The journey to implementing a zero trust architecture includes many steps, and deployment might be one of the most intimidating. Perhaps we cannot take all of the pain out of migrating to a zero trust architecture, but here at Zscaler we’re making “ease of use” a top priority to help agencies implement zero trust principles simply and efficiently.
As we’ve outlined previously, zero trust is not a single technology or solution. Rather it is a collection of concepts that make access control as granular as possible to prevent large scale disruption to IT infrastructures. The combination and integration of solutions and processes is inherently complex, but with the right approach much of that complexity can be removed from day-to-day IT administration.
Zscaler's FedRAMP HIgh and Moderate Zero Trust Exchange (ZTE) platform provides Government customers a true cloud-native platform that aligns with NIST's Zero Trust Framework and the Cyber EO mandates. The ZTE reduces complexity and provides scalability, all while improving your security posture. What does that mean for those tasked with designing, implementing and maintaining a zero trust architecture for your Federal Organization? Zscaler has built a process to streamline your transformation with three key success factors including a solution that is menu driven, scalable, and automated.
Menu driven
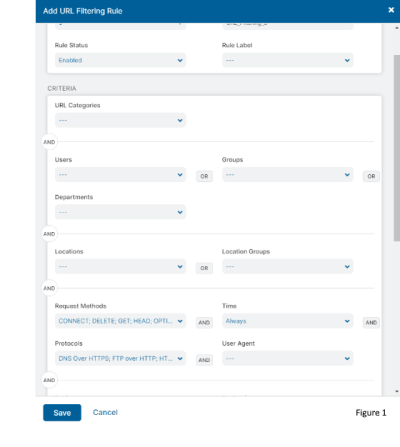 We focus on policies, not the platform. Out of the box Zscaler Internet Access (ZIA) is configured to stop the worst of the worst. Our policy-based system requires no command line experience. Rule creation can be as easy as defining who, what, and action. When you hit “Add new rule”, a menu similar to what you see in Figure 1 pops up to guide you through policy creation. However, the policy engine can go deeper to include: on what form factor, which request methods, where to allow viewing, when to allow uploads or downloads, how to caution the use, or when block the attempt. The easy to learn rule engine is common across ZIA policy including:
We focus on policies, not the platform. Out of the box Zscaler Internet Access (ZIA) is configured to stop the worst of the worst. Our policy-based system requires no command line experience. Rule creation can be as easy as defining who, what, and action. When you hit “Add new rule”, a menu similar to what you see in Figure 1 pops up to guide you through policy creation. However, the policy engine can go deeper to include: on what form factor, which request methods, where to allow viewing, when to allow uploads or downloads, how to caution the use, or when block the attempt. The easy to learn rule engine is common across ZIA policy including:
- Cloud Application Control
- Cloud sandbox
- DLP
- DNS
- SSL inspection
- And more
In practice, this allows the creation of broad initial rules, and refinement as your needs and missions dictate.
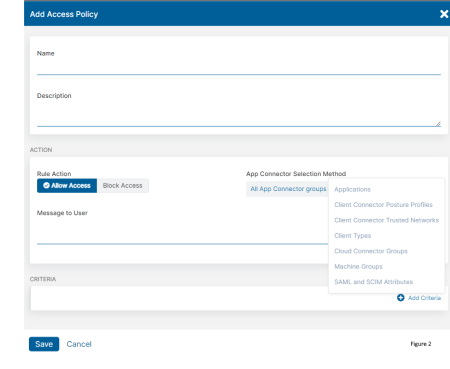 Zscaler Private Access (ZPA) is just as easy to configure. Figure 2 shows the menu to configure ZPA which allows you to add criteria for setting policies. ZPA can be set to automatically determine what private applications your customers are using and with one click you can define the application. Access policy is set by simply chaining together criteria and linking them with AND/OR statements.
Zscaler Private Access (ZPA) is just as easy to configure. Figure 2 shows the menu to configure ZPA which allows you to add criteria for setting policies. ZPA can be set to automatically determine what private applications your customers are using and with one click you can define the application. Access policy is set by simply chaining together criteria and linking them with AND/OR statements.
Like ZIA, policies can be as broad or specific as needed. With ZPA you can create rules based on client device posture assessment (FW enabled, Domain Joined, etc…), user attributes (Group, Department, etc...), client type, network location, and other factors. You can use these same criteria to build policy to bypass ZPA and set timeout policies for applications.
Scalable
Scale as needed
ZIA allows for deployment at speed and at scale. Our cloud-native architecture enabled one customer to deploy over 20,000 users over a weekend. Robust API support allows rule creation to be automated. Workflows can now be automated to require just an approval - no admin input needed!
ZPA is designed to surge and flex as needs change. Use your DevOps pipeline and automate the deployment and decommissioning of application connectors via our APIs. Automate the ability to surge capacity when and where needed. To take you out of the VM deployment business, ZPA has built-in support for scaling groups in AWS and API support for tools like Terraform. Additionally, our connector images are available on the cloud provider marketplaces for rapid deployment.
Redesign on the fly
New locations can be on-boarded or removed with a few clicks. Customers can deploy where needed and not have to go through a complex configuration for a new node or site. When the mission is over, it’s just as easy to remove a node/site. By leveraging our dynamic location groups, policy can be written and applied to the location group. As nodes or sites come on and off the network- they will join or leave the location group automatically. Meaning – you only write the policy once.
With ZPA, adding a commissioning and decommissioning a new data center for access is controlled by a key click and is transparent to your users. In a data center or VPC application, connectors are tied to connector groups. ZPA takes this a step further assigning connector groups to an intermediate construct called a server group. Server groups control which applications use which application connectors to reach the desired destination. Because of this, global applications can be assigned to a global server group. When a user connects to a global application, the ZPA cloud will connect them based on the best performing path – for them. If they then travel to another location the best path is recalculated. Because of this, disaster recovery is built into ZPA’s fabric and requires no user input.
Automated
Set and forget
With Zscaler, users won’t have to decide if the VPN should be on and where to connect. Zscaler Client Connector (ZCC) intelligently watches user location and connectivity to determine which cloud nodes to offer the best performance. ZCC will also detect if it’s on a trusted network segment and can change the way it processes traffic. Once your user moves, ZCC will update again, protecting traffic in the manner appropriate for the new location. This allows you to fully support a mobile and remote workforce, while cutting down on support calls due to user’s not using the VPN properly.
More than a point product
Zero trust takes a village
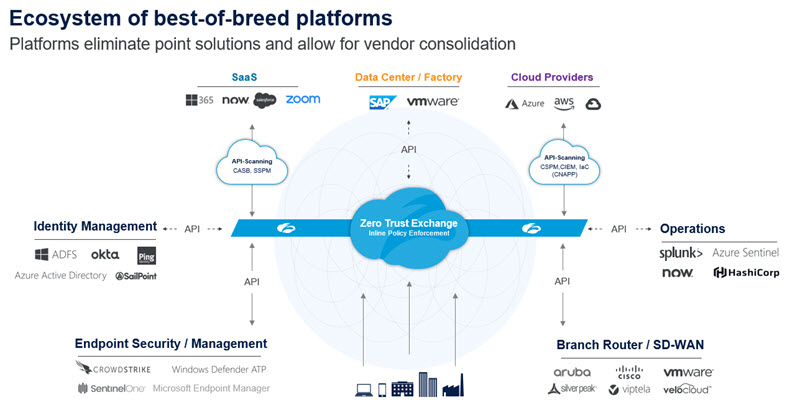
Achieving a true zero trust architecture requires a platform that eliminates point solutions and allows for vendor consolidation. Choose partners that know their strengths and aren’t trying to be everything to everyone. Zscaler has created a best-of-breed platform that uses the Zero Trust Exchange for inline policy enforcement while integrating with other best-of-breed solutions for zero trust functionality including Identity Management, Endpoint Security/Management, Brand Router/SD-WAN, Operations, SaaS, Data Centers and Cloud Providers. All in all, building a zero trust strategy around Zscaler’s Zero Trust Exchange allows for the network and security transformation that ultimately enables digital transformation.
Successfully embarking on a zero trust journey requires a phased approach. After working with over 300 public sector agencies on deployments, many best practices on the customer side have emerged for the smoothest user experience. We’ll be sharing these best practices and tips in Part II of this blog.
Contact Zscaler today to find out more about how Zscaler’s menu-driven, scalable, automated approaches can clear the way to a more secure future and ease your zero trust deployment.





