Overview
Provide seamless application access without VDI or network integrations
Contractors, partners, and other third parties need SaaS and private app access to get work done. Options like VDI, VPN, enterprise browsers, or extending network access are difficult, expensive, and not built to protect data. Give third parties secure, agentless app access—from the browser they already use—with data security included.
Enable productivity on unmanaged devices
with browser-based app access
Prevent data exfiltration and risky user actions
with robust data security controls
Provide direct user-to-app access with no VPN
for built-in app segmentation
The Problem
Traditionally, third-party users access apps through slow, expensive VDI or a VPN agent installed on their devices. Either approach has three main challenges.
Giving third parties broad network access via VPN lets them access other sensitive information. VDI lacks integrated data protection to prevent data exfiltration.
VDI latency hinders productivity, and VPN agents frustrate users by forcing them to convert their personal devices into corporate-managed endpoints.
VDI is synonymous with "expensive," potentially costing more than $1,000 per user per year in licensing, infrastructure, and operations.
Solution Overview
Easily minimize third-party risk with Zscaler
Take a user- and application-centric approach to security with Zscaler Third-Party Access. Provide only authorized users with access to specific apps—with great user experiences, integrated data security and private AppProtection; and no software agents, new dedicated browsers, or VDI—all without granting network access.
It works seamlessly with any device, including bring-your-own-device (BYOD), in the user's browser of choice, while your IT team maintains granular control. Authorized users gain secure access to the apps and data they need, and nothing else.
Security
Segment application access with direct user-to-app connections, preventing lateral movement. Restrict risky actions like copy/paste or document downloads to unmanaged devices to protect against web-based risks and block data exfiltration.
Simplicity
Grant users seamless access to authorized applications from their own web browser, on any device. No need to install agents or deploy a separate browser for enterprise use.
Integration and value
Maintain consistent policies and ease of management from a single, unified platform. Eliminate costly technologies like VDI to drive down costs many times over.
Benefits
Enable secure app access in minutes
Provide a seamless experience
for third-party and internal users
Offer secure, agentless access
to apps from BYOD using your current IdP
Support access to SaaS and private apps
both on-premises and in the cloud
Drive down costs
with more cost-effective app access than VDI
Solution Details
A fundamentally different approach
Most access solutions are flawed. VPNs are network-centric. VDI is slow and expensive. Enterprise browsers add cost, risk, and another tool to manage.
Zscaler does things differently. Unlike VPNs or VDI, Zscaler Third Party Access seamlessly connects users directly to enterprise apps through a cloud native zero trust architecture, reducing risks stemming from overprivileged access.
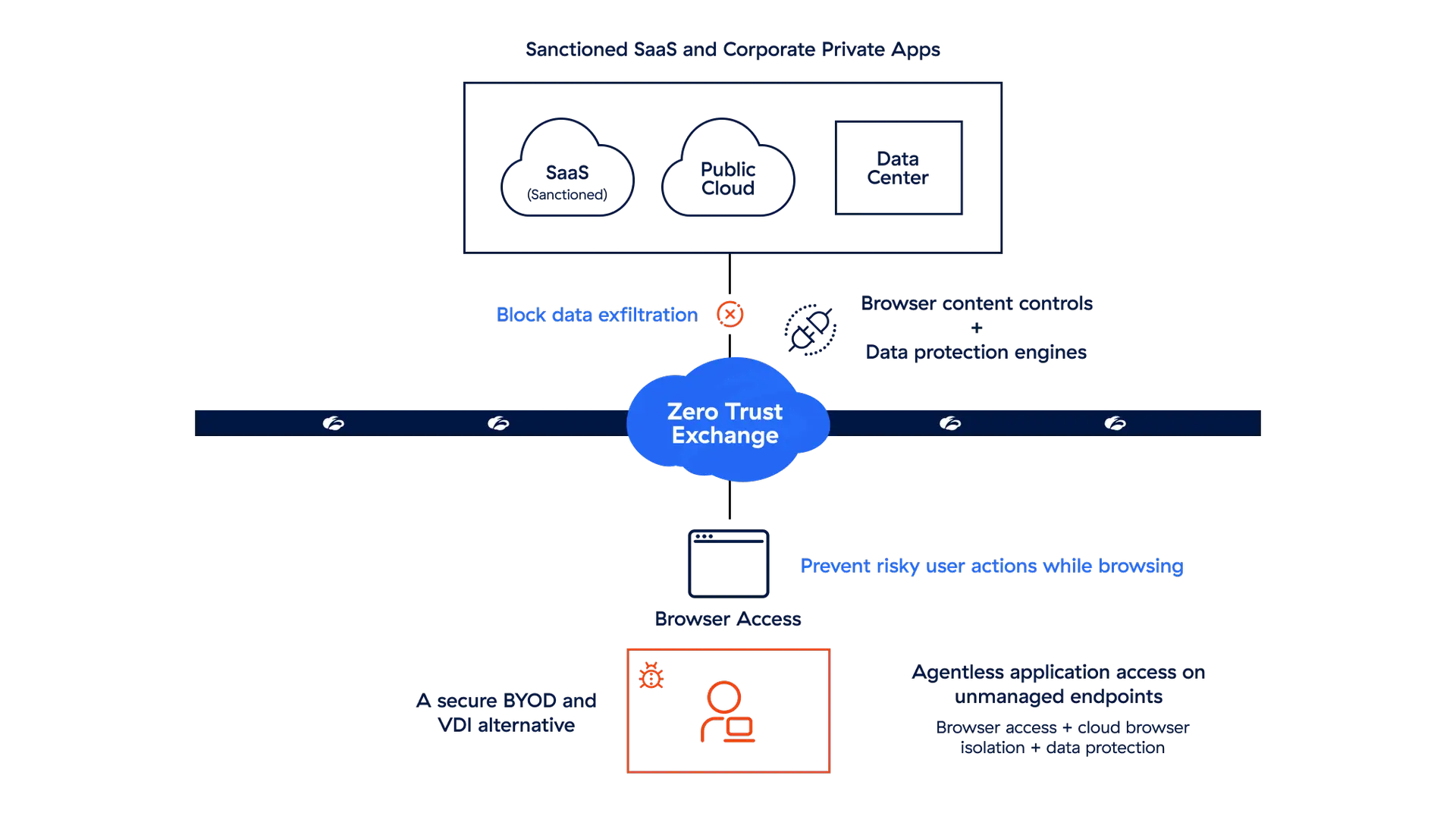
Browser-Based Access
Deliver agentless access to SaaS and private apps via Zscaler for unmanaged devices.
Cloud Browser Isolation
Enforce powerful last-mile data controls to stop risky user actions like uploads, downloads, printing, copy/paste, and more.
Zscaler Data Security
Prevent data exfiltration with fully integrated, fine-grained data security running on all user sessions.
Zscaler AppProtection
Prevent zero-day attacks and browser-based vulnerabilities by identifying high-risk users through user browser activity.

our platform
The Zscaler Zero Trust Exchange
Secure user, workload, and device communication between and
within the branch, cloud, and data center.
Zero Trust Everywhere
Secure Data
- Find, Classify, and Assess Data Security Posture
- Prevent Data Loss Across All Channels
Secure AI
- Secure the Use of Public AI
- Secure Private AI Apps and Models
- Secure Agent Communications
Request a demo
Let our specialists show you how ZPA can quickly and securely transform your operations with zero trust network access.





