The rise of IoT
IoT devices are being leveraged by businesses to simplify processes, enhance productivity, and gain a competitive edge. The rapid pace of implementation and the diversity of devices being utilized—ranging from water dispensing machines and smart thermostats to barcode scanners and CCTV cameras—create problems for networking and security teams as they attempt to protect the business from potential risks and the growing threats against IoT.
The fundamental challenges
Between Q3 2019, and Q4 2020, malware attacks against IoT surged by 30X. These attacks against IoT can disrupt business operations, cause financial burden, and impact your employees and end users. But solving the security problem is a multifaceted challenge. It begins with the basic fact that you cannot protect something if you don’t even know it is there. Shadow IoT and unknown devices connecting to the network create blind spots for enterprises that make it difficult to even know what devices are connected to the network.
Making matters worse, security was clearly not top of mind in the design process for the majority of IoT devices. Most lack fundamental security, are unable to host traditional agents or certificates, have weak or non-existent encryption capabilities, and are difficult to patch and update. This makes IoT an attractive target for attackers and leaves organizations at risk.
Traditional approaches create more challenges
Traditional approaches are costly, require significant administrative overhead, and actually make identifying, classifying, and monitoring IoT devices more difficult. Most require admins to manually gather data, schedule data collection monthly or quarterly, and only provide a snapshot view of a single point in time. Administrators must juggle between different tools to piece together fragmented information in an attempt to build a partial view of IoT devices on their network.
Alternative approaches require installing sensors at each location to monitor IoT traffic from your network, resulting in increased management complexity and administrative burden, thus increasing costs. Because of these issues, it should be no surprise that recent research from Kaspersky indicates that 43% of businesses admit they don’t protect their full suite of IoT devices.
Visibility is key
How can an organization address these challenges? To secure IoT devices, you must first know what devices are connected to your network, what those devices are doing, and where they are connecting. To eliminate blind spots and provide a complete picture of your IoT landscape, Zscaler has introduced Zscaler IoT Device Visibility, part of the Zscaler Zero Trust Exchange.
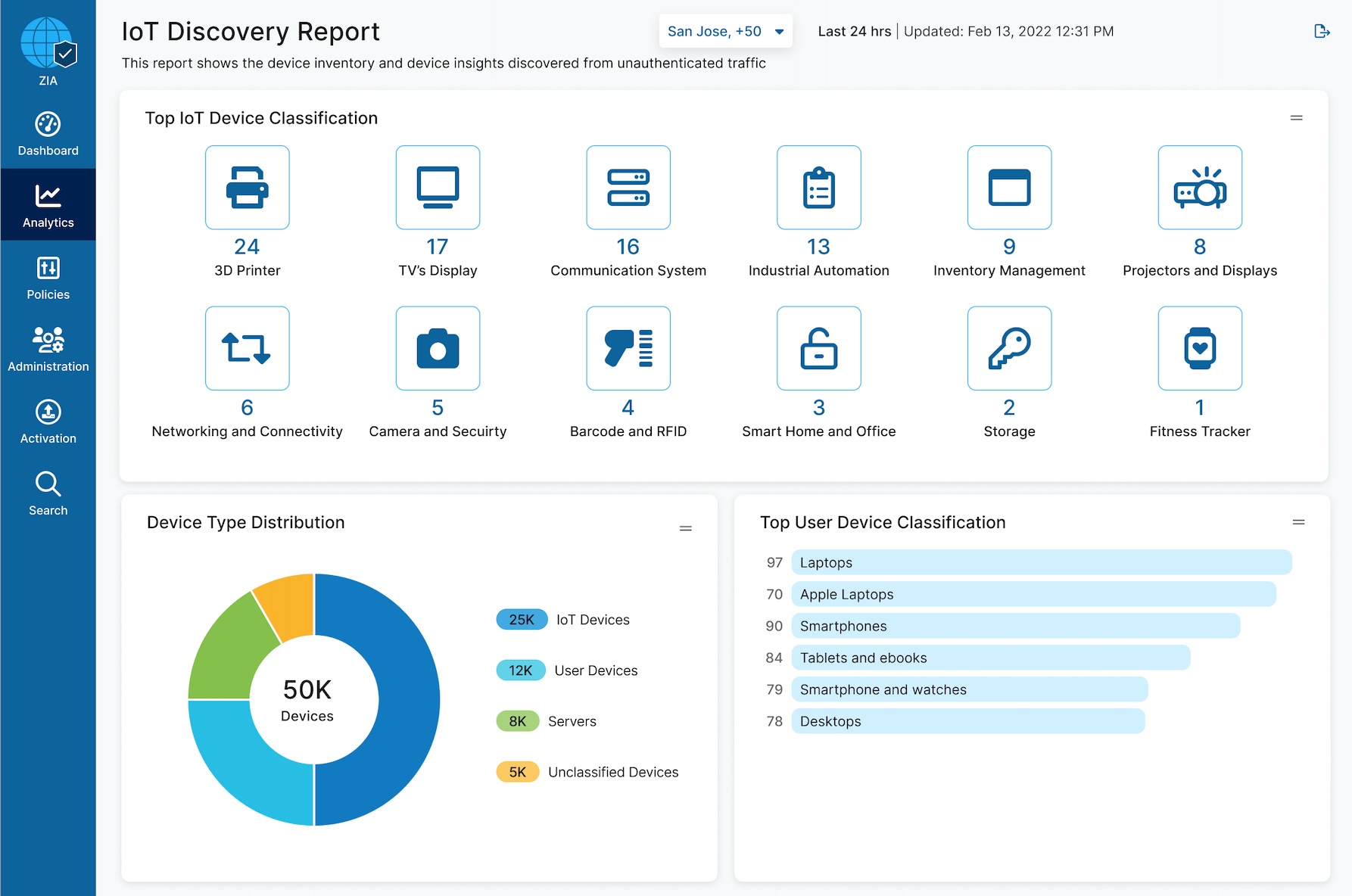
Zscaler IoT Device Visibility automates discovery of IoT devices connecting to your network and offers continuous monitoring to provide real-time insights that guide your IoT security policy. AI/ML classification, with industry-leading auto-labeling capabilities, automatically identifies device types based on activity and behavior, eliminating the need for manual processes and sensor installation. With Zscaler IoT Device Visibility, you get the full context of IoT devices, servers, and unmanaged user devices across your environment, including device classification, data consumption, destinations visited, and applications utilized—all within the Zscaler Admin Portal.
The prescription for secure IoT adoption
Zscaler IoT Device Visibility takes away the pain of traditional approaches and enables organizations to confidently expedite their journey to secure IoT adoption. By delivering comprehensive visibility into IoT devices, servers, and unmanaged user devices as part of the world’s largest cloud-delivered security platform, organizations can reduce risk, simplify management, and increase productivity and business agility.
If you would like to learn more about Zscaler IoT Device Visibility, please visit our website and request a demo.





