Splunk and Zscaler deliver a powerful, simple, and integrated zero trust solution that provides unmatched security for the cloud-first enterprise.
WHY ZSCALER + SPLUNK
Hybrid workforce risk
Cloud-driven hybrid work can significantly improve productivity, but trying to keep cloud environments secure using traditional security can create blind spots in visibility and gaps in protection, both of which increase business risk. Thus, a zero trust architecture is needed to securely adopt the cloud for hybrid work.

BENEFITS
Securing the enterprise with improved visibility and response
Reduce risk
Zscaler logs are readily formatted for Splunk, enabling security teams to search and identify emerging threats.
Improved response
Integration with Splunk SOAR enables automated case enrichment and threat response.
Simplified operations
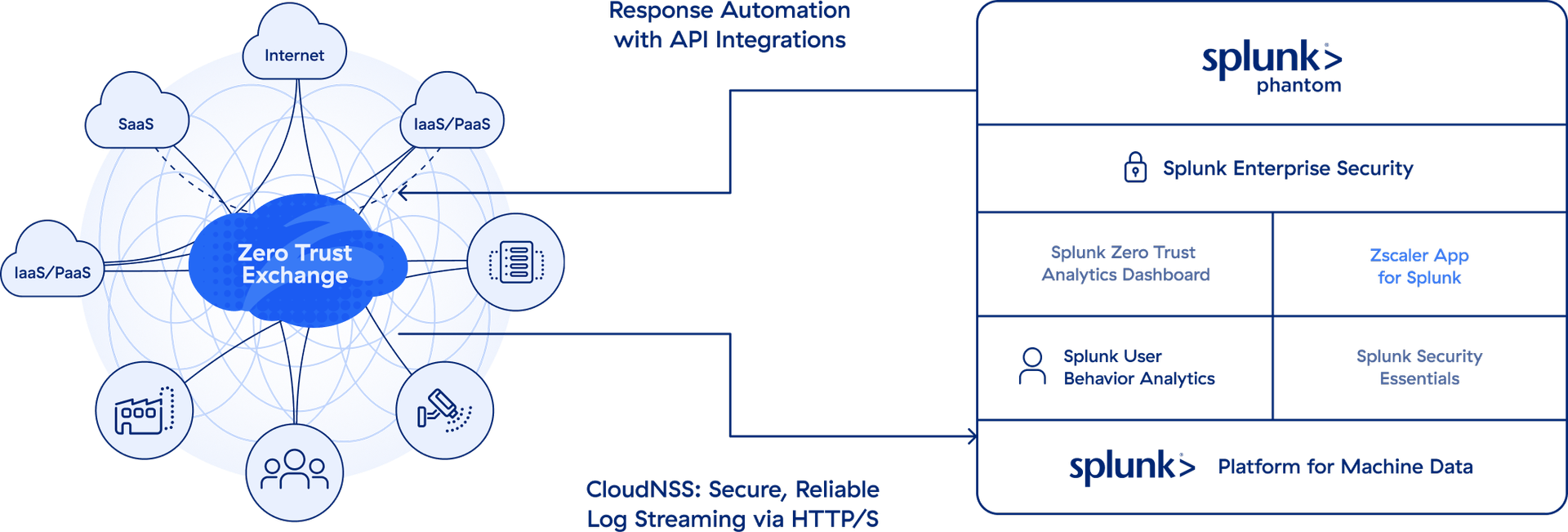
Splunk Cloud and Zscaler CloudNSS integration eliminates the need to manage your logging pipeline, so security teams can focus on the data.
HOW IT WORKS
Insights from Zscaler Telemetry
Simplified connectivity
Zscaler CloudNSS enables secure connectivity to Splunk Cloud with no infrastructure to manage.
Actionable data
Zscaler App for Splunk gives insights into Zscaler telemetry with dashboards and prebuilt search queries.
Faster response
Integration with Splunk SOAR using APIs allows otherwise time consuming tasks to be completed easily, allowing analysts to focus on emerging threats.
Experience the power of the Zero Trust Exchange
ENLARGE
Take the next step
Zero trust and analytics
Learn more about how Zscaler and Splunk can help you secure your enterprise.