www.Google.com. Here is what the obfuscated malicious script looks like:
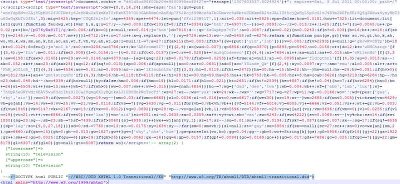 The malicious script is inserted just ahead of the opening HTML tag and decodes to any of the following domains which will ultimately deliver exploit code after multiple redirections,
The malicious script is inserted just ahead of the opening HTML tag and decodes to any of the following domains which will ultimately deliver exploit code after multiple redirections,okvmodps.co.tv
qbzaqmse.co.tv
jujbytqe.co.tv
ccjayplh.co.tv
sbzjrszn.co.tv
zarqqasx.co.tv
pboysxaj.co.tv
ecxajgff.co.tv
wkydwlkk.co.tv
bqhfvvdn.co.tv
cbneehtm.co.tv
xfrfrwjd.co.tv
neddhilr.co.tv
dzedshuw.co.tv
zhkeinzr.co.tv
rblvsbht.co.tv
itzqmiip.co.tv
mzpupkqo.co.tv
fkejoten.co.tv
rowxhoai.co.tv
eddddbzm.co.tv
bhbdzmjy.co.tv
xnnblhid.co.tv
zzxfyrru.co.tv
hocxhnrl.co.tv
rvcxwsmt.co.tv
wkrfgzoc.co.tv
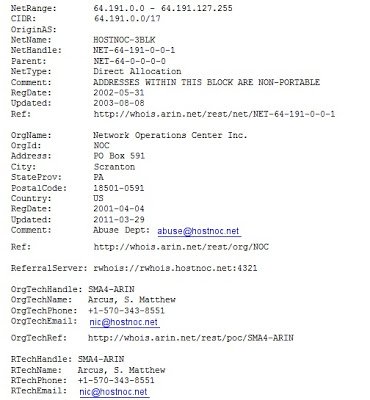
All above mentioned domains are hosted on the same IP address (64.191.81.117).Here is whois information for the IP:
Umesh




