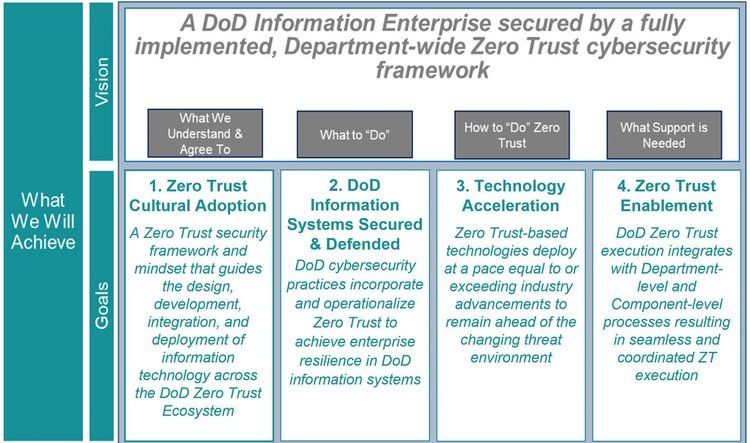
In October 2022, the Department of Defense (DoD) released a DoD Zero Trust Strategy document in which four key goals were identified including Zero Trust Cultural Adoption, DoD Information Systems Secured and Defended, Technology Acceleration, Zero Trust Enablement. With so many US Government guidances around Zero trust, the strategy guide focuses on DoD’s unique operational requirements. This was the subject of our conversation on a Government Technology Insider podcast.
DoD Zero Trust Strategy - What is it and why is it really needed?
The DoD Zero Trust Strategy document is designed to provide guidance to the MILDEPs and DoD agencies for deploying and measuring the success of their zero trust designs. The document states:
“This Zero Trust Strategy defines an adaptive approach for how DoD must champion and accelerate the shift to a Zero Trust architecture and framework…The intent of the strategy is to establish the parameters and target levels necessary to achieve Zero Trust (ZT) adoption across systems and networks.”
Within one of the defined goals, it lays out high level capability roadmaps for the DoD including seven DoD Zero Trust pillars, 45 different core capabilities that map to those pillars, and three different target levels. Each defense agency has its unique scenarios that they need to consider. Therefore, it's crucial to have a cross-functional team to help map out the zero trust capability model. This model can serve to get everyone aligned, to understand the current mode of operation and map out the future mode of operation.
Barriers for Agencies to Implement a Zero Trust Strategy
While the DoD strategy guide is partially designed to overcome barriers like differentiating definitions of Zero Trust, and how to measure it, there are still a few barriers DoD organizations must consider.
One potential barrier to implementing zero trust security is the existing security infrastructure and access controls that are already in place. The military, for example, has its own security infrastructure and access controls and, moreover, a process of evaluating its compliance under the Risk Management Framework (RMF) that has been built over many years. These systems are deeply ingrained in the organization's culture, and it is not easy to simply rip and replace them with a new approach like zero trust. To overcome this barrier, the DoD and other organizations will need to find ways to integrate zero trust into their existing security infrastructure and access controls gradually. This will require careful planning and a deep understanding of the existing systems and processes.
An additional barrier to implementing zero trust security is the need to stay flexible and adaptable as technology evolves. Specific capabilities or attributes that may be relevant today may become irrelevant in a few years due to changes in technology. To overcome this barrier, the DoD and other organizations will need to build a culture of continuous improvement and innovation, with a focus on staying flexible and adaptable to change.
Zero Trust Roadmap
Agencies can use the DoD Zero Trust strategy document to create an executable guide, or roadmap to include timeline gates, for their particular agency to implement a zero trust architecture. A simple three phased approach can help an organization align resources to both their zero trust strategy and modernization.
1. Inventory Assets. The first step is to get an accurate inventory of assets. This is critical because in a zero trust environment, each device and end user will have a risk score, and there will be conditional access control to those applications and devices.
2. Identify unifying zero trust assets to divest in. The second step is to create an inventory of assets that can be displaced when moving to a zero trust architecture. For example, with the adoption of cloud computing, agencies will start to see a lot more of the implementation of solutions like Secure Access Services Edge. This will result in a massive exodus of hardware leaving the shelves of facilities.
3. Operational value assessment of assets. Finally the third step is to work with the operations and acquisition teams to understand the value of assets that will be displaced. This is important because agencies will need to build a business case to explain why moving to a zero trust architecture makes sense.
While the above steps are a good starting point, there are undoubtedly many other things that agencies can do to prepare for the implementation of a zero trust architecture. The important thing is to start now, even if it's just taking small steps, and to not consider each step as one needing perfection, but instead one needing to be built upon along the way. Waiting until fiscal year 2024, when planning and preparation are scheduled to begin, could be too late.
Zero Trust’s Cultural Shift
Zero trust requires a cultural shift and operational alignment of what IT security really means. People are starting to understand that IT security is not just a supporting function but a domain in itself, and zero trust is a critical strategy in this domain. The future of IT security is about maneuvering within the domain of cyber warfare. This realization is changing the place of IT security at the table of senior leadership, and the adoption of the term zero trust is driving this cultural shift.
The future of zero trust is not just about the capabilities it provides, but also aligning talent and culture. The four main goals of the zero trust strategy guide fall under one capability, but the alignment of talent and culture is part of the other goals. Zero trust is not a one-time process or a checklist item; it requires a daily mindset shift, adaptive security, and constant learning.
Zero trust is no longer just a security model; it is a strategic initiative that is becoming a domain of warfare. It is essential to identify where an organization stands within the three target levels of the zero trust capability model and make incremental progress every day towards measurable successful implementation. With modern solutions aligning with zero trust, organizations will see significant changes in their security posture in 2024. Zero trust is driving a cultural shift towards a daily mindset shift, adaptive security, and constant learning, making it a strategic initiative in the DoD and across the entire US government.
The entire podcast can be heard here.




