UPDATE: see the requirements for the extension at the end of the post
UPDATE: an new version is available
UPDATE: BlackSheep for Linux is available here
UPDATE: If you use FileVault on MacOSX, you might be prompted for a password. See this thread for more information.
You've probably all heard of Firesheep by now, a Firefox add-on which lets anyone hijack a user's session to various popular web applications when they're using an open wireless network. While sniffing/stealing session credentials is nothing new, Firesheep exposes this capability to the masses by automating the process so that absolutely no technical know-how is required. Unfortunately, it is actually quite difficult to defend against Firesheep because most sites only permit SSL connections during the initial login, not while surfing other pages. As such, while your username and password are encrypted, your session ID is available to all other machines on the same network.
In a previous post, Mike showed how to detect the use of Firesheep on a local network by using Wireshark and Scapy. Well, today, we're releasing a new Firefox add-on which makes the detection of FireSheep available to everyone and we're calling it BlackSheep!
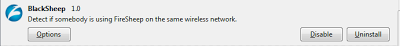 |
| BlackSheep installed |
BlackSheep is a Firefox add-on which warns users if someone is using Firesheep on their network. It also indicates the IP address of the machine that is spying on you
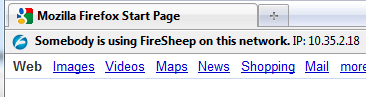 |
| BlackSheep warns that someone is using FireSheep |
How BlackSheep works
To understand how BlackSheep works, we first need to understand the details of FireSheep. FireSheep listens to the HTTP traffic on port 80. When it identifies a transaction to a known site (Facebook, Google, Yahoo!, etc.), it looks for specific cookie values which are then used to identify a specific user. This phase of the attack cannot be detected as it is done passively.
When FireSheep identifies a user session, it then makes a request to the same site using the user's cookie values in order to retrieve user information such as their name, picture, etc. This active network activity is however visible to others on the local network.
BlackSheep detects the active connection made by Firesheep. It does this by making HTTP requests to random sites handled by FireSheep every 5 minutes (configurable) with fake values. BlackSheep then listens to all HTTP requests on the network to detect if somebody else is using the same fake values.
Use Firesheep to combat.... Firesheep!
BlackSheep is based on the FireSheep source code. It reuses the same network listening back-end and the list of sites and corresponding cookies, etc. This ensures that the fake traffic generated by BlackSheep is what Firesheep is expecting.
BlackSheep in action
First, install BlackSheep here. If you already have FireSheep installed, make sure it is disabled, otherwise BlackSheep will detect that you are using FireSheep.
Then select the correct network interface in the options menu (same as FireSheep).
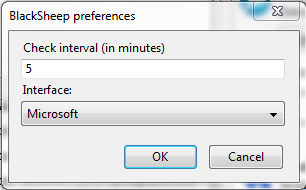 |
| BlackSheep preferences menu |
By default, BlackSheep generates fake traffic every 5 minutes. You can change this value in the option settings.
If Firesheep is detected, you will see the following warning in your current browser tab.
 |
| BlackSheep notification |
Finally, here is a video of BlackSheep in action.
Surf safe!
Requirements
In order to install BlackSheep, you need:
- Mac OS X: 10.5 or newer on an Intel processor.
- Windows: XP or newer. Install Winpcap first!
- Linux: available here
- Firefox: 3.5 or newer. 32-bit only.
-- Julien





