In my previous blog I talked about how enterprises can use the software-defined access technologies to mitigate risk by reducing the exposure created by traditional remote access technologies. Now, we’ll discuss the benefits of the software-defined perimeter (SDP)—a technology Gartner calls zero trust network access (ZTNA)—as it relates to making cloud adoption a bit easier, for everyone.
The cool thing about SDPs is that they build off of the traditional model of protecting internal services from external threats, but their software design gives them a unique characteristic—the ability to run in any environment. SDPs can run in private clouds, public clouds, and within the data center without the need to make any changes to the existing environment. Their agnostic architecture makes the SDP particularly helpful when it comes to securing access to applications that have recently moved from the data center to a public cloud service like Azure or AWS. It reduces the networking and security complexity that is often introduced in this transition and that frequently slows cloud migration initiatives.
Say “buh-bye” to complexity
Enterprises can use SDP to accelerate the adoption of cloud, enable hybrid and multi-cloud strategies, and protect sensitive data at the same time. Once an application is migrated to a cloud provider, an admin can quickly deploy a connector, which front-ends the application running in a cloud instance, and then creates a new policy to route user traffic to the new connector (this process is even easier if there is already a group of connectors running in the cloud). Only users who are authorized to access the application are able to connect to it, and for anyone else, the application is completely invisible (think of this as a way of this is an isolated community of cloud apps and users). The whole process can take just five minutes in some cases! No network segmentation, no VPN gateway additional appliances or ACLs required. Just software.
Give the people what they want
User experience is a major benefit of the SDP because they provide the seamless cloud-like user experience that users now expect. Users no longer need to think about whether they are accessing an application that is running in the cloud or the datacenter and whether or not they need VPN in order to connect to it. Remote access just works, and it’s the same way for any app, for any device and from anywhere. The ability to integrate with popular SSO providers makes for an experience users truly welcome.
IT admins will appreciate the simplicity of the method, which leads to less time putting out fires related to failing or misconfigured appliances or addressing user complaints, and more time for solving business needs. Oh, and sensitive data becomes more secure, even as apps are moved to the cloud. But how?
Finally, peace of mind in the cloud
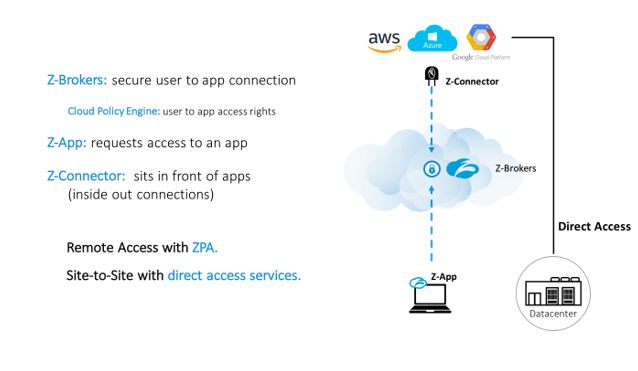
With SDPs, security becomes less of a barrier when moving internal services to the cloud. This is due to the zero-trust model that the method takes. Once apps have been migrated to AWS, Azure or Google Cloud Platform, IT security (or even the IT operations or Network admin) has the ability to use software to control who can access which cloud apps based on granular policies. This also helps when it comes to ensuring that third-party users are connecting to internal applications, securely. These policies can be set at a global level and can be created based on user, user group, application, and application groups. The brokered approach of SDP creates a secure mediation between users and applications, and centralizes security across any hybrid environment. Users are able to connect to applications even though they are never actually placed on the network. Cloud applications are never exposed to the internet, as the SDP creates an isolated environment for it. This protects against DDoS attacks which stem from external sources, primarily the internet. Data travels through TLS-based, encrypted micro-tunnels which are on a per app, per user basis. Admins can also use their own PKI infrastructure for double encryption.
Not bad, especially when you consider there is no need for appliances either.
To learn more about how SDP and ZTNA can be used to help enterprises adopt cloud more quickly and to secure access to cloud applications (at a global scale) read this case study about MAN Diesel & Turbo SE. You can also view our on-demand webinar discussing remote access to AWS.
To learn about ZTNA, read the new Gartner Market Guide.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Chris Hines is head of product marketing for Zscaler Private Access and Z App.





