 If you look at the source of page, you will find the malicious iframe injected into the source code as shown below:
If you look at the source of page, you will find the malicious iframe injected into the source code as shown below: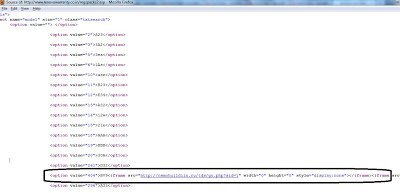
The malicious iframe points to the site “hxxp://nemohuildiin.ru/tds/go.php?sid=1". This malicious site actually redirects the user to another malicious website hosting the
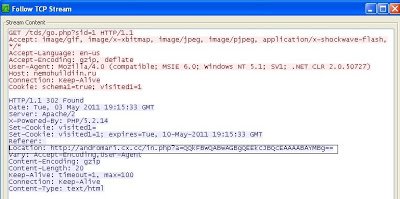 Observing the “Location” field in the HTTP header, we see the user is being redirected to another malicious website hosting the malicious toolkit, a common pattern that we’ve seen in the past. The malicious website “hxxp://andromari.cx.cc” returns obfuscated malicious JavaScript code to exploit different vulnerabilities and downloads malicious binaries. Here is the screenshot of the malicious JavaScript sent by this kit
Observing the “Location” field in the HTTP header, we see the user is being redirected to another malicious website hosting the malicious toolkit, a common pattern that we’ve seen in the past. The malicious website “hxxp://andromari.cx.cc” returns obfuscated malicious JavaScript code to exploit different vulnerabilities and downloads malicious binaries. Here is the screenshot of the malicious JavaScript sent by this kit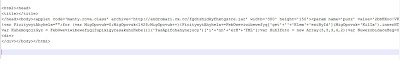 I am not going into the details of the exploits themselves as they are related to the same vulnerabilities and toolkit, which I have discussed in an earlier blog. The malicious site hosting the
I am not going into the details of the exploits themselves as they are related to the same vulnerabilities and toolkit, which I have discussed in an earlier blog. The malicious site hosting the Umesh