/ What Is 5G Security?
What Is 5G Security?
5G security is an area of wireless network security focused on fifth-generation (5G) wireless networks. 5G security technologies help protect 5G infrastructure and 5G-enabled devices against data loss, cyberattacks, hackers, malware, and other threats. Compared to previous generations, 5G makes greater use of virtualization, network slicing, and software-defined networking (SDN), making it vulnerable to new kinds of attacks.
Why Is 5G Security Important?
As 5G technology is rolled out in more and more countries, it will have a huge impact on critical infrastructure and global industries. However, the technological advancements of 5G also come with new and heightened cybersecurity risks that telecommunication operators and their customers can’t ignore, including:
- Expanded attack surface: More connected devices and more infrastructure migrating into the cloud create a wider range of entry points for cybercriminals to exploit. And because 5G enables millions of devices per square kilometer to interconnect (vs. tens of thousands of 4G LTE and Wi-Fi enabled devices), one exploited device could lead to cascading vulnerabilities compromising whole ecosystems.
- Network slicing vulnerabilities: 5G infrastructure enables network slicing—creating multiple virtual network segments side-by-side in a 5G network, each serving specific apps, companies, or industry verticals. This is efficient, but it opens the door to intra-slice attacks and other new risks. Slices need to be securely isolated and segmented to prevent attackers from moving laterally.
- Supply chain risks: The adoption of 5G relies on a global supply chain of hardware, software, and services. Ensuring the security of all components is challenging, as malicious actors may attempt to compromise one or more points in the hardware/software supply chain to infiltrate 5G networks and devices.
- Data privacy concerns: 5G networks support massive data exchange and processing, creating privacy concerns around the ever-increasing amounts of personal/sensitive data involved. Unauthorized data access often leads to identity theft, fraud, and other misuse.
- Threats to critical infrastructure: As 5G technology integrates with national critical infrastructure like power grids, transportation systems, and healthcare facilities, a breach could have serious implications for public safety, patient health, industrial operations, national security, or even economic stability.
While 5G is poised to drive the next generation of technological transformation across industries, governments, and more, it also comes with greater (and in some cases, unquantified) security risks.
5G Security Benefits
Service providers and mobile network operators have a responsibility to ensure the privacy, security, and integrity of customer data and operations on their 5G networks. With effective security measures in place, providers and operators can:
- Leverage real-time security monitoring and analysis to more quickly detect and respond to potential security threats
- Minimize the impact of cyberattacks and reduce the associated costs and reputation damage
- Demonstrate a commitment to the integrity of customers’ data and operations, building their loyalty and trust
With smart manufacturing—Industry 4.0—in full swing, businesses using internet of things (IoT) devices are eager to use 5G networks to keep their IoT devices connected and performing.
How Does 5G Work?
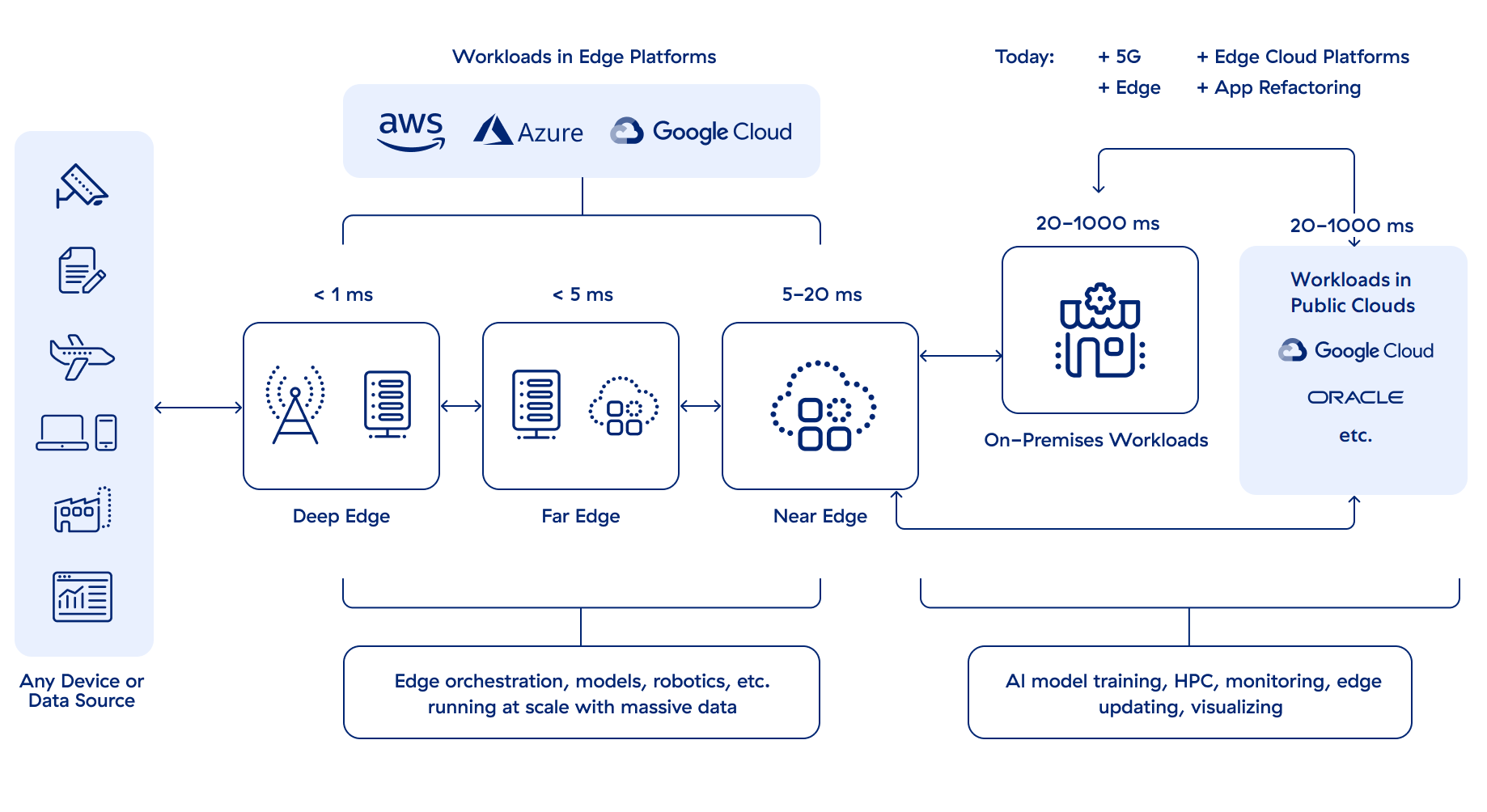
5G uses a broad mix of radio bands that push speeds of up to 10 Gbps (10 to 100 times faster than 4G-LTE), which will soon make web experiences that feel “fast enough” today feel like the days of dial-up. 5G offers ultra-low latency, which translates to near-real-time network performance. Where a packet of data could previously take 20 to 1,000 milliseconds (ms) to get from your laptop or smartphone to a workload, 5G can cut that time down to a few milliseconds when the use case demands it.
Naturally, there’s more to it than that—physical speed alone doesn’t reduce latency. Various factors, including distance, bandwidth congestion, software and processing deficiencies, and even physical obstacles, can contribute to high latency.
To achieve ultra-low latency, what compute resources need most is to be closer to end user devices. Having servers located physically close to end-user devices is called “Edge compute.” The type of Edge compute varies by latency range:
- Far Edge: Between 5 and 20 ms latency; farthest from the cloud and closer to devices
- Near Edge: 20+ ms latency; nearer to the cloud than to devices
- Deep Edge: Less than 5 ms away from devices
A basic 5G network schema—where does your network start (or end)?
Use case, latency requirements, and budget all factor into what level of Edge compute is needed. Not everything needs near real-time performance, but many things need “good enough real-time,” for which 20 ms or so is adequate.
5G is also designed to be massively scalable for connected devices. Upgraded radio access networks can support 1,000 times more bandwidth per unit area and 100 times more connected devices than 4G LTE. Consumer mobile devices, enterprise devices, smart sensors, autonomous vehicles, drones, and more can all share the same 5G network without service degradation.
5G vs. 4G
4G and 5G are both high-speed wireless telecommunication technologies for mobile devices.
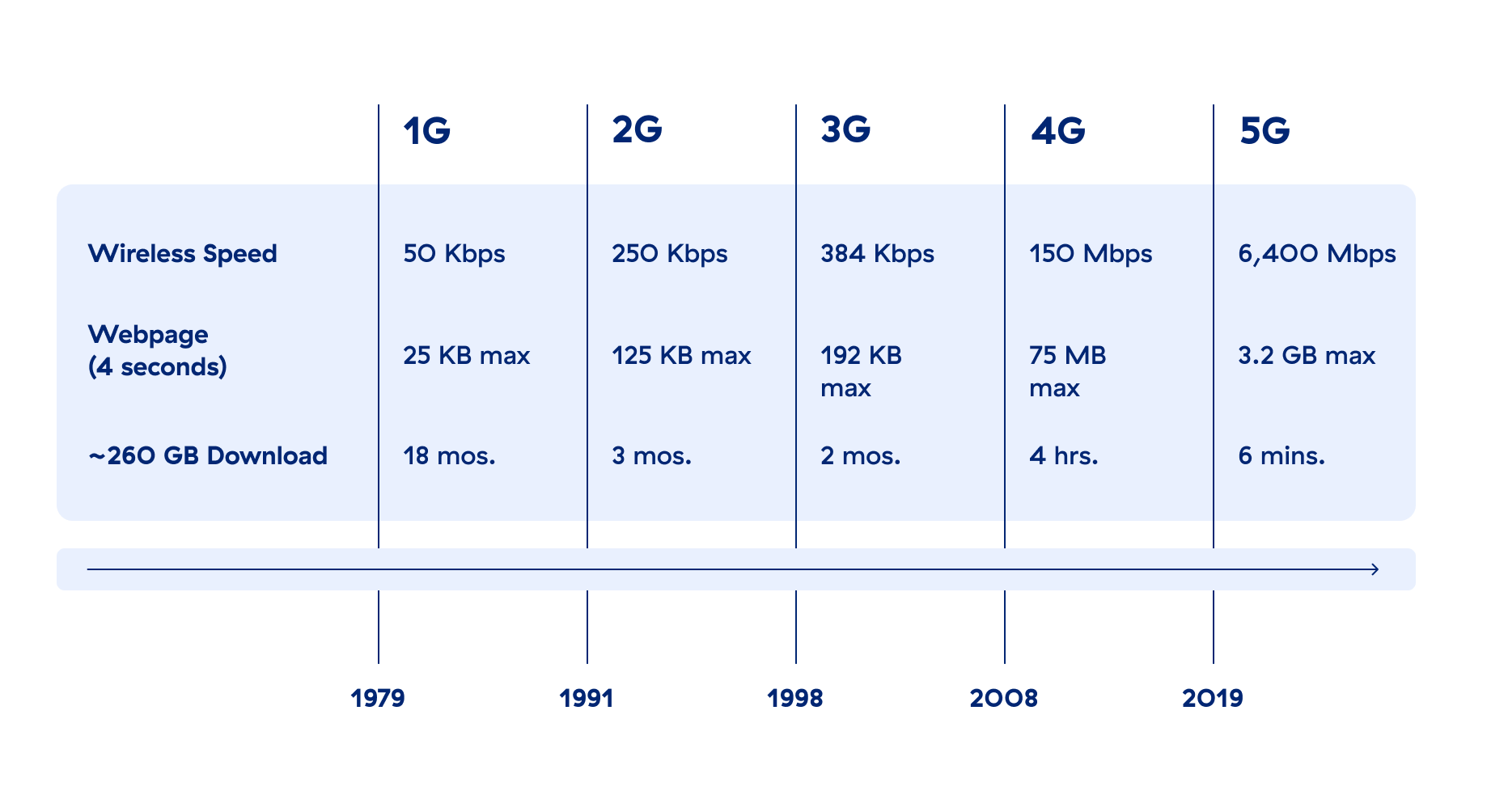
In terms of technical capabilities, 4G offers data rates of up to roughly 100 Mbps, while 5G can offer up to 20 Gbps. For communications between devices, 4G latency ranges from about 60–100 milliseconds, whereas 5G can offer far lower latency, potentially under 5 milliseconds. And when it comes to bandwidth and the volume of connections, a 4G network can support several thousand devices in one square kilometer, while a 5G network can support a million.
The more complex infrastructure of 5G also widens its attack surface, however, and with far more connected devices and far faster data transfer rates than 4G, 5G is significantly more vulnerable to cyberattacks. Beyond that, the use of new technologies such as virtualization and software-defined networking in 5G networks may lead to new vulnerabilities for threat actors to exploit.
Finally, among the most critical differences between generations: 5G functions on the network edge, not within the traditional infrastructure 4G relies on. By extension, security can’t be effectively delivered by traditional network infrastructure, and must instead be delivered at the network edge as well.
Let’s look at 5G with respect to edge computing and security next.
How Does 5G Work with Edge Computing?
5G technology and edge computing (distributed computing that enables data processing and storage at the edge of the network) are transforming the way we communicate and do business. Enhancements in speed, real-time data transmission, and mobile network density are the cornerstones of modern connectivity—delivering the capacity essential for IoT-connected devices, automation, VR and augmented reality interfaces, smart cities, and more.
In effect, 5G provides the high-speed connectivity and low latency required for edge computing to function effectively. Data can be transmitted and received almost instantly, allowing for real-time communication and analysis to support time-critical services and other applications that require immediate response, such as some Industry 4.0 functions.
Among many other factors of 5G network design, physical proximity to the device is key to achieving low latency. This means that the core network infrastructure, application server, and—crucially—the security infrastructure need to be relocated from centralized data centers to the edge of the network, closer to users. For that, organizations need to look to zero trust.
5G Security Challenges
The 5G standard explicitly calls out that security is a key design principle. This usually means you’ll read that “5G is secure by design.” In other words, 5G was designed to be secure.
The reality is that 5G security is limited to the network itself. It doesn’t extend to the devices and workloads customers will use to communicate through a 5G network.
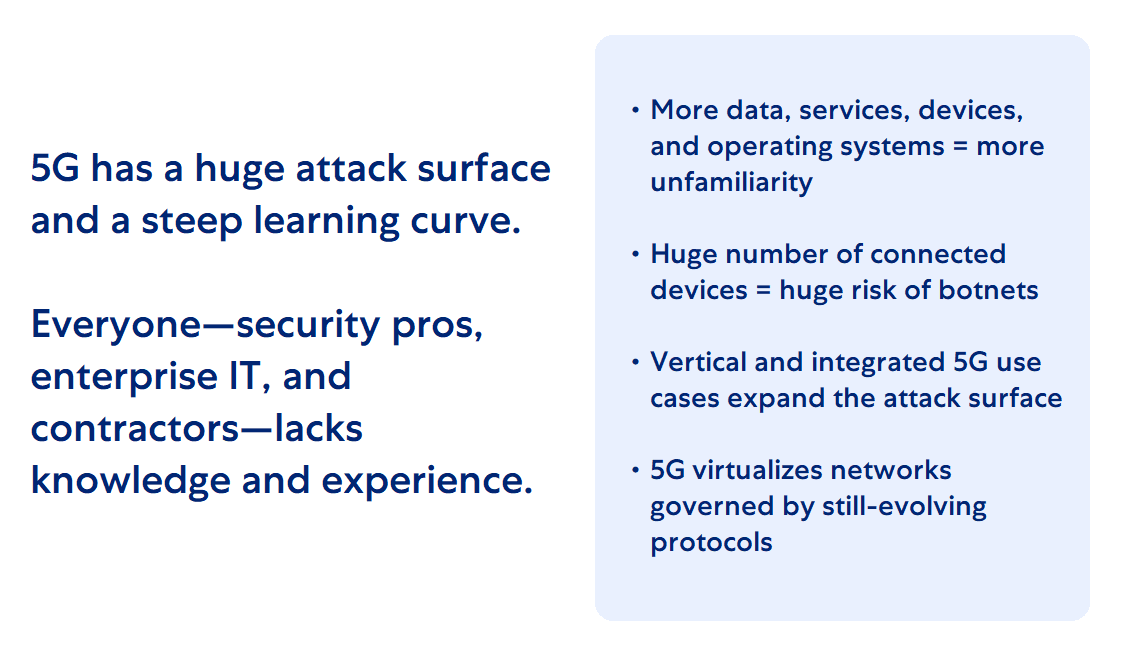
So, while 5G means more data, services, devices, operating systems, virtualization, and use of the cloud, it also means the 5G attack surface is huge, and Edge workloads are many attackers’ new preferred targets.
5G security has a steep learning curve, and many security professionals, enterprise IT, and sub-contractors lack the knowledge and experience to protect apps running on 5G networks. As the joining of highly-scaled IT systems to wireless telecommunications networks, 5G needs cybersecurity specialists skilled in both worlds.
5G and Zero Trust for Maximum Security
Zero trust simplifies the protection of 5G/edge workloads and devices, meaning organizations that embrace it will find embracing 5G and its attendant security challenges easier, faster, and safer.
Zero trust is the architecture for comprehensive security monitoring, granular risk-based access controls, infrastructure-wide coordinated system security automation, and real-time protection of critical data assets in a dynamic threat environment.
How Zscaler Can Help: Embrace the Zero Trust Security Model
Zscaler Zero Trust Architecture for Private 5G secures and simplifies private 5G deployments for the centralized 5G core, helping providers:
- Enable zero trust connectivity: Secure site-to-site connectivity over the internet without a routable network (5G UPF to Core), and ensure users and devices (UE) are not on the same routable network as apps in the MEC, DC, and cloud.
- Secure apps and data: Minimize the egress and ingress attack surface as well as identify workload vulnerabilities, misconfigurations, and excessive permissions.
- Secure communications: Prevents compromise and data loss with inline content inspection.
- Provide digital experience management: Quickly resolve performance issues with visibility into device, network, and app performance.
Zscaler Private Access App Connectors, Branch Connectors, and Cloud Connectors, along with Zscaler Client Connector, can protect customer devices and workloads on 5G networks today. A version of Branch Connector designed to protect 5G core technologies from breaches was released in mid-2023, with further enhancements coming in 2024.
Together with our partners, we’re empowering customers to securely embrace private 5G.
Suggested Resources
FAQ
Frequently Asked Questions
4G offers data rates of up to roughly 100 Mbps, while 5G can offer up to 20 Gbps, but 5G offers more than increased data transfer speeds. 4G communications latency, or the delay in data being sent, ranges from about 60-100 milliseconds, whereas 5G latency can be under 5 milliseconds for certain use cases. Regarding bandwidth and the volume of simultaneous connections, a 4G network can support several thousand devices in one square kilometer, while a 5G network can support a million.
5G can improve security by providing faster, more reliable, and more secure communication between devices. It also enables real-time security monitoring and analysis because data can be transmitted and received almost instantaneously. Additionally, the use of virtualization and software-defined networking in 5G networks provides greater flexibility and scalability, enabling more efficient and effective security measures to be implemented.
5G uses advanced encryption algorithms and protocols that are more difficult to hack than those used by 4G LTE and Wi-Fi, making 5G networks more secure. 5G networks also incorporate multiple layers of defense, such as firewalls, intrusion detection, and prevention systems, encryption, and other security capabilities built into core network functions.