Zero Trust Networking
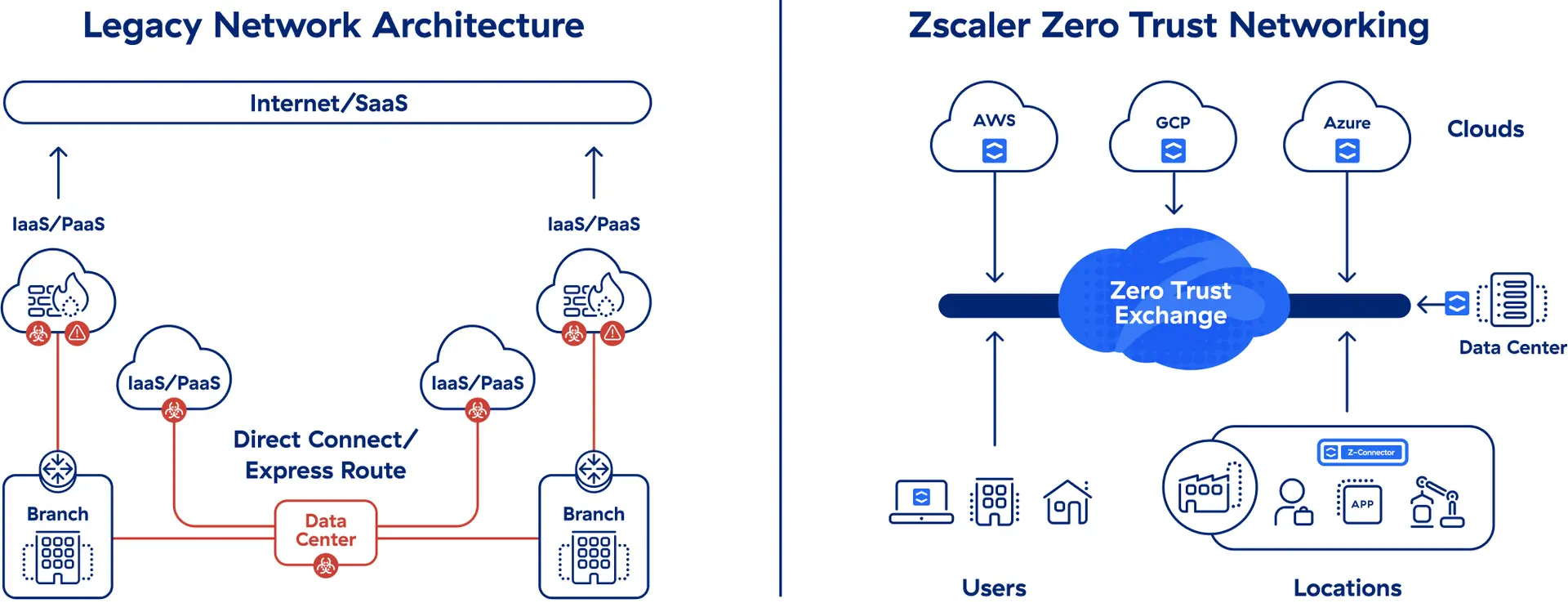
Legacy network architectures weren’t built for cloud-first environments and distributed workforces. They’re complex, inflexible, and vulnerable to cyberthreats like ransomware.
Legacy networks can’t do zero trust
Zscaler Zero Trust Networking allows users and devices to securely communicate with applications according using—wherever they are located—without the use of firewalls/VPNs, and provides end-to-end visibility to help optimize digital experience. Organizations can realize the benefits of single-vendor SASE with the security of zero trust.
What sets Zscaler Zero Trust Networking and SASE apart?
Connectivity is a non-routable network overlay
Eliminates DC/cloud DMZs and site-to-site VPNs
AI-powered cyberthreat and data protection (TLS inspection at scale)
Expose and fix network, app, or device issues
Zero trust principles lead to better security outcomes
In a zero trust architecture, all users, devices, and applications are inherently untrusted and can’t freely communicate with each other. Connectivity is brokered as needed based on business policies, identity, and context.
Solution Details
Zero Trust Networking for Users
Provide fast, secure, and direct connectivity to applications for your distributed workforce, third-party contractors, and B2B customers while delivering an exceptional user experience.
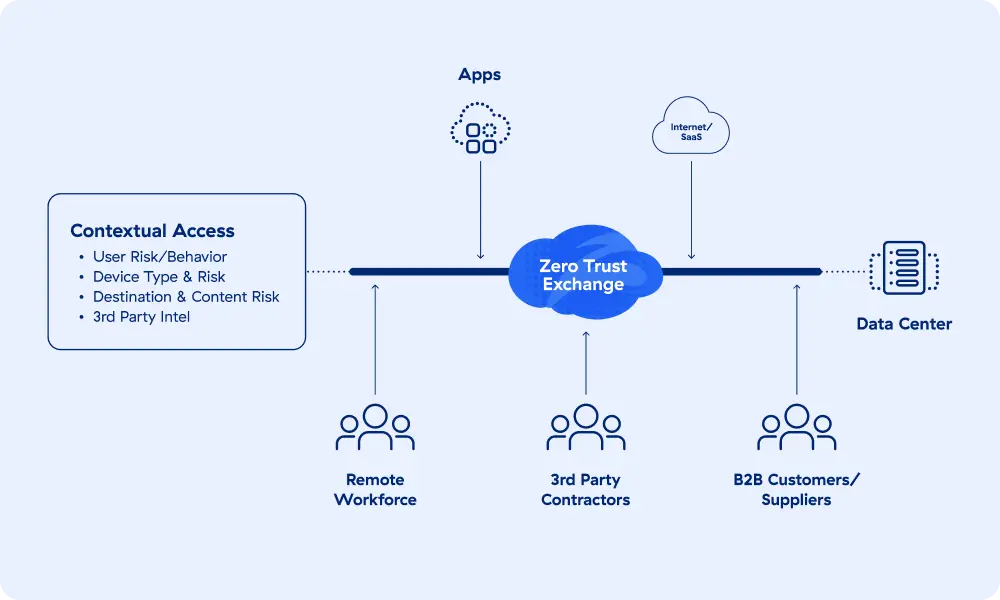
Zero Trust Remote App Access
Replace VPNs/VDI with zero trust access for your remote workforce.
Client Connector
Forward all traffic from managed endpoints (supports all leading operating systems).
Browser-Based Access
Give third party users clientless browser-based access to private apps.
Privileged Remote Access
Secure remote access to OT systems for vendors without exposed ports or VPNs.
Zero Trust SD-WAN
Securely connect your sites and data centers without the complexity of VPNs, ensuring zero trust access between users, IoT/OT devices, and applications based on business policies.
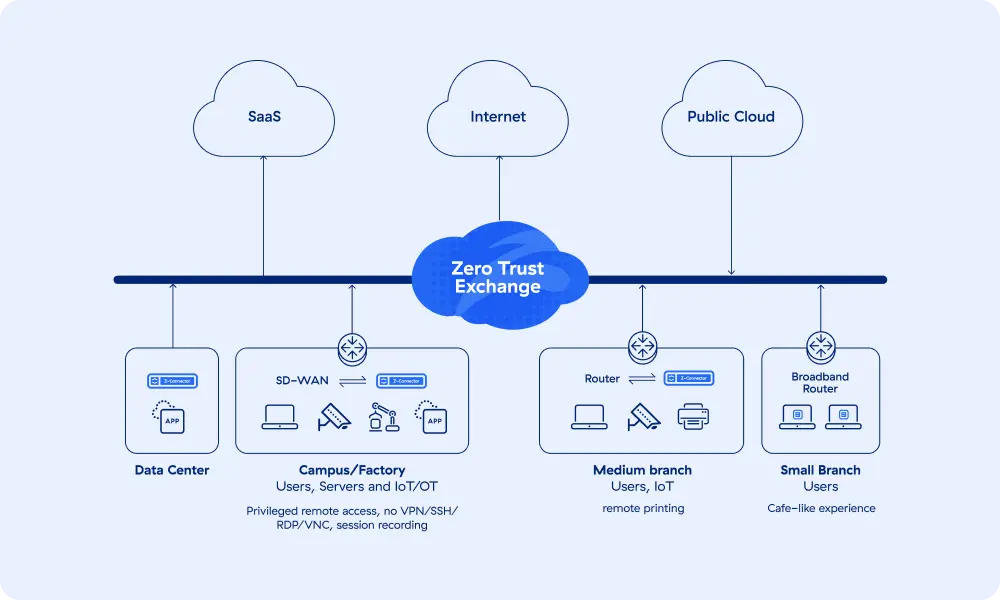
Secure Branch/Factory Connectivity
Secure branch-to-cloud and branch-to-DC without MPLS or site-to-site VPNs.
Secure Internet/SaaS Access
Enforce cloud-based TLS/SSL inspection to provide cyber and data protection for user and IoT/OT device traffic.
IoT Discovery and Control
Discover and classify IoT devices. Secure internet/SaaS and private app access.
China Premium Access
Provide high-quality domestic and international internet, SaaS, and private app access.
Zero Trust Workload Communications
Securely connect your cloud workloads and radically simplify security by eliminating lateral movement, reducing operational cost and complexity, and ensuring consistent threat and data protection.
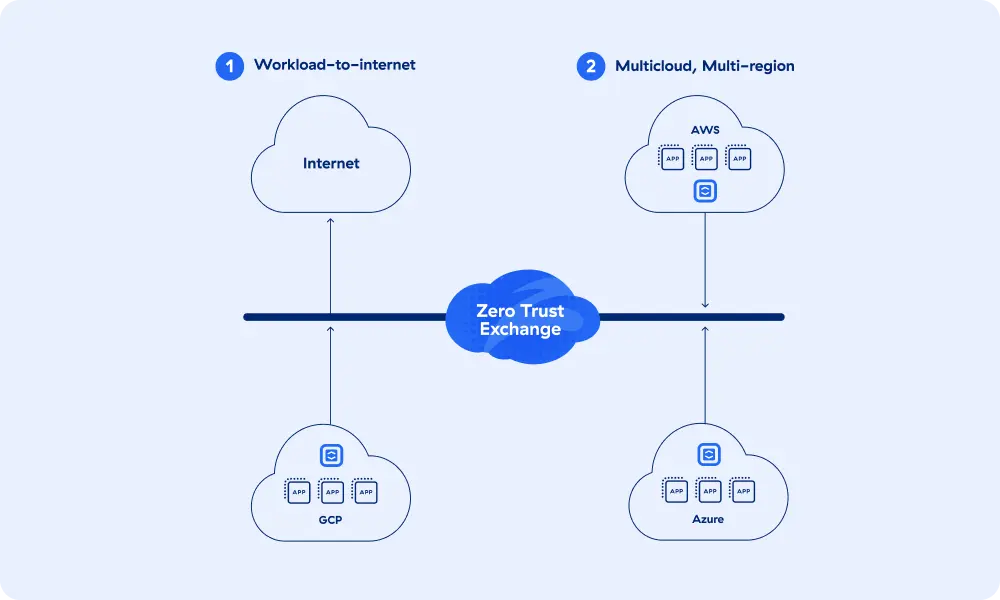
Multicloud Connectivity
Securely connect VPCs/VNETs across public clouds and regions.
Secure Internet/SaaS Connections
Provide TLS/SSL inspection for cyber and data protection.
Zero Trust Visibility
Zero trust architectures shut out existing network monitoring tools. Regain end-to-end visibility from device to app. Rapidly detect user experience issues and expose root cause using AI. Accelerate fixes and put employees back to work faster.
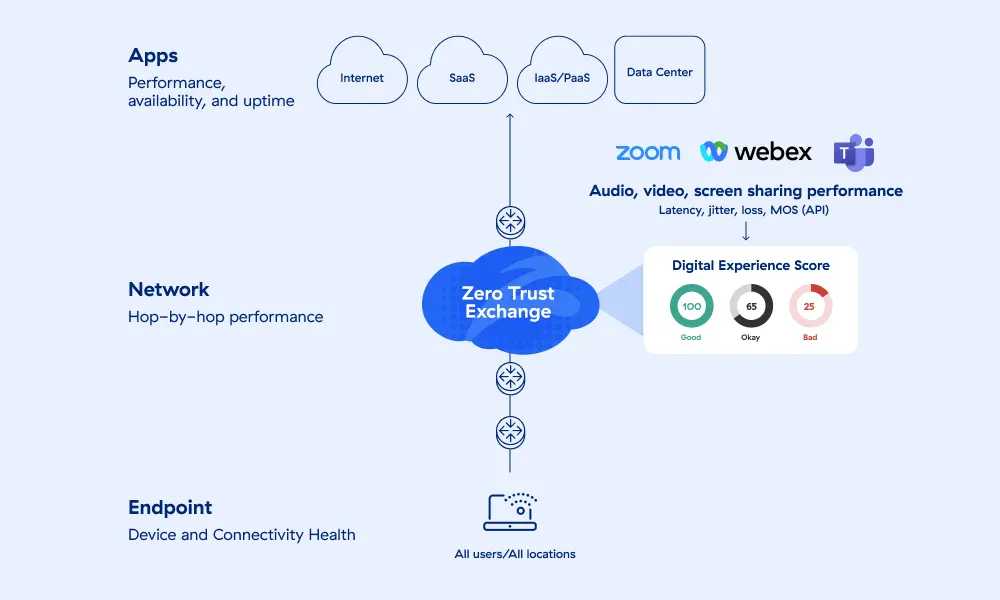
Network, App, and Device Monitoring
Get end-to-end visibility, and consolidate your monitoring stack.
AI-Powered Analysis to Accelerate MTTR
Instantly expose root causes of poor end user experience.
IT Self Service to Reduce Tickets
Intelligently detect device performance issues and guide users to fix them.
Proactive Incident Detection
Get in front of developing issues impacting offices, regions, or users.
Experience the power of the Zscaler Zero Trust Exchange
A comprehensive platform to secure, simplify, and transform your business
01 Business Analytics
Gain insight and optimize risk, IT, and business performance
02 Cyberthreat Protection
Take a holistic approach to securing users, workloads, and devices
03 Data Protection
Leverage full TLS/SSL inspection at scale for complete data protection across the SSE platform
04 Zero Trust Networking
Connect to apps, not networks, to prevent lateral movement with ZTNA


The impact of true zero trust, as told by Zscaler customers
Thousands of successful transformation journeys all began with one foundation.


Enabling work from anywhere and zero trust connectivity for all branches, factories, and IoT/OT
“Zero Trust SD-WAN ... in combination with policy automation and experience monitoring as part of the Zscaler platform, will help us achieve operational excellence.”
—Rui Cabeço, Service Group Manager for Outbound Connectivity, Siemens

Request a custom demo
Let our experts show you how Zero Trust Networking provides fast, reliable access to the internet and private apps with a direct-to-cloud architecture.



