Most Fake AV pages mimic a Windows Desktop application running. In addition, the Fake AV pages have generally been the same regardless of which browser they are viewed. I recently found a new type of Fake AV page that looks different on each browser. And it also uses internal elements of those browsers.
Internet Explorer version
The version for Internet Explorer looks more like the previous pages I've seen.
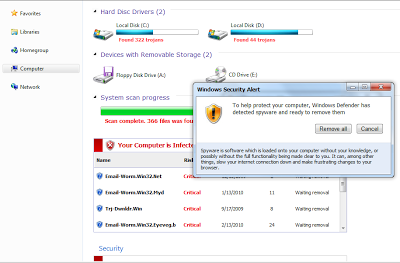 |
| Fake AV page for Internet Explorer |
The malicious executable InstallInternetDefender_722.exe is detected by only 9.5% of AV!
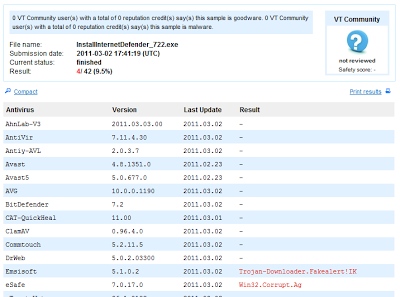 |
| Virustotal results for malicious executable |
Firefox version
The version displayed in Firefox browsers is very interesting. It looks like the security warning Firefox shows for malicious and phishing sites.
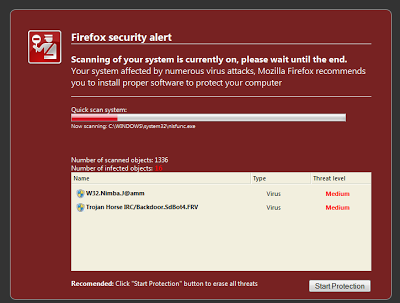 |
| Fake AV page for Firefox |
The source code of the pages shows that the page is using internal elements of the browser to construct the page:
- chrome://global/skin/netError.css
- chrome://global/skin/icons/blacklist_favicon.png
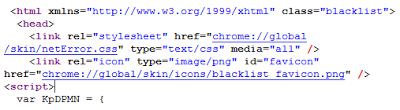 |
| Use of internal Firefox elements |
The warning looks very legitimate.
Chrome version
Like for Firefox, the Chrome version looks like a legitimate browser warning.
Safari version
For Safari, only the first popup box is tailored to the browser. The main page is the same as Internet Explorer.
Fake AV continues to evolve. This new version for Firefox will surely fool more than one user.
-- Julien
Chrome version
Like for Firefox, the Chrome version looks like a legitimate browser warning.
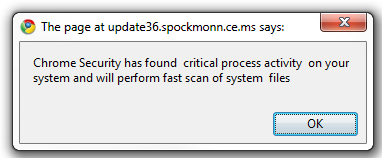 |
| First warning from the fake AV page |
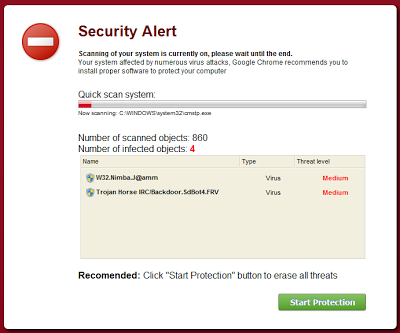 |
| Fake AV page fro Chrome |
Safari version
For Safari, only the first popup box is tailored to the browser. The main page is the same as Internet Explorer.
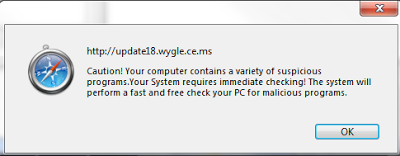 |
| Fake Av warning for Safari |
Fake AV continues to evolve. This new version for Firefox will surely fool more than one user.
-- Julien






