 A detailed analysis was provided, here, on the new version of the Storm Worm making it's rounds this week. I went looking in our logs for HTTP POSTs to three and four character GIF and JPG files with relatively small request and response sizes (
A detailed analysis was provided, here, on the new version of the Storm Worm making it's rounds this week. I went looking in our logs for HTTP POSTs to three and four character GIF and JPG files with relatively small request and response sizes (
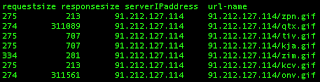
A small snippet of transactions:
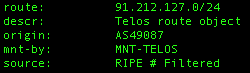
There is a ThreatExpert report on the related server / malware, which is identified as Email-Worm.Zhelatin (name used by Kaspersky and F-Secure for the Storm Worm). The infected hosts connect out to mail servers in attempts to mass-mail and infect others. Here is a list of some of the email servers that it connects to:
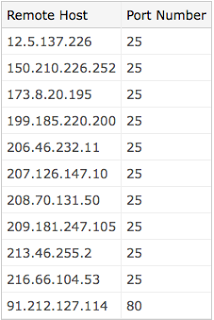
Keep an eye out for these types of transactions within your networks.
Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Storm Worm 2.0
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.




