Zscaler Blog
Get the latest Zscaler blog updates in your inbox
Cloud Workloads: Cybersecurity Predictions for 2024
The year 2023 witnessed explosive transitions in the cloud security market, with every aspect of the ecosystem—vendors, products, and infrastructure—undergoing significant change. Looking ahead to 2024, cybersecurity for workloads (VMs, containers, services) in the public cloud will continue to evolve as customers continue to strike a balance between aggressive cloud adoption and compliance with corporate security needs. Within this, CIOs and CISOs will challenge their teams to build a security platform that consolidates point products, supports multiple clouds (AWS, Azure, and GCP), and automates to scale security operations. As a result, we will see zero trust architecture leading the way in securing cloud workloads, real-time data protection, and centralized policy enforcement. Here are the top 5 trends we believe will unfold in 2024.
1. Lateral threat movement into clouds from on-premises environments will increase
The cloud is where organizations' most valuable assets—applications and data—are heading. Attackers are employing innovative techniques that involve compromising an organization's on-premises network and laterally moving to its cloud domain. These techniques are seeing increased popularity with threat actors as inconsistencies persist between on-premises and public cloud environments.
An attack detailed by the Microsoft Security research team (source: MERCURY and DEV-1084: Destructive attack on hybrid environment) exemplifies this trend. The threat actors first compromised two privileged accounts, then leveraged them to manipulate the Azure Active Directory (Azure AD) Connect agent. Two weeks prior to deploying ransomware, the threat actors used a compromised, highly privileged account to gain access to the device where the Azure AD Connect agent was installed. We assess with high confidence that the threat actors then utilized the AADInternals tool to extract plaintext credentials of a privileged Azure AD account. These credentials were subsequently used to pivot from the targeted on-premises environment to the targeted Azure AD environment.
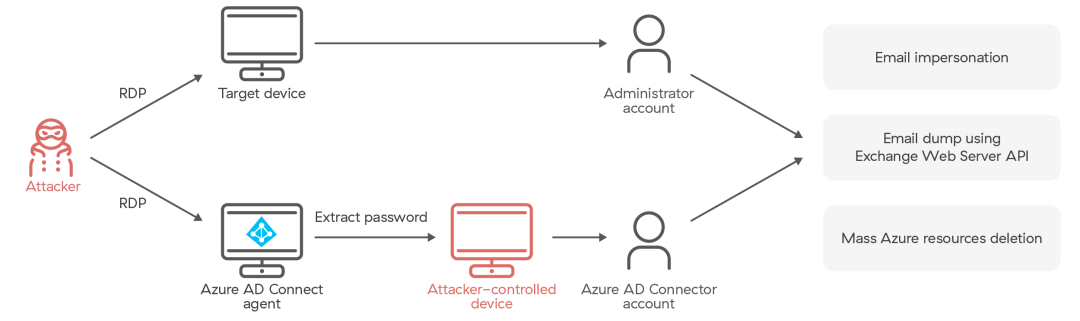
Fig. On-premises compromise pivots to the public cloud
2. Serverless services will significantly widen the attack surface
Serverless functions offer tremendous simplicity, allowing developers to focus solely on writing and deploying code without worrying about its underlying infrastructure. The adoption of microservices-based architectures will continue to drive the use of serverless functions due to their reusability as well as their ability to speed up application development. However, there is a significant security risk associated with serverless functions, as they interact with various input and event sources, often requiring HTTP or API calls to trigger actions. They also utilize cloud resources such as blob stores or block storage, employ queues to sequence interactions with other functions, and connect with devices. These touchpoints increase the attack surface, as many of them involve untrusted message formats and lack proper monitoring or auditing for standard application layer protection.
Fig. Serverless functions can access the full stack of additional services, creating a wide attack surface
3. Identity-based security policies will be redefined as it pertains to public cloud protection
As workloads start to mushroom in public clouds, each CSP will bring their own disparate identity capabilities. Unlike with users, there is no one ring (Active Directory) to rule them all. IT shops will continue to deal with disconnected identity profiles across on-premises, private cloud, and public cloud for workloads. That said, in 2024, security teams will continue to deal with multiple workload attributes to write their security policies, and higher level abstractions (like user defined tags) will start to gain wider adoption as such. This will drive consistency between cybersecurity and other resource management functions (billing, access controls, authentication, reporting) for cloud workloads.

Fig. User Defined tags will be used to implement zero trust architecture to secure workloads in the cloud
4. Enterprises will evaluate and deploy cloud-delivered security platforms that support multiple public clouds
Staffing people and building architectures specialized to secure each public cloud will place the onus on security teams to seek out the solutions that work best for them. Enterprises will evaluate tools from CSPs such as cloud firewall point solutions, but will increasingly look for architectures that can centralize their cloud security policy definitions, enforcements, and remediations. Only when cyber prevention is delivered from one central platform can cyber defense be applied to all workloads—not just a few selective ones.
5. CIOs' willingness to hedge their bets across AWS, Azure, and GCP will dictate the implementation of security tools that can span multiclouds.
When it comes to vendor best practices, CIOs are looking to diversify their cloud infrastructure portfolios. Doing so allows them to reduce reliance on a single vendor, integrate infrastructure inherited from mergers and acquisitions, and leverage best of breed services from different public clouds such as Google Cloud BigQuery for data analytics, AWS for mobile apps, and Oracle Cloud for ERP.
Every cloud vendor preaches the notion of “shared responsibility” when it comes to cybersecurity, placing the onus on the customer to implement a security infrastructure for their cloud resources. Savvy IT shops will ensure that they pick a cybersecurity platform that can support multiple public cloud environments. Customers can’t possibly entertain the idea of separate security tools for each public cloud—rather, they will standardize on one platform for all their needs.
Deploying workloads in the public cloud is not a new trend in the corporate world, but the topic of cloud workload security continues to get hotter and hotter. While there are no clear answers yet, there are a few indications that customers will navigate towards in 2024. Namely, zero trust, as it provides immediate benefit in the near-term and a solid framework for cloud workload security into the future. Want to learn more about zero trust for cloud workloads? Click here for more Zscaler perspectives.
This blog is part of a series of blogs that provide forward-facing statements into access and security in 2024. The next blog in this series covers Zero Trust predictions.
Forward-Looking Statements
This blog contains forward-looking statements that are based on our management's beliefs and assumptions and on information currently available to our management. The words "believe," "may," "will," "potentially," "estimate," "continue," "anticipate," "intend," "could," "would," "project," "plan," "expect," and similar expressions that convey uncertainty of future events or outcomes are intended to identify forward-looking statements. These forward-looking statements include, but are not limited to, statements concerning: predictions about the state of the cyber security industry in calendar year 2024 and our ability to capitalize on such market opportunities; anticipated benefits and increased market adoption of “as-a-service models” and Zero Trust architecture to combat cyberthreats; and beliefs about the ability of AI and machine learning to reduce detection and remediation response times as well as proactively identify and stop cyberthreats. These forward-looking statements are subject to the safe harbor provisions created by the Private Securities Litigation Reform Act of 1995. These forward-looking statements are subject to a number of risks, uncertainties and assumptions, and a significant number of factors could cause actual results to differ materially from statements made in this blog, including, but not limited to, security risks and developments unknown to Zscaler at the time of this blog and the assumptions underlying our predictions regarding the cyber security industry in calendar year 2024.
Risks and uncertainties specific to the Zscaler business are set forth in our most recent Quarterly Report on Form 10-Q filed with the Securities and Exchange Commission (“SEC”) on December 7, 2022, which is available on our website at ir.zscaler.com and on the SEC's website at www.sec.gov. Any forward-looking statements in this release are based on the limited information currently available to Zscaler as of the date hereof, which is subject to change, and Zscaler does not undertake to update any forward-looking statements made in this blog, even if new information becomes available in the future, except as required by law.
Was this post useful?
Disclaimer: This blog post has been created by Zscaler for informational purposes only and is provided "as is" without any guarantees of accuracy, completeness or reliability. Zscaler assumes no responsibility for any errors or omissions or for any actions taken based on the information provided. Any third-party websites or resources linked in this blog post are provided for convenience only, and Zscaler is not responsible for their content or practices. All content is subject to change without notice. By accessing this blog, you agree to these terms and acknowledge your sole responsibility to verify and use the information as appropriate for your needs.
Get the latest Zscaler blog updates in your inbox
By submitting the form, you are agreeing to our privacy policy.




