
Log4j Vulnerability Resource Center
Zscaler is here to help you mitigate the impact of Log4Shell and prevent other zero-day vulnerabilities

Join our expert-led webinar for insights on how to manage the long-term impact of the Log4j vulnerability
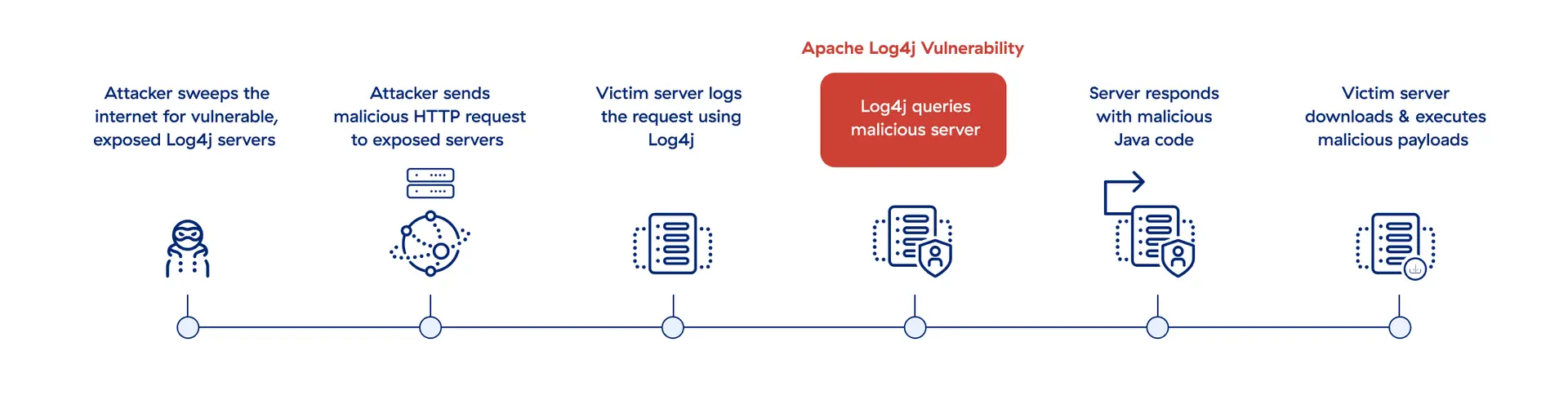
The Log4Shell exploit allows attackers to take over devices and carry out a range of attacks against vulnerable targets.
Apache Log4j is an open source logging library used in millions of enterprise applications and cloud services. By now, many organizations have updated their Log4j libraries and protected their most critical applications and assets, but Log4j’s widespread use can make it difficult to conclusively hunt down across the enterprise. Plus, sophisticated attackers could have planted backdoors in vulnerable systems before patching, allowing them to break in and carry out future attacks.
This is why you need a long-term mitigation strategy for Log4Shell.
This is why you need a long-term mitigation strategy for Log4Shell.
Stop Log4j with Zero Trust
Prevent Log4j exploits with a zero trust architecture
A zero trust architecture relies on four key tenets to hide vulnerable applications from attackers, detect and block intrusions, and mitigate the damage of successful attacks by eliminating lateral movement.
Eliminate the external attack surface
Make apps and servers invisible, impossible to compromise
Prevent compromise
Stop web app infections and exploit activity with full TLS/SSL inspection
Prevent lateral movement
Limit the blast radius with zero trust network access and integrated deception
Prevent data exfiltration
Stop data exfiltration attempts using inline DLP with TLS/SSL inspection
Why Zscaler
Gain peace of mind with Zscaler
Do you have Apache applications and servers that can’t be patched? Placing them behind the Zscaler Zero Trust Exchange™ hides them from attackers to eliminate vulnerable backdoors.
See how Zscaler Private Access™ eliminates exposure of vulnerable applications.






