Welcome to the second installment of our OWASP Top 10 blog series, where we’ll be discussing one of the most critical web application security risks - injection attacks (ranked #3 on the OWASP Top 10). Injection attacks refer to a range of tactics used by hackers to trick web applications into performing unintended actions such as destroying databases, compromising backend systems, or hijacking other clients connected to the application. In technical terms, injection flaws permit attackers to send hostile code or input data to an application, tricking the code interpreter into executing unintended commands or accessing data without proper authorization.
Injections aren’t new but are among the most dangerous types of attacks for web applications because when successful, they can lead to data theft, denial of service, and even complete system compromise or destruction. Not only are injection vulnerabilities dangerous, but they’re also pervasive, especially in legacy applications which is why injection attacks are still considered one of the top web application security risks by OWASP. Some of the most prevalent and easily exploitable injection flaws are SQL (structured query language) injection and cross-site scripting (XSS).
In 2019, millions of Fortnite users were impacted by a cyber attack that utilized SQLi and XSS tactics to gain unauthorized access to player accounts and compromise their data. The hackers manipulated the game's backend database using SQL injection and stole user session tokens via XSS to bypass login authentication. The Fortnite hack highlighted the severity of injection attacks and highlights the need for stronger web application security measures. Now, let’s take a closer look at SQL injection attacks and the potential consequences they can have on organizations.
SQL injection attacks
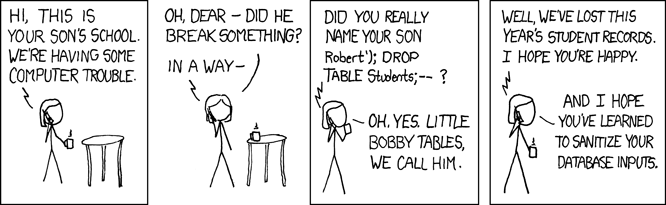
Source: https://imgs.xkcd.com/comics/exploits_of_a_mom.png
SQL injection (SQLi) attacks involve inserting malicious code into a SQL query through user input, which is then executed by a website’s backend database server. Successful SQL injection exploits can result in massive data loss and disruption as the attacker gains access to and manipulates the database such as reading and modifying tables, executing privileged operations. These types of vulnerabilities remain prevalent because user input must be sanitized/validated before being passed into a query, but software developers often forget to do it or don’t do it properly. What’s more, databases themselves are attractive, high-value targets for attackers because they often contain critical or sensitive information.
To protect against SQL injection attacks, it’s important to take the following steps:
- Use prepared statements, stored procedures, or an ORM
- Validate and allowlist user input
- Limit user privileges and use the principle of least privilege
- Monitor logs for signs of SQL injection attacks
- Keep software up to date with security patches and updates
Cross-site scripting attacks
Cross-site scripting (XSS) vulnerabilities pose a serious threat to web applications because they enable attackers to inject malicious scripts into legitimate websites and trick unsuspecting users into executing them. This can lead to the theft of sensitive data, such as login credentials or financial information, or even the complete takeover of a victim's web session. In some cases, these attacks can also pave the way for other types of attacks, such as malware distribution or further exploitation of vulnerabilities in the web application.
These attacks are insidious, exploiting application vulnerabilities by manipulating user input without proper validation or encoding. Attackers start by sending seemingly harmless scripts to unsuspecting users, which browsers view as trustworthy. Once the scripts are executed, they can gain access to sensitive information, like session tokens and cookies, and even manipulate website content. To mitigate the risk of XSS attacks, it’s important to take the following steps:
- Use a Content Security Policy (CSP) to specify allowed content
- Use output encoding or HTML entity encoding to display user input safely
- Follow secure coding practices and use secure frameworks
- Verify user input on the server side to prevent malicious scripts
- Install a web application firewall (WAF) for extra protection. If you are a Zscaler Private Access customer make sure to use AppProtection
- Avoid using certain functions with user input, like eval() and setTimeout()
- Turn off unnecessary browser features or plugins
- Educate developers and users about XSS attacks
- Use HTTP-only cookies to secure session data
- Regularly update and patch web applications and servers to address vulnerabilities
3 practical recommendations to defend your apps against injection attacks
Don't let injection attacks take down your web applications. Sure, writing secure code is important, but that’s not within the control of most network and security teams. So what can you do? A zero trust-based architecture is recommended to:
1) Minimize the attack surface presented by the exposed IPs of firewalls and VPNs that protect your internal applications by making your infrastructure undiscoverable
2) Minimize lateral movement of users and threats across the network by enforcing least-privileged access and only connecting a specific, authorized user to a specific, authorized resource
3) Prevent compromise by threats hidden in encrypted traffic by blocking malicious content with inline inspection of user-to-application traffic
Protecting your applications from injection attacks requires a multi-layered approach. In addition to implementing a zero trust-based architecture, organizations can also enhance their application security with Zscaler Private Access (ZPA).
Strengthen your application security with Zscaler Private Access
When your applications are protected by Zscaler Private Access (ZPA), they are concealed from the internet and attackers. Only authenticated and authorized user traffic can access them, which reduces the attack surface and blast radius for lateral movement. But that doesn’t mean your risk goes down to zero. In case of a user's identity being compromised, skilled attackers can exploit known (or unknown) software vulnerabilities. Inline defenses are needed to identify malicious traffic and hidden threats. That's why we integrated high-performance security inspection into ZPA. Similar to the robust inspection capabilities for public apps, we can inspect for threats against private apps.
With this essential layer of visibility into private application traffic, you can identify and block the most common web attacks, including SQLi, XSS, remote code execution, and more, using ZPA’s predefined OWASP Top 10 controls. Additionally, we provide the flexibility to create inspection profiles and write your own signatures. With these measures in place, you can have peace of mind knowing that your internal applications are safe from web attacks.
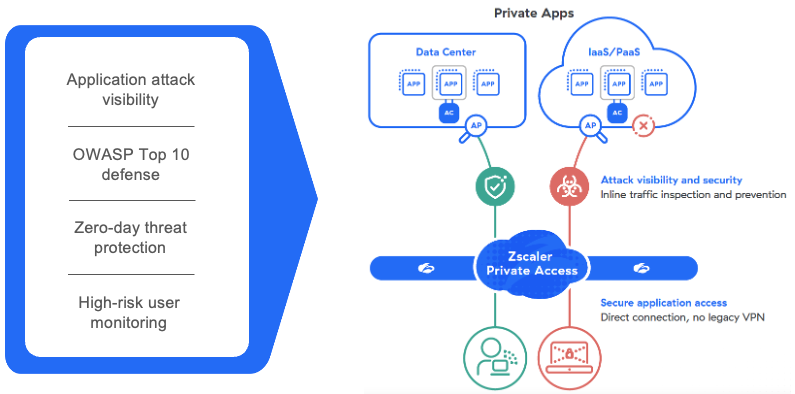
ZPA AppProtection monitors all incoming and outgoing application traffic.
How to get started with ZPA AppProtection
Getting started with AppProtection has never been easier. Simply define your AppProtection Profile and select from a list of OWASP Predefined Controls to customize how your traffic is inspected and managed. Choose a Paranoia Level that matches your level of concern, set up your AppProtection policy with the desired override actions, and review your profile configurations before deploying them in an AppProtection Policy. With our user-friendly AppProtection Dashboard, monitoring and responding to any detected attacks is a seamless process!

Safeguard your apps from injection attacks and ensure business continuity
Let’s face it - injection attacks are a ticking time bomb when it comes to application security. These sneaky attacks can impact both legacy and modern applications, and the consequences can be devastating - think massive data loss and total system compromise. Fortunately, there are practical steps that organizations can take to safeguard against injection attacks. By implementing zero trust principles, validating user input, and monitoring for attacks, organizations can significantly reduce their risk of being victimized by injection attacks. For those using ZPA, AppProtection has your back with high-performance security inspection capabilities to detect and prevent these types of attacks. It’s essential for organizations to take web application security seriously and follow best practices to protect against injection attacks and other web-based threats.
Ready to learn more? We’ve got you covered:




