Deploy smarter defenses at every attack stage
To protect your data and your bottom line, you need an approach that does what legacy anti-malware and other tools can’t. A comprehensive, cloud native zero trust security architecture empowers you to:
Eliminate the attack surface
by ensuring users, networks, and apps are never exposed to the internet
Prevent compromise
including zero-day threats, with full TLS/SSL inspection and instantly shared protections
Stop lateral movement
by connecting authenticated users and devices directly to apps, never your network
Block data exfiltration
with end-to-end security for data in motion and at rest—even encrypted data
THE PROBLEM
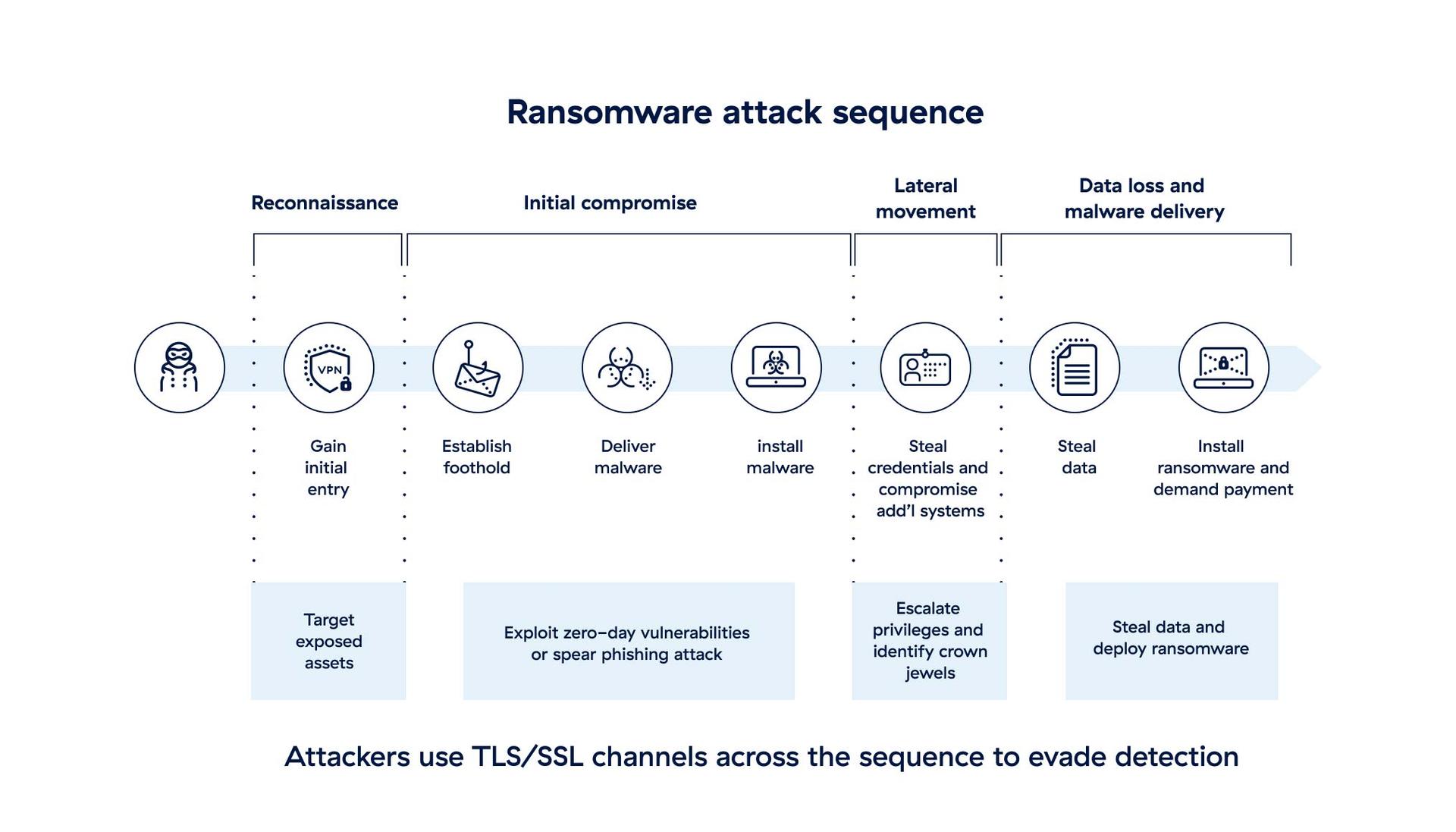
Ransomware threats are becoming more frequent, expensive, and evasive
57.81%
ThreatLabz
US$75M
ThreatLabz
87.2%
ThreatLabz
Legacy security architectures are ineffective
Next-generation firewalls, VPNs, and point products like anti-malware introduce blind spots, complexity, and high costs. It becomes cost-prohibitive to inspect encrypted traffic for threats, leaving you vulnerable to attack.
Meanwhile, legacy hub-and-spoke network architectures leave the doors wide open for attackers to move laterally. Once inside the network, attackers can freely infect other systems and look for sensitive data to encrypt and/or steal, fueling their ransom demands.
Ransomware attacks surge 146% year over year
The ThreatLabz Ransomware Report reveals what’s driving the spike—from top families to evolving tactics and extortion-focused attacks.
Solution Overview
Defend your data across the attack life cycle
Take back the advantage at every turn with a globally proven, cloud-delivered zero trust architecture. Make your users and apps accessible only to authorized users or devices and stop ransomware attacks before they even start. Attackers can't see your network or any of its contents, so there's nothing for them to discover, exploit, or infect.
Eliminate the attack surface
Make all entry points invisible to attackers. Zero trust architecture never exposes users, networks, or apps to the internet.
Prevent initial compromise
Inspect 100% of inbound and outbound connections. Threats are blocked before they can cause damage.
Stop lateral movement
Broker 1:1 connections between users, workloads, and applications. The network remains invisible to attackers.
Block data exfiltration
Inspect all traffic in real time and at cloud scale. Sensitive data never leaves the network on an untrusted connection.

Solution Details
Prevent compromise

Inspect 100% of encrypted traffic in real time, gaining visibility that powers advanced data protection and dynamic access control.
Continuously detect and block new threats as they emerge with cloud-based, AI/ML-driven, inline sandboxing.
Stay safe from patient zero infections and emerging threats discovered anywhere across the world's largest security cloud.
Deliver fast, secure access for all users without the risks and poor user experiences of legacy VPNs and VDI.
Protect your users and data from web-borne threats, in any location and on any device, including BYOD.
Fully inspect all traffic and content with an inline cloud proxy architecture, delivered from the cloud at infinite scale.
Protect all users, locations, and clouds with a cloud native firewall that adapts to the needs and risks of distributed environments.
Prevent connections between your workloads and attackers' command-and-control servers, blocking data breaches and callbacks.
Prevent lateral movement

Securely connect users anywhere to applications hosted in any location, with no access to adjacent applications or systems.
Secure cloud workload communications across hybrid and multicloud environments, such as AWS and Azure.
Proactively lure, detect, and intercept sophisticated active attackers with integrated deception technology that employs decoys and false user paths.
Block data exfiltration

Inspect 100% of TLS/SSL-encrypted traffic end to end through a cloud-based proxy architecture.
Enforce consistent, unified security for data in motion across SaaS and public cloud applications.
Secure cloud data at rest from risky misconfigurations, and data on endpoints from risky user behaviors.
FAQ
Ransomware is a type of malware that encrypts files and/or steals data, after which attackers demand a ransom. Victims usually can't recover their data until they pay the ransom—and they may even lose the data permanently. Payment demanded for a decryption key can range from hundreds to millions of dollars. Learn more.
In a double extortion attack, threat actors exfiltrate a victim’s data in addition to encrypting it. This gives the attacker more leverage to make ransom demands, compared to traditional attacks that stop at encryption. Learn more.
Lateral movement is how threat actors access other assets on a network after the initial compromise. Using stolen credentials or other means of privilege escalation, they hunt for sensitive data to encrypt or steal. Legacy security solutions don't effectively detect lateral movement, instead seeing it as allowed network traffic. Learn more.










