A huge wave of the Flubot malware has been making its rounds in the wild, primarily targeting users in Europe -- particularly the UK -- and in the US.
Flubot is an Android banking malware which lures victims to install the app, eventually stealing victim's bank credentials. Flubot has a complete list of capabilities, but features overlay attack capabilities most prominently. It also holds capability to bypass financial institutions' multi-factor authentication security features.
According to Threatpost,
“The U.K.’s National Cyber Security Centre (NCSC) has issued security guidance about how to identify and remove FluBot malware, while network providers including Three and Vodafone have also issued warnings to users over the text message attacks”.
Initial Phase
Flubot's infection cycle starts with an SMS message luring victims by stating they have either missed their parcel or a new parcel is arriving. The SMS message contains a malicious link, which redirects users to a compromised website that downloads an Android banking malware.
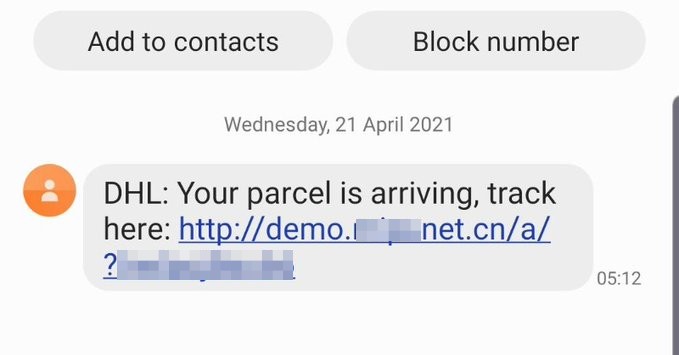 |
| Figure 1 : Flubot Smshing Link (src:https://twitter.com/VodafoneUK/status/1385326486144618497) |
The downloaded app, Flubot, portrays itself as one of the delivery apps from either “Fedex,” “DHL”, or “Correos”. And in some cases, as “Chrome”.
| Figure 2 : Malware Icons |
Features
Flubot is a typical Android Banking malware, which consists of following key features:
- Steals SMS messages
- Steals Contacts
- Spreads itself by messaging to contact list
- Reads notifications
- Gets list of installed applications
- Uses Accessibility Services
- Deletes apps from compromised device
- Performs calls
- Steals Credit Card information using fake system overlays
Some of the unique features include using Domain Generation Algorithm (DGA) to contact command and control (C&C) servers and encrypting part of the communication sent to C&C servers using RSA encryption. It can also disable Google Play Protect via Android’s Accessibility feature.
Once installed, the malware keeps a watch on the application opened by the victim. If the app turns out to be one of the targeted banking apps, it shows a fake overlay screen to the victim and eventually steals credentials.
Flubot also has the capability to steal credit card information by displaying a fake Google verification page.
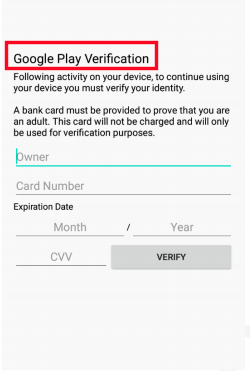 |
| Figure 3 : Credit Card Theft |
In-depth analysis of Flubot malware was done by Prodaft and can be found here (pdf)
Zscaler Coverage
Zscaler’s Defense-In-Depth approach prevents the infection at each step, eventually bringing down the complete attack kill-chain. References to Zscaler Threat Library and Flubot definitions can be found here.
As seen in the screenshot below, Zscaler’s advanced sandbox detects all the Flubot variants with utmost precision.
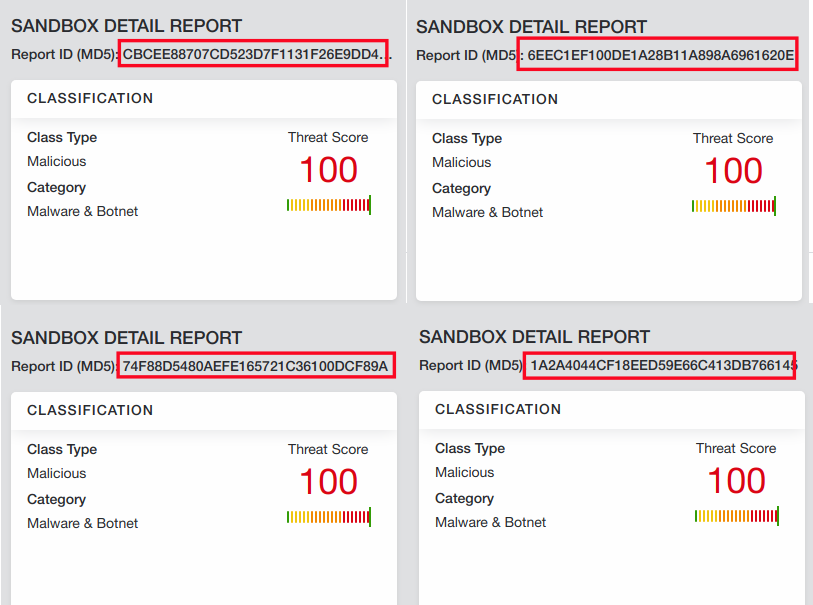 |
| Figure 4 : Zscaler Cloud Sandbox Detections. |
Conclusion
Due to the ubiquitous nature of the Android operating system, attacks on its users are inevitable and will keep increasing at a rapid pace. Android users should always be wary of the presence of mobile malware.
Malware such as Flubot have full potential to compromise victims with features like stealing banking credentials and bypass multi-factor security measures.
It is always advisable to stay away from third-party sources distributing Android apps, and to distrust any random links presented to you via email and/or SMS messages.
Zscaler customers are protected from such types of attacks. The Zscaler Security team, ThreatLabZ, provides proactive coverage against advanced threats targeting Android banking apps, such as Flubot.
ThreatLabz also tracks various Android malware families along with advanced APT (Advanced Persistent Threats) pertaining to Android ecosystem and ensures coverage for all the latest malicious indicators.





