Threats continue to evolve in their complexity and scale as cyber criminals regularly come up with new ideas and find ways to target their victims.
Modern information stealer families such as RedLine, RecordBreaker, ArkeiStealer, Vidar, Satacom, BatLoader are often sold through Malware-as-a-Service (MaaS) models and they continuously update with their varying initial attack vectors.
ThreatLabz discovered that threat actors are now distributing ArkeiStealer through Windows Installer binaries which masquerade as a trading application. The trading application is backdoored with the SmokeLoader downloader which further downloads an information stealer. In May 2021 in a similar campaign, ThreatLabz identified a fake TradingView website and backdoored TradingView application associated with the MineBridge RAT campaign [1].
Key Points
- ThreatLabz was able to flag malicious activity to an IP address based on C2 beaconing characteristics and a low domain and ASN reputation.
- It also discovered a recently registered domain spoofing the official TradingView website
- It was able to identify that the actual malware was embedded inside TradingView Desktop Application
- The actual malware and the C2 IP address flagged were identified as SmokeLoader and ArkeiStealer
Technical Analysis
ThreatLabz identified C2 beaconing events connected to an IP address, and the team started the threat hunting process. Following characteristics were essential in identifying and flagging the C2 beaconing activities:
- Frequent C2 beaconing
- Low domain reputation
- Newly Registered Domain
The process started with the Indicator of Attack (IoA) being flagged and the rest of the process revolved around identifying the TTP of the threat campaign.
The IP address “85.208.136.162” was flagged as an Indicator of Attack. The ThreatLabz Threat Intel team immediately validated the IP address as a SmokeLoader C2, as shown below in the following malware configuration in Figure 1.
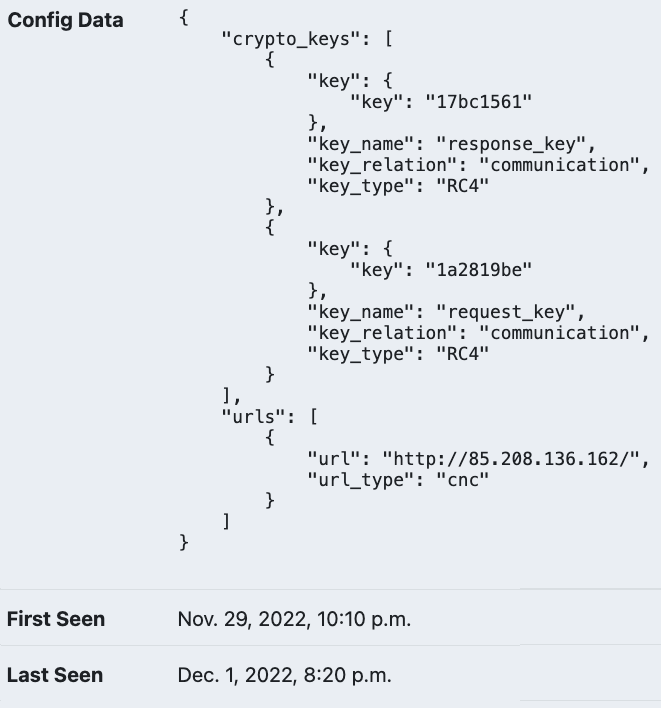
Figure 1: SmokeLoader Malware Configuration
During the threat hunting process, the ThreatLabz team analyzed network transactions in a time window around the trigger point to identify the end-to-end attack flow as shown in Figure 2.
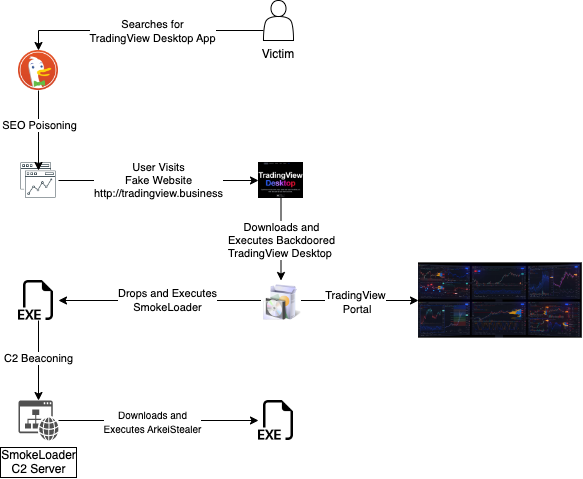
Figure 2: Complete end-to-end attack chain, used to deliver SmokeLoader and ArkeiStealer
While reconstructing the end-to-end attack chain, our team has identified 3 TradingView Desktop App download attempts from the following URL:
sxvlww.am.files.1drv.com/y4mqgb...ktaq/tradingvlev_x32_x64bit.zip?download&psid=1
Further analysis revealed the victim searching for the TradingView Desktop Application on the DuckDuckGo search engine, as shown below in Figure 3.
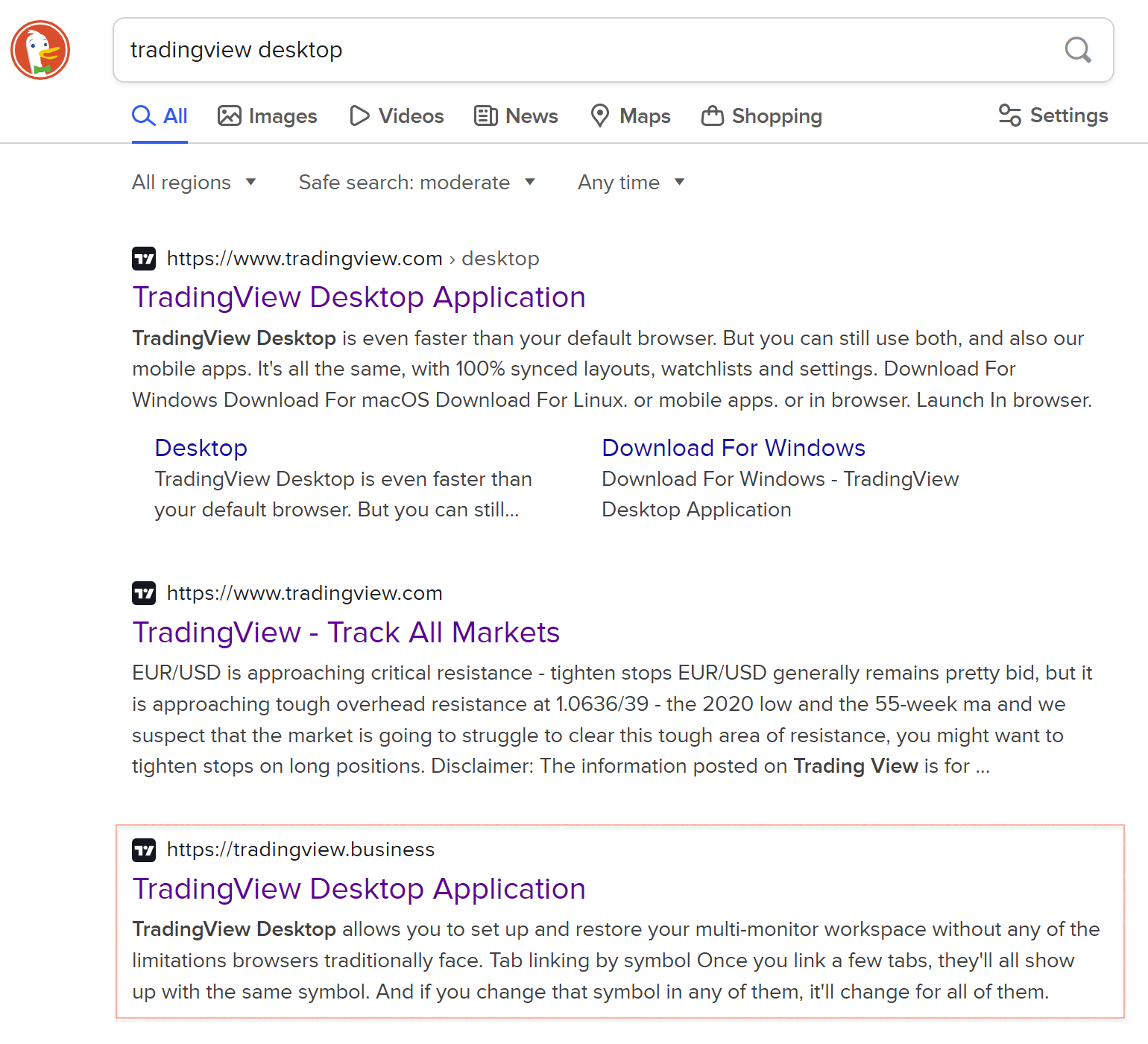
Figure 3: TradingView search results with SEO poisoned results
On October 6th, 2022, the threat actors registered the domain "tradingview[.]business", a look-alike of the legitimate website "tradingview[.]com". At first glance, “tradingview[.]business” looks almost identical to the legitimate website.
While the real website allows users to download clients for Windows, macOS and Linux platforms, the fake website only offers a Windows application. The download link for the malicious TradingView Desktop Windows application was placed on the homepage as shown in Figure 4.
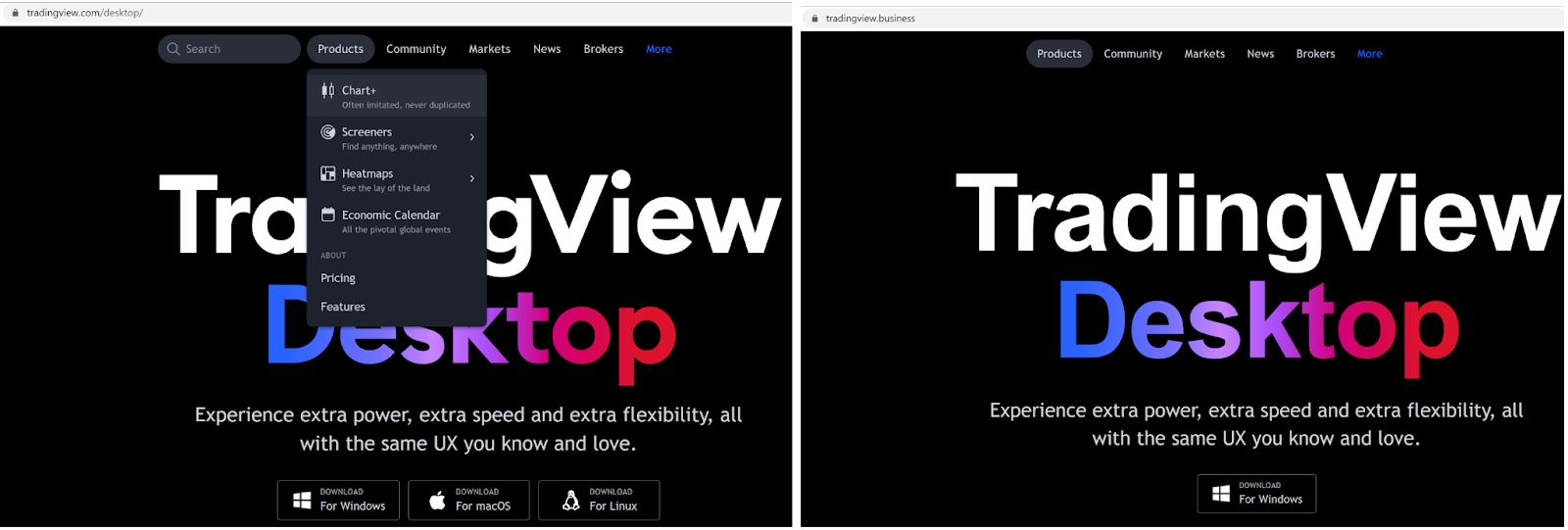
Figure 4: Legitimate vs. Fake TradingView website
The official and latest version of the TradingView Desktop Application was launched on October 25 2022. The malicious website, however, was registered prior to this on October 6 2022 in anticipation of the release; and the malicious TradingView Desktop Application was launched on October 31, 2022, shortly after the official release. This indicates that the threat actors are diligent in identifying and preparing for such opportunities ahead of time. In addition, they are extremely quick in developing and deploying the attack.
Comparing Whois data for both websites, we quickly validated the malicious intent of the fake website. While the original website’s Whois record is legitimate, the fake website redacts most of its registration details as shown in Figure 5.
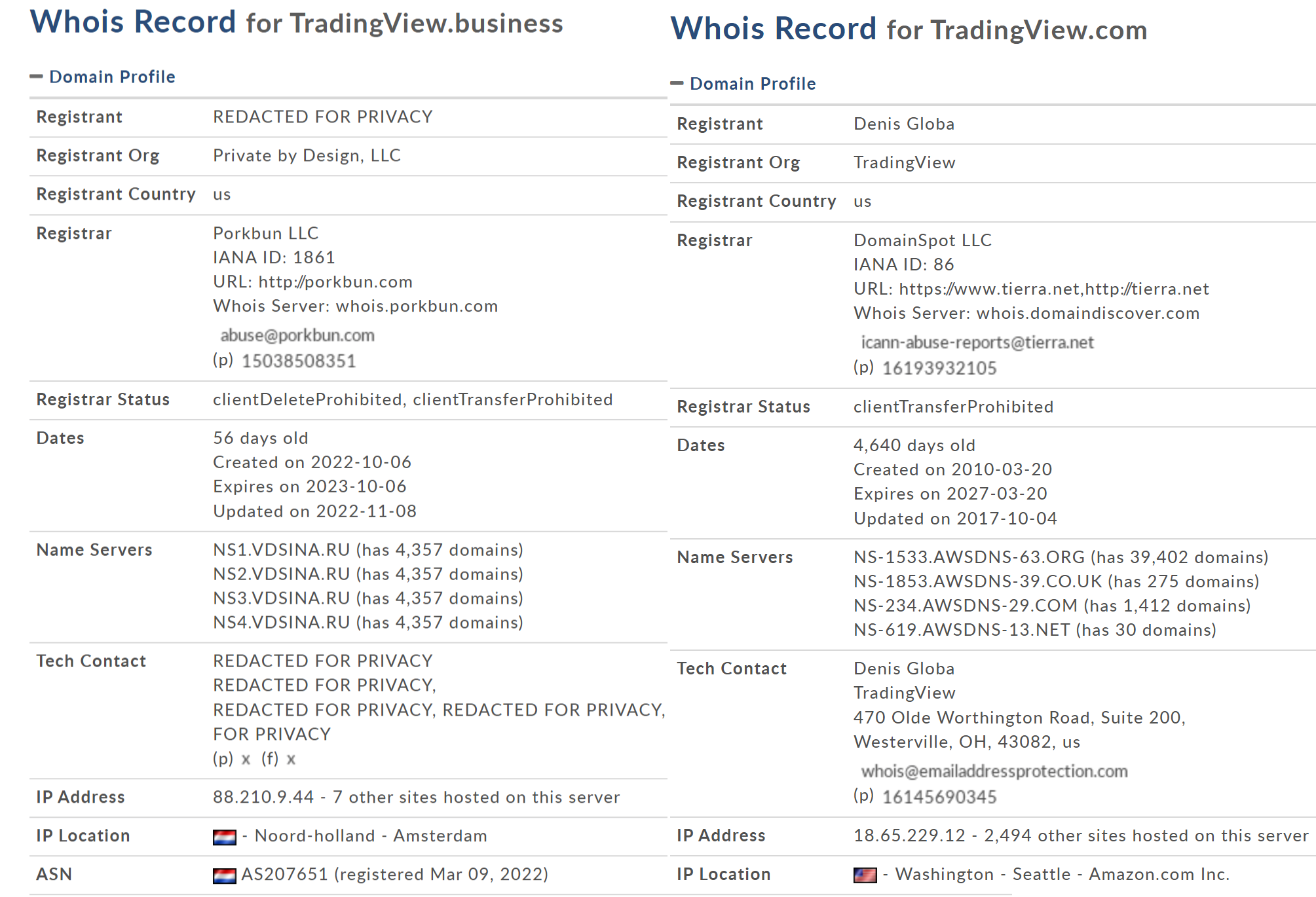
Figure 5: WHOIS records for the legitimate and fake TradingView domain
The download link (hxxps://tradingview[.]business/download.php) on the attacker-controlled domain leads to the download of a malicious Windows Installer from the following URL:
sxvlww[.]am[.]files[.]1drv[.]com/y4mqgbxmxiwuw8zm66u0rrrpceovu5hvhzmpooyrgnaaafadcqoiy-b3zjggi68kx_kt1c99vy4av6z5hznc6gumfg9hrnozccxmfiifzy6qf0rsqexsduxn06mtqzcccwb_iek8lvhu0wi-zupdr4sjpfack_tipf0psgzy5qw6ryzjdc8ny-zclsu716jxa7l1sss6r2jhl7lcdijpcktaq/tradingvlev_x32_x64bit.zip?download&psid=1
Note:
We noticed that the download URL responds with the malicious Windows Installer only if the user-agent string in the HTTP request headers corresponds to the Windows 10 operating system. Otherwise, it responds with HTTP 404 error.
Performing technical analysis, we inspected the malicious TradingView Windows Desktop Application with the following information:
Name: TradingVlev_x32_x64bit.exe MD5: 467d42eca35c0571c30d3f20700d9dff SHA1: e26512838e6ffb8af84743ae37821694cd380003 SHA256: 9abdfcea109db4763065fee6d3e87299f03f57dba0307c67ad10cd86f0f2acf3
The installer is an executable which masquerades as the TradingView Desktop Windows application and is digitally signed by AVG Technologies USA, LLC. The thumbprint of the digital signature is the following:
ThumbPrint: 63fb7fe4f171bd6dde774ae9365d91ac132616af CN = AVG Technologies USA, LLC OU = RE stapler cistodc O = AVG Technologies USA, LLC L = Newton S = North Carolina C = US
Here, we compare the legitimate and fake TradingView Desktop application signatures.
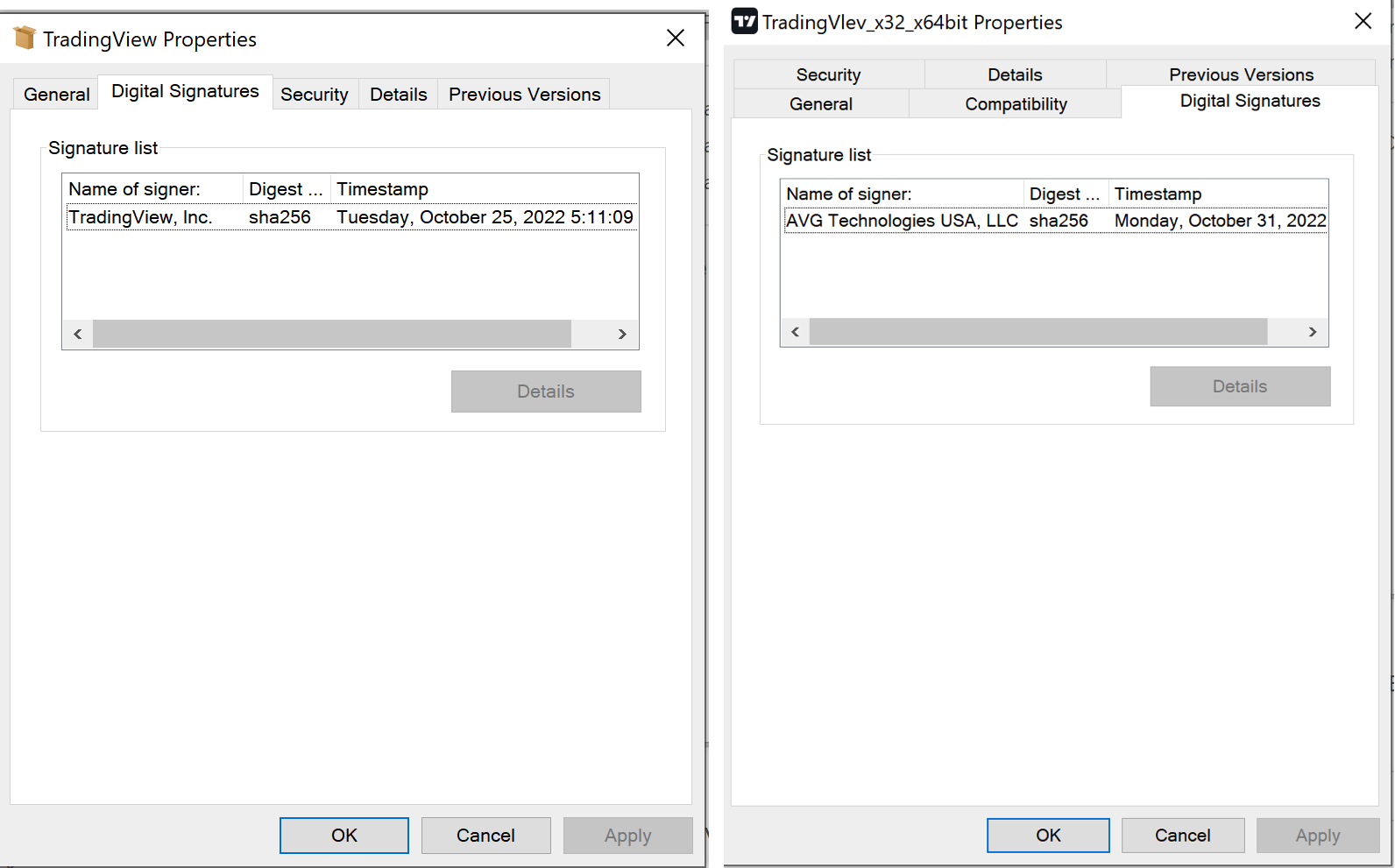
Figure 6: Legitimate vs. Fake TradingView Desktop applications
Upon execution, this installer shows a Graphical User Interface (GUI) which spoofs the TradingView application while it performs malicious activities in the background. It drops a SmokeLoader DLL named “Scintilla.DLL” in the same folder as the TradingView installation folder. The SmokeLoader DLL then creates a copy of itself with the name “bot.exe” on the user’s desktop.
SmokeLoader then immediately starts beaconing out to its C2 at the IP address “85.208.136.162” and receives a few download tasks, as shown below:
- 212[.]8[.]246[.]70/builds/still[.]exe - 16857afad0b6c40469e5d9d9b63a2927
- 212[.]8[.]246[.]70/builds/still[.]exe - 55552ed60bddd332eee8a23f0494174f
- 212[.]8[.]246[.]70/builds/installer[.]exe - 4d7f538bf21bf0c42fee87d28d3f3079
- 212[.]8[.]246[.]70/build/bot[.]exe - 0743250f8bb1a0baa01affcfd963d171
ZScaler ThreatLabz has identified all 4 payloads as ArkeiStealer. ArkeiStealer is an information stealer malware family that was first identified in May 2018. ArkeiStealer is a stealthy and flexible information stealer that is known to harvest confidential data from web browsers, cryptocurrency wallets, and search files for attacker-defined patterns. ArkeiStealer was later forked to create a new variant named Vidar Stealer.
This ArkeiStealer payload first obtains its configuration file from the C2 as shown below:
GET /1769 HTTP/1.1 Host: 95.217.31.208 HTTP/1.1 200 OK Server: nginx Date: Sat, 26 Nov 2022 15:21:14 GMT Content-Type: text/html; charset=UTF-8 Transfer-Encoding: chunked Connection: keep-alive 1,1,0,1,0,30e8151b350f29168e37e1eea06ed1b4,1,1,1,0,0,Default;%DOCUMENTS%\;*.txt;50;4;movies:music:mp3:exe;DESKTOP;%DESKTOP%\;*.txt;50;4;movies:music:mp3:exe;
The ArkeiStealer configuration carries multiple flags. It performs distinct malicious activities depending on the flags that are set in the configuration. The usage of a dynamic configuration provides flexibility to extend the malware’s capabilities at any stage of the campaign.
As shown below, ArkeiStealer immediately begins downloading well-known and legitimate DLLs in a ZIP bundle that are required to fully execute its tasks.
GET /547345733334.zip HTTP/1.1 Host: 95.217.31.208 Cache-Control: no-cache HTTP/1.1 200 OK Server: nginx Date: Sat, 26 Nov 2022 15:21:14 GMT Content-Type: application/zip Content-Length: 2685679 Last-Modified: Mon, 12 Sep 2022 13:14:59 GMT Connection: keep-alive ETag: "631f30d3-28faef" Accept-Ranges: bytes
These DLLs are typically used by ArkeiStealer to read information from web browsers. ArkeiStealer downloads and stores below DLLs into the %\ProgramData\% directory.
|
Name |
Description |
|
sqlite3.dll |
SQLite Database Management DLL |
|
freebl3.dll |
Freebl Network Security Service DLL for Mozilla Firefox |
|
mozglue.dll |
Browser Library for Mozilla Firefox |
|
nss3.dll |
Network System Service DLL for Mozilla Firefox |
|
softokn3.dll |
Part of Network Security Service for Mozilla Firefox |
|
msvcp140.dll |
MS Visual Studio component |
|
vcruntime140.dll |
Runtime Library for Visual Studio |
Conclusions
Information stealing is extremely rewarding for threat actors especially when storing financial and personal information in web browsers is becoming common. Use of legitimate DLL components to perform browser information enumeration and use of dynamic configuration allows ArkeiStealer threat actors to tailor their operation and choose the information they want to steal from the victim.
At Zscaler, ThreatLabz team works closely with security research, security engineering and ML scientists to develop tools that augment and empower security teams in tackling complex and evasive threats. After successfully detecting C2 traffic to a malicious server, it was further passed to the Threat Hunting team for end-to-end atack chain construction. The team successfully created an end-to-end attack chain identifying all infection stages which consisted of a DuckDuckGo search, a fake TradingView website, a backdoored TradingView Windows application download, SmokeLoader C2 beaconing and the ArkeiStealer download and C2 beaconing.
ZScaler Cloud Sandbox Report
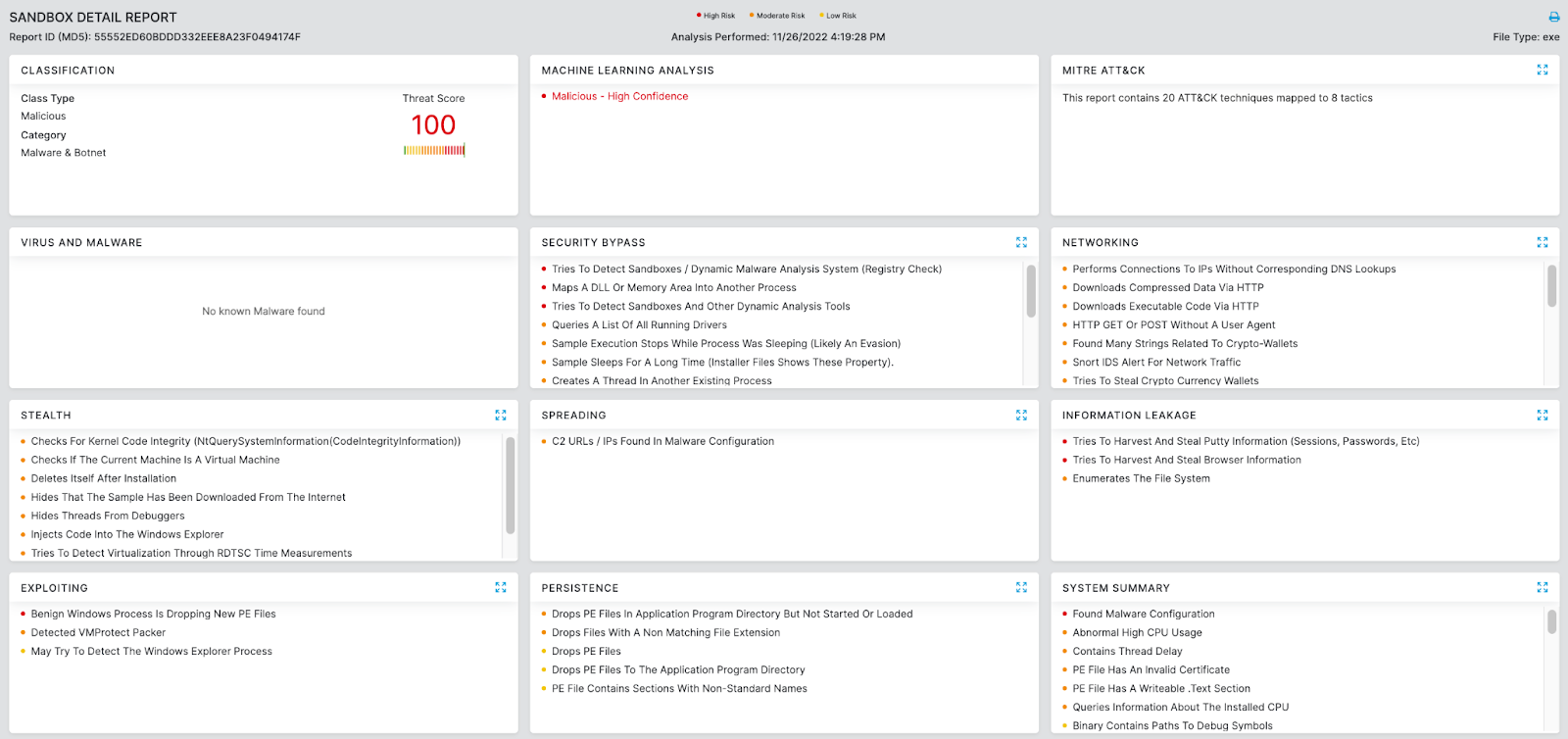
Figure 7: ArkeiStealer Cloud Sandbox Report
In addition to cloud sandbox detections, Zscaler’s multilayered cloud security platform detects indicators at various levels. The Machine Learning Threat Detection Model assists in identifying emerging threats, automatically blocking those with the highest risk scores, and ranking suspicious candidates for further review.
MITRE ATT&CK TTP Mapping
|
ID |
Tactic |
Technique |
|
T1203 |
Exploitation for Client Execution |
Benign windows process is dropping new PE files |
|
T1574.002 |
DLL Side-Loading |
Tries to load missing DLLs |
|
T1055 |
Privilege Escalation |
Injects code into the Windows Explorer |
|
T1036 |
Defense Evasion |
Creates files inside the user directory |
|
T1070.004 |
File Deletion |
Deletes itself after installation |
|
T1497 |
Virtualization/Sandbox Evasion |
Checks for kernel code integrity |
|
T1564.001 |
Hidden Files and Directories |
Hides that the sample has been downloaded from the Internet |
|
T1010 |
Discovery |
Application Window Discovery |
|
T1057 |
Process Discovery |
Verifies the name of parent process |
|
T1082 |
System Information Discovery |
Gathers system OS version info |
|
T1518.001 |
Security Software Discovery |
Checks if the current machine is a virtual machine Checks if the current process is being debugged |
|
T1071 |
Application Layer Protocol: Web protocol |
Posts data to web server C2 URLs/IPs found in malware configuration |
|
T1095 |
Non-Application Layer Protocol: |
Tries to download or post to a non-existing http route |
|
T1105 |
Ingress Tool Transfer |
Some HTTP requests failed with 404. Part of communication protocol |
Indicators of Compromise
|
Indicators |
Description |
|
TradingVlev_x32_x64bit.zip |
Fake TradingView Desktop Application Download |
|
fc99ea424df48f2b661219b71f33b979 |
MD5 of Fake TradingView Desktop Application |
|
1a70718eefa2aef42f4b09577aea7b43ff874e02 |
SHA1 of Fake TradingView Desktop Application |
|
f4c166dddefd29eb457d0a7b426928b1123626c6c1568bc998440dac72a816b7 |
SHA256 of Fake TradingView Desktop Application |
|
TradingVlev_x32_x64bit.exe |
Fake TradingView Desktop Application |
|
467d42eca35c0571c30d3f20700d9dff |
MD5 of Fake TradingView Desktop Application |
|
e26512838e6ffb8af84743ae37821694cd380003 |
SHA1 of Fake TradingView Desktop Application |
|
9abdfcea109db4763065fee6d3e87299f03f57dba0307c67ad10cd86f0f2acf3 |
SHA256 of Fake TradingView Desktop Application |
|
85.208.136.162 |
SmokeLoader C2 |
|
sxvlww.am.files.1drv.com |
Fake TradingView Application Distribution Domain |
|
tradingview.business |
Fake TradingView look-alike website |
|
hxxps://tradingview[.]business/download.php |
Fake TradingView download URL |
|
212[.]8[.]246[.]70/builds/still[.]exe |
ArkeiStealer download URL |
|
212[.]8[.]246[.]70/builds/installer[.]exe |
ArkeiStealer download URL |
|
212[.]8[.]246[.]70/builds/bot[.]exe |
ArkeiStealer download URL |
|
4d7f538bf21bf0c42fee87d28d3f3079 |
ArkeiStealer payload |
|
55552ed60bddd332eee8a23f0494174f |
ArkeiStealer payload |
|
16857afad0b6c40469e5d9d9b63a2927 |
ArkeiStealer payload |
|
0743250f8bb1a0baa01affcfd963d171 |
ArkeiStealer payload |
References
[1] “Demystifying the full attack chain of MineBridge RAT”, https://www.zscaler.com/blogs/security-research/demystifying-full-attack-chain-minebridge-rat




