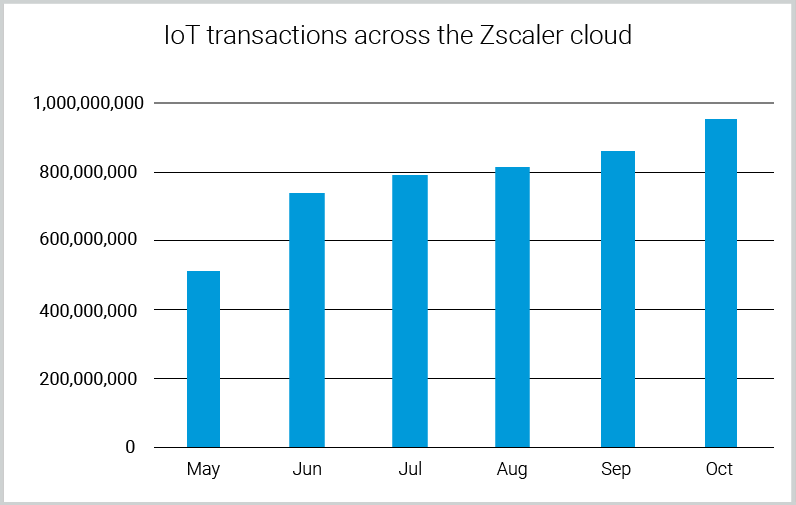
More than you think. You've probably heard this quote repeatedly in the past few years: “Gartner predicts that the number of IoT devices used worldwide will reach 20.4 billion by 2020.” Indeed, enterprises across all industries are experiencing an explosion of sanctioned and unsanctioned (shadow) IoT devices in their networks, as exhibited in the numbers Zscaler ThreatLabZ researchers shared in their report, IoT in the Enterprise: an analysis of traffic and threats last spring. Back then, we reported that our cloud platform had detected approximately 56 million transactions originating from IoT in the month of March. Today, with the extension of our IoT detection capabilities, we are approaching a huge milestone: the detection of 1 billion monthly IoT transactions.
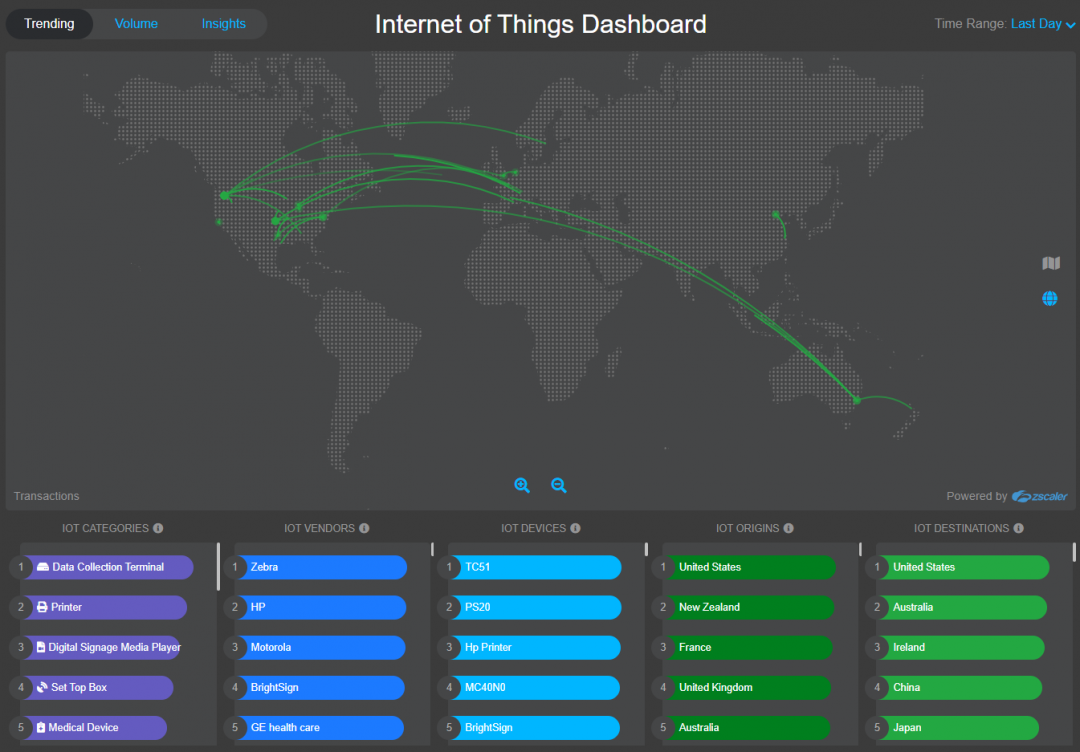
As the trusted internet gateway for thousands of global enterprises, the Zscaler cloud security platform has unparalleled visibility into internet-destined traffic generated by some of the world's largest and most diverse corporate networks—regardless of whether that traffic is originating on a common laptop or handheld device or whether it’s from an IoT device communicating with its mothership for configuration, remote control, and updates. The Zscaler cloud processes IoT traffic, acting as the network policy and security enforcement layer, just as it does for user-held devices.
Gain visibility into IoT traffic and trends
Many organizations are aware of the presence of a few devices, such as IP cameras and photocopiers, but are often surprised to find out how much traffic is being generated by devices they weren’t aware that were on their network.
Wouldn't it be great if you had live visibility into IoT traffic at the level of the Zscaler cloud? In recent months, the ThreatLabZ team has been increasing its automated detection capabilities to almost two dozen of the most popular IoT product families from 250 manufacturers to help to bring you exactly that kind of visibility.
We are pleased to announce the latest addition to our global internet insights dashboard gallery: the interactive Internet of Things Dashboard. In this live dashboard, we offer you a window into the traffic trends of the most popular IoT product families as seen on a daily basis across the thousands of Zscaler-protected enterprises.
About the Internet of Things Dashboard
This dashboard is essentially a suite of three tools, updated daily, in which each illustrates a different aspect of the IoT traffic we see across our cloud. These interactive illustrations include the trending device families/vendors/models and the respective geolocations of their source and destination servers (by web transactions); the top devices and source geolocations (by bytes transferred); and the top categories and models (by device count).
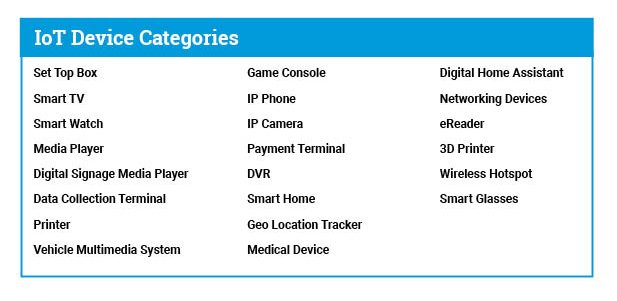
The device types we are detecting include:
Highlights of current enterprise IoT traffic:
-
1,500+ organizations and 10,000+ Zscaler-protected locations (branch offices, HQs) had at least one IoT device
-
The five most chatty IoT vendors across our cloud are: Zebra, HP, Motorola, Bright Sign, and Roku
-
The five most chatty IoT categories across our cloud are: data collection terminals, printers, set top boxes, digital signage media players, and medical devices
-
The five most chatty gaming consoles across our cloud are: PlayStation 4, PlayStation Vita, Nintendo Switch, Nintendo Wii U, and Nintendo NX
Interested in discovering more insights? Visit the live dashboard page to uncover more.
Why IoT traffic matters in the enterprise
IoT devices continue to be an easy target for cyberattacks. Printers, IP cameras, and smart TVs are just a few examples of devices that come with Ethernet and internet connectivity for remote monitoring, administration, and update services. But this connectivity also introduces risks, such as data leakage, denial of service, and malware infiltration vectors. Most devices today lack even basic security mechanisms, and the vast majority of devices, especially those designed for low-cost and mass consumer markets, use obsolete and insecure software (OS and applications), go through minimal to no vulnerability scanning, and lack the ability or vendor motivation to receive any software or security updates.
While analyzing the IoT traffic devices in the Zscaler cloud, we indeed observed that some of the devices are not following security best practices by using:
-
Plain-text HTTP authentication or communication to a server for firmware or package updates
-
Outdated libraries
-
Weak default credentials
Incredibly, we saw that approximately 60% of IoT transactions are occurring on clear text HTTP, making them easy targets for man-in-the-middle (MiTM) attacks. Additionally, we detected that approximately 1.45% of all device transactions are misbehaving and, as a result, are being blocked or cautioned due to corporate-specific internet access policies enforced by Zscaler.
How Zscaler protects customers (and how you can protect yourself)
To protect our customers from IoT risks, ThreatLabZ actively blocks IoT attacks in our cloud and tracks them in the wild, continually adding new detections for malware and advanced threats, such as the Mirai botnet and RIFT backdoor RAT. Earlier this year, we shared A sneak peek into recent IoT attacks and we frequently write blogs and analyses that cover the IoT activity we see.
As your IoT footprint expands, there are some things that you can do to reduce risk:
-
Search your Zscaler web logs for IoT threat names published on the Zscaler Threat Library, such as IoT.Trojan.Mirai, IoT.Backdoor.RIFT, to identify compromised clients and IP addresses that require remediation.
-
Change default credentials. As employees bring in devices, encourage them to be sure their passwords are strong and their firmware is always up to date.
-
Install IoT devices on isolated networks (to prevent lateral movement), with restrictions on inbound and outbound network traffic.
-
Restrict access to the IoT device as much as possible from external networks. Block unnecessary ports from external access.
-
Apply regular security and firmware updates to IoT devices, in addition to securing the network traffic.
-
Finally, deploy a solution to gain visibility into the shadow IoT devices that are already sitting inside the network and ensure above safeguards.
If you haven't already checked it out, take our new IoT dashboard for a drive.
I'd like to thank Deepen Desai and Viral Gandhi from the ThreatLabZ team for their collaboration on this project.
Lidor Pergament is a Senior Product Manager at Zscaler