/ What Is OT Security?
What Is OT Security?
OT security is the measures and controls in place to protect OT systems—which use purpose-built software to automate industrial processes—against cybersecurity threats. As the convergence of information technology and OT drives greater automation and efficiency in industrial systems, OT security has become a requirement of critical infrastructure management.
What’s the Difference Between IT and OT Security?
While IT systems are designed for various uses for people, devices, and workloads, OT systems are instead purpose-built to automate specific industrial applications, presenting some key differences in how they are secured.
One challenge lies in the technology life cycle. That of an OT system can span decades, whereas the life cycles of IT systems, such as laptops and servers, are often between four and six years. In practical terms, this means OT security measures often need to account for infrastructure that’s out of date, and may not even be possible to patch.
Some OT systems are also highly regulated. For example, US Food and Drug Administration (FDA) regulations require the manufacturers of diagnostic machines to support them for 20 years from the date of deployment. OT systems are also managed by business units, and CIOs and CISOs are not typically responsible for procuring, managing, or securing these systems.
OT and IT security do have something important in common, however: IT and OT both increasingly depend on connections to the internet or public networks.
Why Is OT Cybersecurity Important?
Years ago, OT assets weren’t connected to the internet, so they weren’t exposed to web-borne threats like malware, ransomware attacks, and hackers. Then, as digital transformation initiatives and IT-OT convergence expanded, many organizations added point solutions to their infrastructure to address specific issues, such as patching. This approach led to complex networks in which systems didn’t share information, and therefore couldn’t provide full visibility to those managing them.
Industrial control systems (ICS)—the devices, controls, and networks that manage different industrial processes—are critical in maintaining operations and revenue streams. Compromise of common industrial systems, such as supervisory control and data acquisition (SCADA) systems, distributed control systems (DCS), and various customized applications, can have massive consequences for an organization, making them attractive targets for cyberattacks.
The Need to Converge IT and OT Network Security
IT and OT networks are often disparate systems, unable to track activities holistically across an organization’s ecosystem as OT network teams report to the COO, while IT network teams report to the CIO. Each of the teams protects just half of the total ecosystem, simultaneously dividing and duplicating security and threat management efforts—and making it much more difficult to protect the organization from cyberthreats.
OT Security in Operational Environments
OT systems include sensors, monitors, actuators, generators, industrial robots, programmable logic controllers (PLCs), remote processing units (RPUs), and other technologies that, today, are part of the Industrial Internet of Things (IIoT). OT devices can include dangerous machinery, and ensuring their security is crucial to ensuring human safety as associated cyber risk grows—Gartner has predicted that cybercriminals will have managed to weaponize OT environments to physically harm humans by 2025.
Operational Technology Security Best Practices
Operational technologies vary widely, as do today’s available security solutions—but there are certain broad steps you should take as part of any effective OT security strategy:
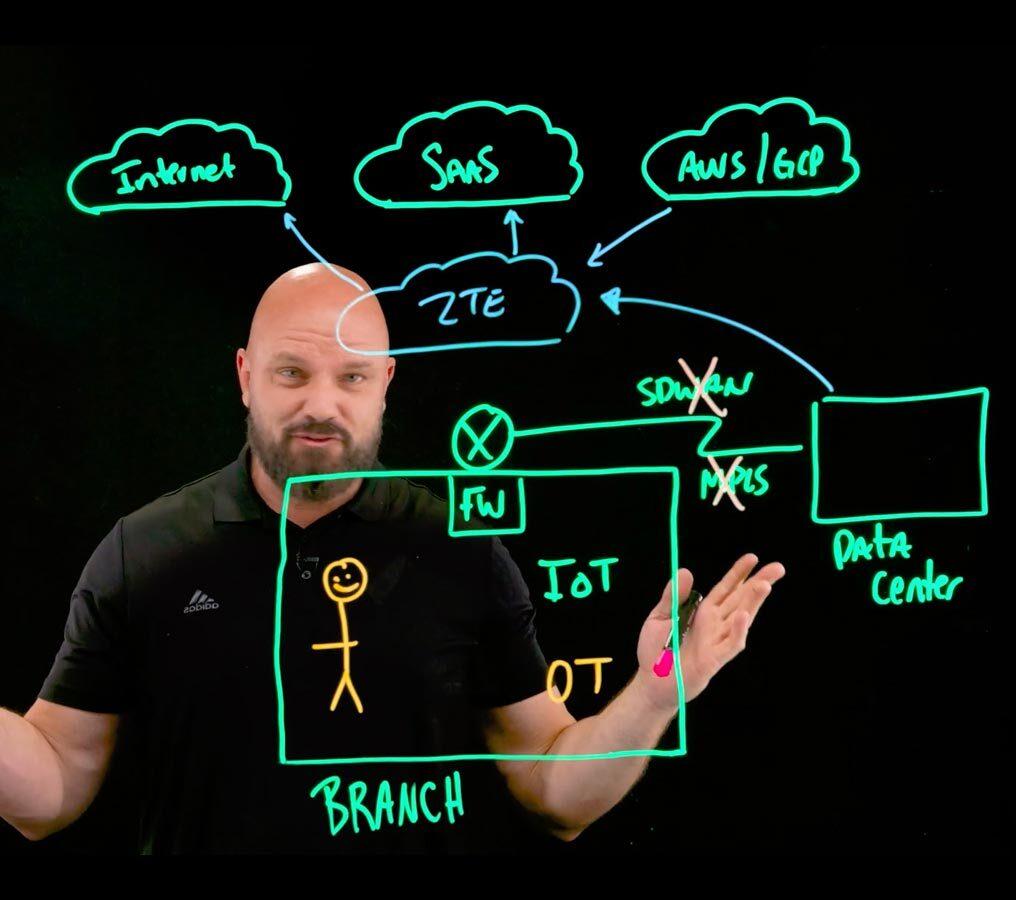
- Map your environment. Make sure your team can identify the digital locations of all devices in your network in real time. This is especially crucial for maintaining visibility and control in branch office environments, where highly distributed systems can increase your attack surface.
- Monitor your entire ecosystem for suspicious activity. Identifying unusual or otherwise anomalous activity in your network—including vendor and service provider traffic—is key to reducing security risks and maintaining a strong security posture.
- Adopt a zero trust framework. Zero trust assumes any device, user, or network may be a threat until the entity is authenticated. In branch environments, where employees and IoT devices connect from various locations, zero trust ensures that only verified users and devices can access resources.
- Enact application-level microsegmentation. Unlike traditional flat network segmentation, microsegmentation prevents users, including malicious insiders, from discovering applications they are not authorized to access.
- Leverage identity and access management. Identity management and access controls are extremely important in IT environments, but absolutely paramount in OT environments, where compromises can be physically destructive, even dangerous to human safety.
- Educate your workforce. Helping your employees understand the types of threats they can expect to face, and the potential vectors of those threats, can hugely reduce your overall risk.
The Role of Zero Trust in Branch Security
Zscaler and OT Security
A zero trust approach is the most effective way to ensure robust OT security, with adaptive, context-based application access that doesn’t depend on network access. With an effective zero trust architecture in place, any user—an employee, a contractor, or a third party—can only access the applications and systems they need to do their job, with no complex firewall stacks or VPNs required, all while your apps and network stay invisible to the open internet.
Zscaler Private Access™ (ZPA™) is the world’s most deployed zero trust network access (ZTNA) platform, providing:
- A powerful alternative to VPN: Replace risky, overloaded VPN with ZPA to eliminate unnecessary traffic backhauling and gain secure, low-latency access to private applications.
- Hybrid workforce security: Empower your users to securely access web apps and cloud services from any location or device, with a smooth user experience.
- Agentless access for third parties: Extend your secure private app access to vendors, contractors, suppliers, and more with support for unmanaged devices, with no endpoint agent.
- Industrial IoT and OT connectivity: Provide fast, reliable, and secure remote access to industrial IoT and OT devices to facilitate maintenance and troubleshooting.
Check out these video case studies from our customers to see what made ZPA the clear choice for their OT environments: