Once upon a time, encrypted traffic was considered the safe, secure option for browsing and doing business online. Going back nine years to December 2013, the Google Transparency Report shows just 48% of worldwide web traffic was encrypted. Flash forward to today, and the volume of encrypted web traffic tracked by Google is up to 95%. However, the threat landscape has changed a lot since 2013, and now we find the majority of cyberthreats lurking within encrypted channels.
Hidden in the layers of your encrypted internet traffic are malware payloads, phishing scams, sensitive data leaks, and more. To understand this better, Zscaler ThreatLabz researchers tapped into the Zscaler Cloud and analyzed 24 billion threats from October 2021 to September 2022 to reveal details on threats embedded in HTTPS traffic, including SSL and TLS. The team published the full results of this research in the State of Encrypted Attacks 2022 Report.
Leveraging insights from more than 300 trillion daily signals and 270 billion daily transactions in the Zscaler Zero Trust Exchange™, the report shows a consistent upward trend of attacks using encrypted channels—from 57% in 2020 to 80% in 2021, ultimately finding that more than 85% of attacks were encrypted in 2022, with a total attack volume 20% higher than 2021. Other key findings from the report include:
89.9% of encrypted threats involve malware
While cybercriminals hide a variety of attack tactics in encrypted traffic, malware continues to be the most prevalent. Malicious scripts and payloads used throughout the attack sequence make up nearly 90% of the encrypted attack tactics blocked in 2022 (see figure 1).
Malware continues to pose the greatest threat to individuals and businesses across nine key industries, with manufacturing, education, and healthcare the most common targets. This category includes ransomware, which remains a top concern for CISOs as ransomware attacks have increased 80% year over year.
The most prevalent malware families the ThreatLabz team observed abusing encrypted channels include ChromeLoader, Gamaredon, AdLoad, SolarMarker, and Manuscrypt.
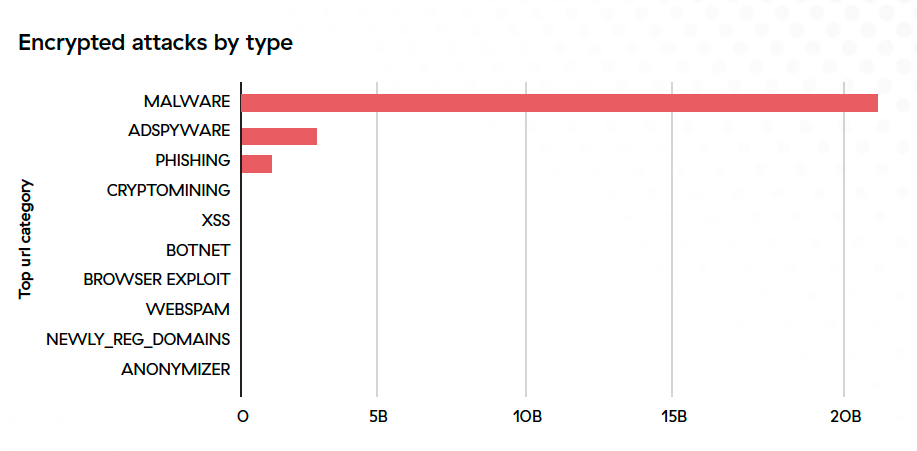
Figure 1: Distribution of 2022 encrypted attacks classified by threat type
The US and India are the top targets for encrypted attacks
The five countries most targeted by encrypted attacks in 2022 were the US, India, South Africa, the UK, and Australia. South Africa is a relative newcomer to the list, soaring to the top in 2022 after bumping France from the 2021 top five. A number of countries saw significant upticks in targets year over year, including Japan (+613%), the US (+155%), and India (+87%).
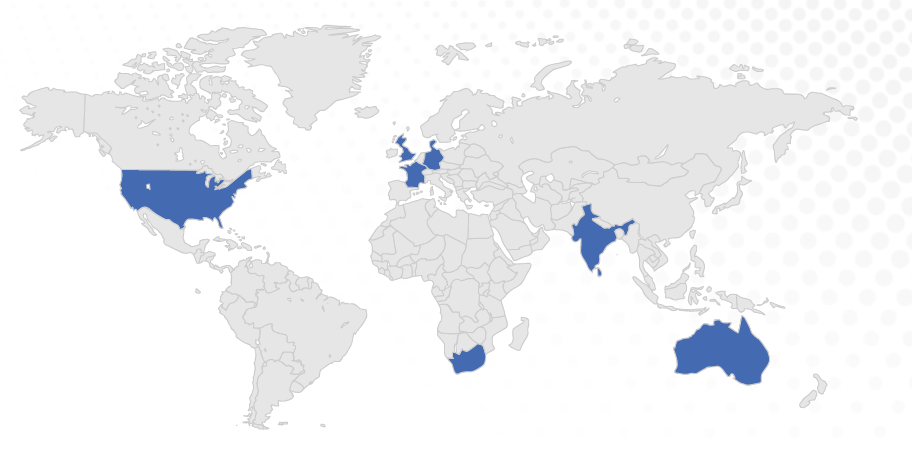
Figure 2: Top geographical targets for encrypted attacks in 2022
Encrypted attacks increased against manufacturing by 239% and education by 134%
More than doubling in encrypted attacks, manufacturing displaced technology as the most targeted industry in 2022. Attackers appear to particularly favor manufacturing over other industries as a target for ad spyware. It is also one of two industries most often phished via encrypted channels—the other being healthcare.
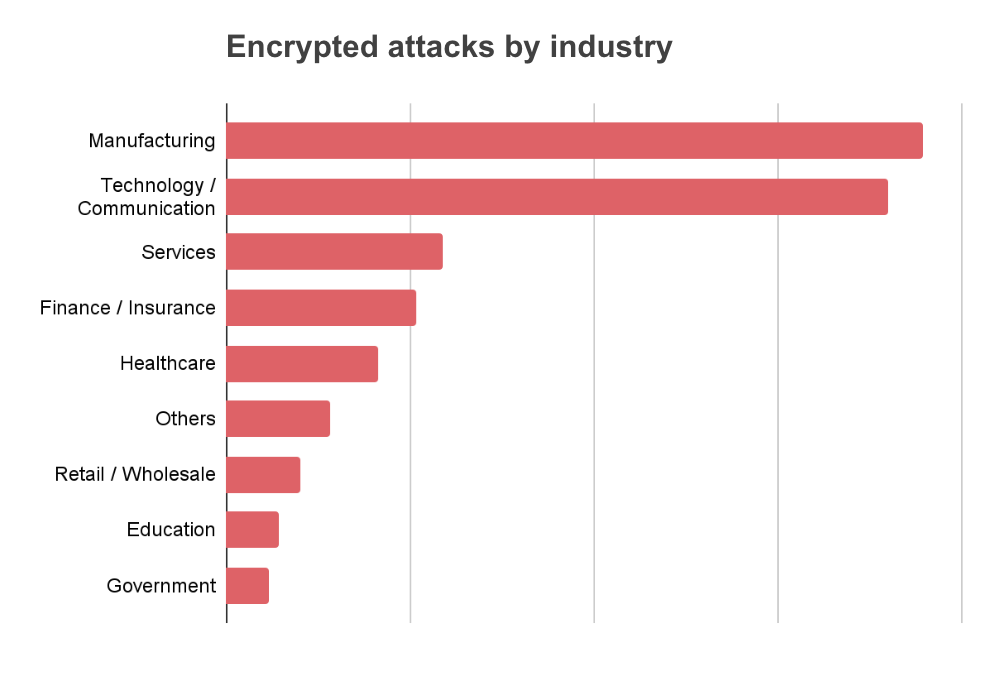
Figure 3: Top industries by vertical targeted by encrypted attacks in 2022
Zscaler secures organizations against encrypted attacks at scale
The report’s main takeaway is this: if you’re not looking at encrypted channels, you don’t know if you’re suffering data leaks or if advanced threats are reaching your users. To help our customers stay secure, Zscaler blocked 24 billion threats over encrypted channels in 2022—a 20% increase from the 20.7 billion blocked in 2021, which was a 314% increase from 2020. This shows that cybercriminals are continuing to evolve their tactics to avoid detection and slip past information security teams.
Today, most attacks leverage SSL or TLS encryption, which is resource-intensive to inspect at scale and best done with a cloud native proxy architecture. While legacy firewalls support packet filtering and stateful inspection, their resource limitations make them poorly suited for this task. This creates a critical need for organizations to implement cloud native architectures that support full inspection of encrypted traffic in alignment with zero trust principles.
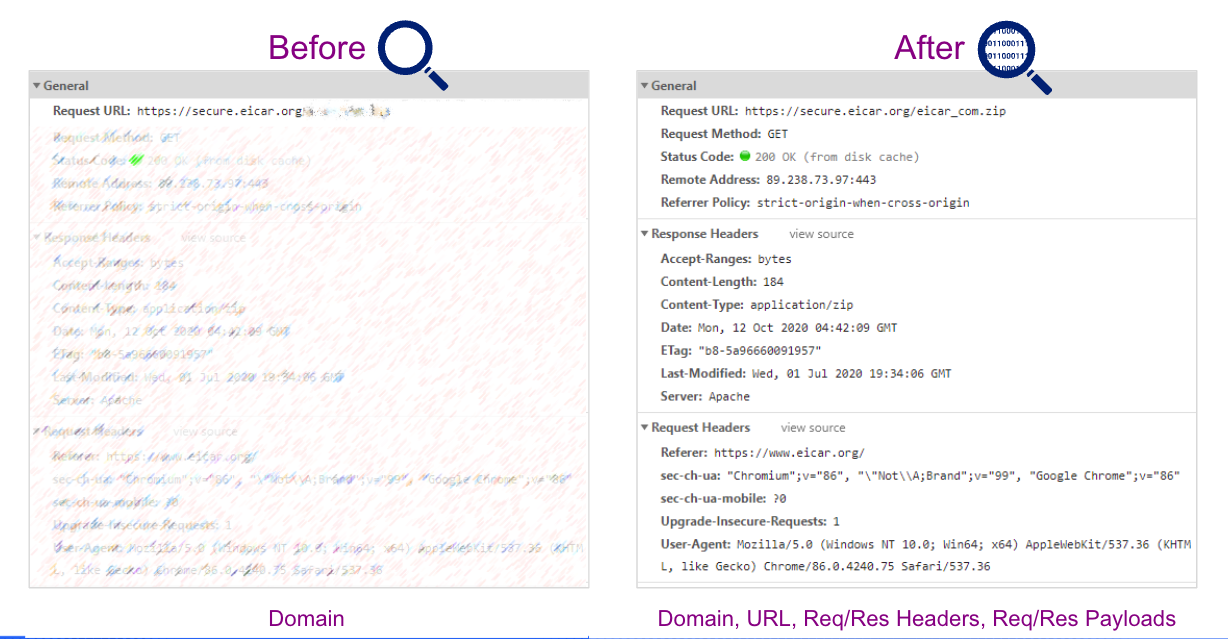
Figure 4: TLS inspection provides full visibility to block advanced threats
How to protect yourself
For defenders, the imperative is clear: all encrypted traffic must be fully inspected (see figure 4) to detect and stop cyberthreats before they cause damage. While we wait for governments, compliance frameworks, and other vendors to catch up with this reality, it will be up to defenders and leaders to raise the flag and champion initiatives to mitigate this common threat tactic. Zero trust strategies and architectures—in which you trust nobody and inspect and authenticate everything—are the most effective way to protect your organization from encrypted attacks and other advanced threats.
Zscaler’s tenets of zero trust align with the primary stages of the attack chain. Attacks start with reconnaissance and an initial compromise of an endpoint or asset exposed to the internet. Once inside, attackers perform lateral propagation, including reconnaissance and establishing a network foothold. Finally, attackers act to achieve their objectives, which often involve data exfiltration.
Your defenses should include controls for each of those stages:
- Minimize the attack surface by making internal apps invisible to the internet.
- Prevent compromise by using cloud native proxy architecture to inspect all traffic inline and at scale, enforcing consistent security policies.
- Stop lateral movement by connecting users directly to applications (rather than the network) to reduce the attack surface, and contain threats by using deception and workload segmentation.
- Stop data loss by inspecting all internet-bound traffic, including encrypted channels, to prevent data theft.
If you’re looking to minimize the risk of encrypted attacks for your organization, you should consider these recommendations as part of your adoption strategy:
- Use a cloud native, proxy-based architecture to decrypt, detect, and prevent threats in all encrypted traffic at scale.
- Leverage an AI-driven sandbox to quarantine unknown attacks and stop patient zero malware.
- Inspect all traffic, all the time, whether a user is at home, at headquarters, or on the go, to ensure everyone is consistently protected against encrypted threats.
- Terminate every connection to allow an inline proxy architecture to inspect all traffic, including encrypted traffic, in real-time—before it reaches its destination—to prevent ransomware, malware, and more.
- Protect data using granular context-based policies, verifying access requests and rights based on context.
- Eliminate the attack surface by connecting users directly to the apps and resources they need, never to networks.
Learn more
Download your copy of the full State of Encrypted Attacks 2022 Report to discover more insights and advice for managing encrypted attacks.




