Bring ease and speed to your IT M&A playbook
$1.5M
85%
80%
The Problem
Every merger or acquisition is a high-stakes undertaking
Weaving together workforces, application hosting environments, and shared access to resources across your new ecosystem—and doing so securely—is a massive architectural and engineering effort, and every delay can set you farther back from your synergy targets.

46% of mergers fail to realize revenue or cost synergies
PwC

51% of M&A/D dealmakers cite cyber as the top transaction risk
McKinsey

33% of acquired employees leave within 12 months due to poor experience
Deloitte
Solution Overview
Accelerate integrations to capture value faster with Zscaler
Maximizing value as you converge ecosystems can be a difficult balance. When low-value, high-effort domains—like networking and security—block your way forward, they put serious pressure on your timelines. With the Zero Trust Exchange, your way forward is clear.
Integrate only what you need
giving you unprecedented flexibility and options during integration.
Provide seamless, secure access
to discrete users, apps, and networked resources in days.
Access organization-wide resources
quickly and easily to cross-sell, innovate, and supply business services.
Reduce impact in the event of “buying a breach,”
keeping users productive while you assess and remediate with confidence.
Three Ways to Accelerate a Successful M&A Integration with Zscaler
Benefits
Join the 350+ organizations we’ve helped perform fast, secure IT integrations and divestitures with our unique zero trust approach
Reduce technical complexity
Remove significant technical debt and complexities so you can move on to value capture activities more quickly.
Protect deal value
Minimize threat exposure from acquired entities on Day 1 to safeguard against cyberthreats while you integrate in parallel.
Boost value capture
Drive meaningful Day 2 savings with consumption-based SaaS models, reducing tech debt by up to 40%.
Integrate or separate faster
Complete a higher rate of integrations or separations with our zero trust cloud platform and highly repeatable approach.
Solution Details
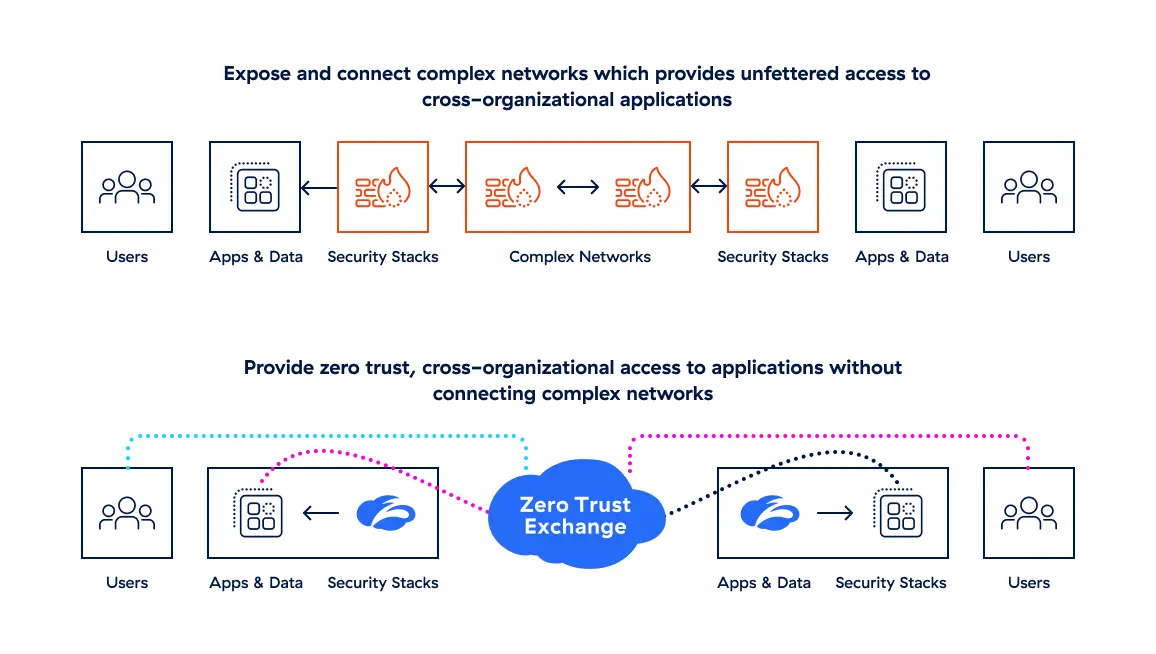
Zero trust and the integration life cycle
Day 1: Integration
Connect resources across your organization with no need to address underlying network complexity—get users productive on Day 1.
Contain acquired vulnerabilities or potential compromises instantly when you overlay your risk posture on the acquired network.
Deliver seamless access to any cross-organization apps and resources with a simple desktop agent.
Day 2 and Beyond: Optimization
Expand and fine-tune Day 1 deployment as you transform to a zero trust architecture.
Connect and secure users and data anywhere while greatly reducing technical debt.
Achieve synergy savings targets with lower run-rate costs by eliminating hardware refresh cycles, support contracts, network circuits, and more.
How Zscaler streamlines M&A integrations
M&A roadmap
Connect
- Provide cross-entity access with a zero IT footprint architecture to instantly connect acquired to buyer (or vice versa) without connecting networks or IP overlap
Secure
- Remove external exposures to minimize risk
- Overlay access to private apps, supporting productivity while learning about app/user inventories and interactions
- Provide data protections to ensure crown jewel IP never leaves your control
Elevate
- Integrate other risk profiling capabilities to provide dynamic risk-based policy
- Adopt data protection (CASB, DLP, etc.) as needed for compliance
- Define and enable more granular access and zero trust policies
Innovate
- Add user experience telemetry to your help desk to raise First Time Fix Rate (FTFR)
- Apply a zero trust architecture to workload-to-workload communications
- Remove network and security stacks or technical debt offsets
- Remove/Replace SD-WAN/network circuits with pure internet access and adopt new tech like 5G














