/ What Is Universal ZTNA?
What Is Universal ZTNA?
Universal zero trust network access (UZTNA) is the use of ZTNA for on-premises and remote users, with no distinction made as to the user’s location. With universal ZTNA users are granted secure access based on the principle of least privilege whether they’re working in the office, at home, or on the road. UZTNA can serve as a conduit for digital transformation, giving organizations the best possible framework for zero trust initiatives.

Understanding Universal ZTNA: A Modern Approach to Secure Access
Key Takeaways
Universal ZTNA (UZTNA) is a cloud native, software-defined security framework that applies zero trust principles to grant granular, context-based access to private applications, SaaS, and networks from any location, eliminating the need for VPNs and significantly reducing the attack surface. It ensures consistent security, seamless user experiences, and effortless scalability for hybrid workforces by connecting users directly to applications, not the network.
Top Reasons to Consider Universal ZTNA
Now more than ever, organizations are discovering the benefits a universal ZTNA model can provide. Here are some of the biggest reasons why companies are making the switch:
- No need for legacy appliances: UZTNA allows organizations to rid themselves of legacy remote access appliances, such as VPNs, and leverage a 100% software-based access control solution.
- Seamless user experiences: With UZTNA, user traffic isn’t backhauled through the data center. Instead, users get fast, direct access to the desired application.
- Consistent security: UZTNA ensures that the same zero trust security policies are applied to employees whether they’re working in or out of the office.
- Effortless scale: A cloud UZTNA service makes scaling capacity easy. An organization just leverages additional licenses.
- Fast deployment: Unlike other solutions that can take weeks to months to deploy, UZTNA can be deployed from anywhere in a matter of days.
ZTNA vs. Universal ZTNA: Key Distinctions
In today’s IT and security vernacular, many vendors claim to offer “zero trust network access,” but this typically ends up being a rigid, on-premises network security deployment with legacy network microsegmentation. While this technology may be able to protect in-office users based on a handful of loosely integrated zero trust network access controls, a proper universal ZTNA solution is more akin to a security fabric, delivering zero trust security to all users wherever they’re working.
This is because a universal ZTNA solution is born in the cloud, typically built on a secure access service edge (SASE) or security service edge (SSE) framework. With universal ZTNA, users are granted access based on the principle of least privilege wherever they work; whether it be in an office, at home, in a coffee shop, or anywhere else with an internet connection.
Secure connectivity to networks, SaaS, and applications from any location is simply not attainable with an on-premises, non-universal framework. Moreover, if a solution claims to deliver zero trust security through on-premises appliances such as firewalls, then it’s not really a zero trust solution, and it’s certainly not a universal ZTNA solution. This is because many of these legacy technologies will grant access based solely on authentication rather than context, device posture, and/or location.
What’s more, many of these technologies use a passthrough architecture, which allows traffic into the network before it’s inspected—this inherently goes against zero trust principles. Universal ZTNA grants secure network, SaaS, and application access, regardless of where users work from without granting implicit trust, and this unique capability comes from a ZTNA that’s cloud native.
Universal ZTNA vs. VPN: Which Outperforms for the Modern Workforce?
Among the most popular legacy security solutions in use today, VPNs are meant to simplify access management by allowing end users to securely access a network, and therefore corporate resources, by way of a designated tunnel, usually through single sign-on (SSO).
For many years, VPNs worked well for users who needed to work remotely for a day or two. However, as the world saw more and more long-term remote workers—leading, eventually, to work-from-anywhere—a lack of scalability alongside high costs and maintenance requirements made VPNs ineffective. What’s more, rapid adoption of the public cloud meant that it not only became more difficult to apply security policies to these remote workers, but also hurt the user experience.
The main problem with VPNs, however, is the attack surface they create. Any user or entity with the right SSO credentials can log on to a VPN and move laterally throughout the network, giving them access to all the network, endpoints, and data the VPN was meant to protect.
Universal ZTNA secures user access by granting it on the principle of least privilege. Rather than trusting on the basis of correct credentials, zero trust only grants authentication only under the correct context—that is, when the user, identity, device, and location all match up.
Furthermore, universal ZTNA provides granular access to resources rather than network access. Users are connected directly and securely to the applications and data they need, removing the possibility of lateral movement by malicious users. Plus, because user connections are direct, experiences are vastly improved when leveraging a UZTNA framework.
Universal ZTNA: Implementing Zero Trust Principles
Universal ZTNA is about more than user identity, segmentation, and secure access. It's a strategy upon which to build a cybersecurity ecosystem. At its core are three tenets:
- Terminate every connection: Technologies like firewalls use a “passthrough” approach, inspecting files as they are delivered. If a malicious file is detected, alerts are often too late. An effective UZTNA solution terminates every connection to allow an inline proxy architecture to inspect all traffic, including encrypted traffic, in real time—before it reaches its destination—to prevent ransomware, malware, and more.
- Protect data using granular context-based policies: Zero trust policies verify access requests and rights based on context, including user identity, device, location, type of content, and the application being requested. Policies are adaptive, so user access privileges are continually reassessed as context changes.
- Reduce risk by eliminating the attack surface: With UZTNA, users connect directly to the apps and resources they need, never to networks. Direct user-to-app and app-to-app connections eliminate the risk of lateral movement and prevent compromised devices from infecting other resources. Plus, users and apps are invisible to the internet, so they can’t be discovered or attacked.
Universal ZTNA with Zscaler
We’re proud to offer Zscaler Private Access™, the world’s most deployed ZTNA platform, built on the unique Zscaler zero trust architecture (ZTA). Cloud-based ZPA applies the principles of least privilege to give users secure, direct connections to private applications while eliminating unauthorized access and lateral movement. As a cloud native service, ZPA can be deployed in hours to replace legacy VPNs and remote access tools with a holistic zero trust platform.
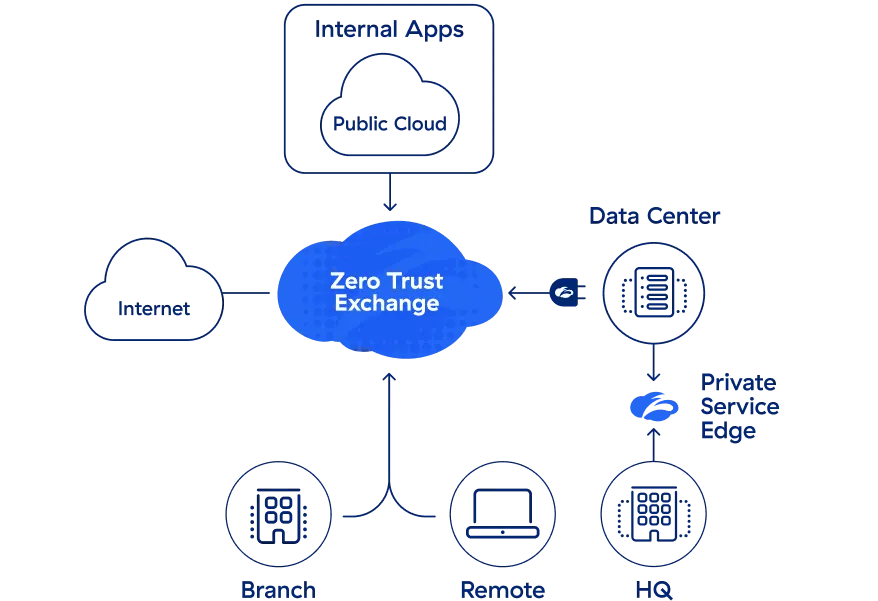
Zscaler Private Access delivers:
- Peerless security, beyond legacy VPNs and firewalls: Users connect directly to apps, not the network, minimizing the attack surface and eliminating lateral movement.
- The end of private app compromise: First-of-its-kind app protection, with inline traffic inspection and threat prevention, integrated deception, and threat isolation minimizes the risk of compromised users.
- Superior productivity for today's hybrid workforce: Lightning-fast secure access to private apps extends seamlessly across remote users, HQ, branch offices, and third-party partners.
- Unified, universal ZTNA for users, workloads, and devices: Employees and partners can securely connect to private apps, services, and OT/IoT devices with the most comprehensive ZTNA platform.
Suggested Resources
FAQ
Frequently Asked Questions
Universal ZTNA doesn’t just help businesses become more flexible—it also greatly improves their overall security postures by delivering:
- An invisible infrastructure: With UZTNA, users can access applications without having to be connected to the corporate network.
- More control and visibility: UZTNA gives IT the power to easily manage their solution with a centralized admin portal with granular controls.
- App segmentation, made simple: Since ZTNA isn’t tied to the network, organizations can segment access down to individual applications rather than having to perform complex network segmentation.
Universal ZTNA begins with the assumption that everything on the network is hostile or compromised, and access to an application is only granted after user identity, device posture, and business context have been verified and policy checks enforced. In this model, all traffic must be logged and inspected—requiring a degree of visibility that traditional security controls can’t achieve.
Universal ZTNA minimizes your organization’s attack surface, prevents lateral movement of threats, and lowers the risk of a breach. It’s best implemented with a proxy-based architecture that connects users directly to applications instead of the network, enabling further controls to be applied before connections are permitted or blocked.
Universal ZTNA has many cloud security use cases. Typically, organizations will first use universal ZTNA:
- As a VPN alternative
- To secure multicloud access
- To reduce third-party risk
- To accelerate M&A Integration
A Universal Zero Trust Network Access (ZTNA) solution provides secure, adaptive access to applications and resources without relying on traditional perimeter-based security models. Its primary goal is to enforce granular, context-aware access based on Zero Trust principles. Key features include:
- Zero Trust Principles
- Adaptive Access Controls
- Application-Level Access
- Cloud-Native Architecture
- Secure Remote Access
- Integration with Threat Detection
Universal Zero Trust Network Access (ZTNA) is well-suited for hybrid and remote workforces because it provides secure, seamless access to applications and resources from any location. Its adaptability stems from its ability to blend flexibility with strong security, tailored to modern, dynamic work environments. Universal ZTNA adapts to hybrid and remote workforces by providing secure, efficient, and scalable access while aligning with the flexibility modern work environments require.