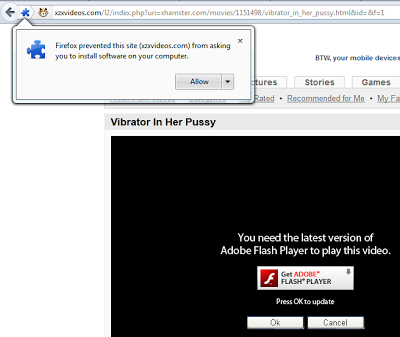
This type of attack is still going on. Today, I was investigating such a malicious page. The page claims to be from xhamster.com, a free porn site. The fake video player shows a warning: "You need the latest version of Adobe Flash Player to play this video."
 |
| Fake porn video |
 |
| Malicious extension for Firefox |
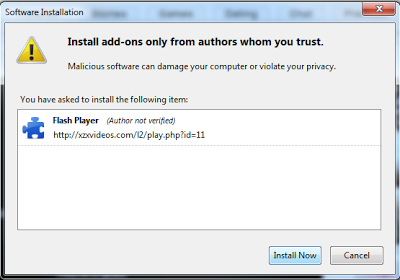 |
| Extension installation on Firefox |
 |
| Fake extension installed |
Browser extensions are open doors to infect users. Antivirus vendors do a very poor job at decting fake extensions, mostly because they are just plain text files (HTML, JavaScript), and cannot therefore contain binary malware. The VirusTotal reports for this particular attack illustrate the challenge:
- executable (Internet Explorer): detection by 21/42 AV
- XPI (Firefox): 0 detected!
- CRX (Chrome): 0 detected!
Browser extensions
Browser extensions have a fairly simple structure. They don't generally contain any malicious code directly, rather, when the browser starts, the add-on fetches the malicious JavaScript code from an external server and executes it.
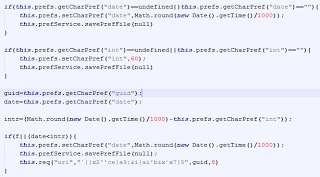 |
| Fake extension code after deobfuscation |
The current files being pulled are not very dangerous, but that could change in the future. An invisible IFRAME is inserted in each new page loaded. The IFRAME contains advertising from resultsz.com, and contains a username in the URL. This tells me that the adware author gets money for the traffic sent to this site, even if the infected user cannot actually see what is being loaded.
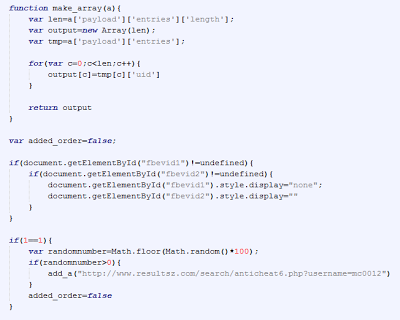 | |
| Remote file content after deobfuscation |
The author could change the remote file at any moment to do much more harm, like stealing cookies to obtain access to the user accounts on any site, stealing username/credentials being entered or previously saved, etc.




