Monsterindia.com is a very popular Indian job search website and a subsidiary of Monster Worldwide. If you are using Monster job search app for Android then you need to be aware of the fact that it’s leaking your username and password in clear text. Beyond this, it also leverages weak authentication encoding. If we sniff the traffic we can easily get username and password as they are sent via HTTP (no encryption). In order to see this in action, you can leverage ZAP (Zscaler Appliation Profiler), which helps you determine the overall risk posed by apps that you have installed on your Android/iOS device.
Here is registration screen of the app.
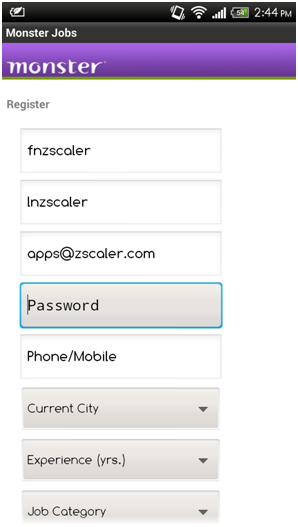
Lets dive in and see exactly how this app is leaking data. Let’s start with an initial account registration, when first installing the app. When doing so, you’ll observe following traffic:
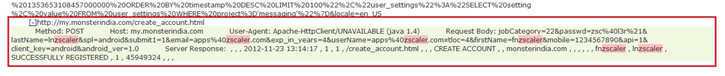
Here, if you look closely, you can observe the highlighted text, which reveals that the e-mail address, username and password are all transmitted in clear text.
If you then subsequently login with an already established account, you’ll observe the following network traffic:
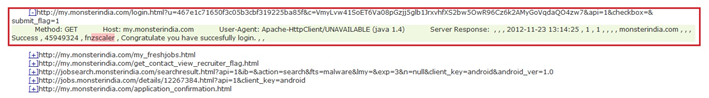
Here, I am using canary data for testing purposes and I have used ‘fnzscaler’ as the user name. As can be seen, this is again being sent in clear text to server. While not nearly as critical as the fact that the password was leaked during the account signup, there’s no reason why this traffic shouldn’t be sent via HTTPS to ensure that someone sniffing traffic on the network wouldn’t be in a position to brute force the login after obtaining your username.
Similarly if we take look at traffic on iOS device, the same thing can be observed. It is also sending the username and password in clear text during the registration process.
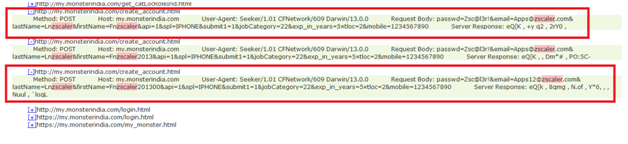
It is disappointing that Google’s Bouncerservice, or some other method was unable to quickly detect such simple coding mistakes and prevent an app with such a basic privacy flaw from appearing in the Google Play Store, until the issues are addressed.
For security purposes, I recommend that you check the risk score of apps on your mobile device, using ZAP. It can help to uncover high risk applications on the iOS and Android platforms.
Be careful while using such apps.





