Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Zscaler Announces Intent to Acquire Airgap Networks to Extend Zero Trust SASE Leadership and Eliminate the Need for Firewall-based Segmentation
Overview
Today, Zscaler has announced the next major step in its Zero Trust SASE leadership by signing an agreement to acquire Airgap Networks, which provides agentless segmentation for enterprise IT and OT environments. With this acquisition, Zscaler will combine its Zero Trust SD-WAN with Airgap to extend the Zero Trust Exchange to protect east-west traffic in branch offices, campuses, factories and plants with critical OT infrastructure. This next step in our SASE leadership will eliminate the need for east-west firewalls, NACs and microsegmentation and deliver greater operational simplicity.
Controlling lateral movement is the cornerstone of Zero Trust
To understand why today’s news is important, let’s reflect on challenges that organizations face in combating attackers. Adversaries are becoming faster and ever more effective at evading even the most sophisticated security controls with AI-enhanced social engineering and identity-based attacks. Once they compromise an organization, they then move laterally to get to sensitive data or critical resources. Once the targets or crown jewels (typically high value data) have been identified and reached, the goal is to exfiltrate the data as quickly and quietly as possible.
While Zero Trust cannot be achieved without a holistic strategy that addresses every stage of this typical cyber attack chain - also known as a defense-in-depth approach - restricting lateral movement, and proper containment of the adversary once your organization has been compromised, is where real Zero Trust technologies must prove their worth. To date, the primary vehicle for addressing lateral movement on local area networks has been network-based segmentation and microsegmentation.
How traditional segmentation and firewalls have fallen short
Segmentation has been carried out with aging, IP-centric networking technologies like NAC and east-west firewalls, managed through complex constructs like ACLs based on MAC, IP addresses and VLANs. This complexity places considerable strain on network operations teams forced to write, maintain and update countless ACLs or internal firewall rules while addressing the inevitable misconfigurations that break business critical applications or leave gaps in segmentation coverage. The complexity that east-west firewalls bring means most segmentation projects are never fully implemented and, even those with partial completion quickly experience segmentation policy drift as workloads and applications move and organizations’ environments change.
The significance of a ‘network of one’
Why is Airgap’s technology so compelling? Their agentless, identity-based approach to segmentation is a total re-think of the complexity of legacy segmentation approaches, for stronger, more predictable segmentation outcomes and greater operational simplicity. This highly secure but simplified approach includes Dynamic Host Configuration Protocol (DHCP) proxy, which creates a "network of one" for all connected endpoints, including those enabled with static IP. For example, the DHCP proxy intercepts all DHCP requests from devices trying to join the LAN. This enables Airgap to assign a /32 IP address and default gateway, effectively creating a segment of one. Airgap can then dynamically control access through continuous assessment of identity and context. Now, Airgap can provide visibility and policy enforcement at every connected endpoint without adding any software to those sensitive endpoints. This approach eliminates the risk of east-west lateral movement on local networks as well as the complexity of traditional segmentation approaches like east-west firewalls, without hardware upgrades or operational disruption.
Agentless Segmentation
It is critical to understand that an agentless approach is essential for effective east-west segmentation on LANs, given that in many scenarios, be it unmanaged devices, aging legacy servers, or headless IoT/OT infrastructure, deploying agents is an impossibility. However, with Airgap, Zero Trust segmentation is possible in campus LAN and OT environments, no matter the device.
Comprehensive Zero Trust Segmentation
If you have been a customer or followed Zscaler, you’ll know we take segmentation very seriously, as a measure to counter lateral movement of threats. In the Zero Trust Exchange, we currently protect thousands of organizations with Zero Trust Segmentation which comprises multiple methods of segmentation depending on the environment and scenario. This includes Zero Trust SD-WAN to securely connect locations and segment them without site-to-site VPNs. Zero Trust Segmentation is made up of:
- User-to-app segmentation: Users access private applications directly, without being put on a network.
- Location Segmentation: Zero Trust SD-WAN ensures connections are made directly to applications from an office, rather than connecting to a routable network. No more site-to-site VPNs
- Workload segmentation: Least-privilege access segments cloud workload-to-workload communications across hybrid and multi-cloud environments.
Now with Airgap, we further extend Zero Trust Segmentation to deliver visibility and segmentation for east-west traffic on LANs, including critical OT environments. Some of the use cases that can be addressed on day one are:
East-West Firewall Replacement
We will extend Zero Trust to the LAN by enforcing segmentation on east-west traffic. This shrinks the internal attack surfaces and eliminates the threat of lateral movement on campus, data center, and OT networks. 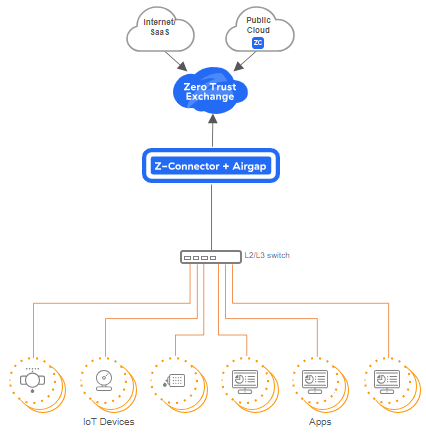
There is no need for NAC or firewall-based segmentation.
To enforce zero trust segmentation on campus, branch, and data center networks, Airgap will:
- Automatically provision every device into a segment of one (/32)
- Auto group devices, users and apps by analyzing the traffic patterns. This prevents rogue devices using MAC spoofing to get on to the network.
Dynamically enforce policies for east-west traffic based on identity and context of users and devices.
IT/OT Segmentation
Airgap’s technology acts as a ransomware kill switch, disabling non-essential device communication to halt lateral threat movement without interrupting business operations. Airgap’s solution neutralizes advanced threats, such as ransomware on IoT devices, OT systems, and agent-incapable devices.
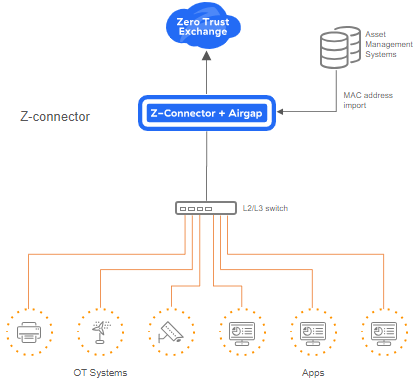
To secure IoT and OT, Airgap will:
- Autonomously group and enforce policy for known MAC addresses on any device; eg. RDP access to cameras denied except for Admins
- Automatically isolate unknown MAC addresses to limit blast radius in case of a compromised device.
- Integrate with asset management systems for secure access control policies.
Automatic Device Discovery & Classification
A significant portion of IT/OT traffic stays within the factory or campus, hence it is important to have continuous visibility into east-west traffic. With automatic device discovery and classification, network admins can better manage performance, uptime and security for IoT/OT systems without complex inventory management.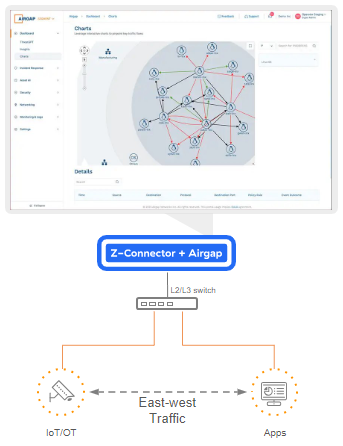
For network and device visibility, Airgap will:
- Discover, classify and inventory IoT/OT devices without the need for endpoint agents
- Get a baseline of traffic patterns and device behaviors in order to determine authorized and unauthorized access.
- Gain AI-driven network insights for performance management and threat mapping.
Modern segmentation for the enterprise, without the complexity
- Eliminate lateral threat movement across the LANs.
- Reduce operational complexity and cost associated with legacy segmentation tools.
- Gain enhanced visibility into east-west traffic with discovery, classification and device inventory without the need for endpoint agents.
We invite you to learn more about Airgap’s technology in an upcoming briefing on April 16th.
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.




