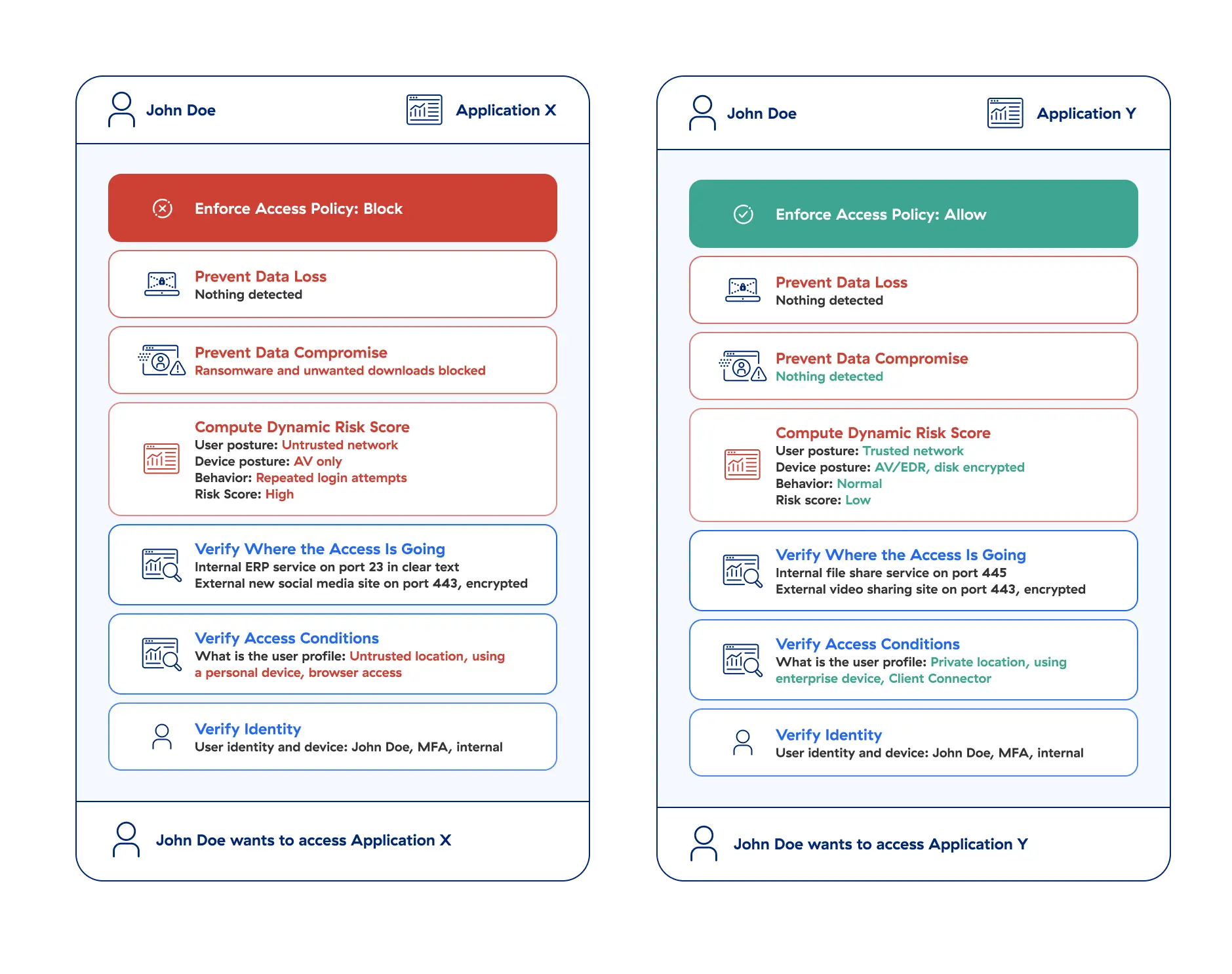
Follow Jane and John Doe on their journey through the zero trust process of accessing applications to see how the seven elements are applied by the Zscaler Zero Trust Exchange.