Securely connect your branches and factories without the complexity of firewalls and VPNs
Legacy branch architecture exposes your organization to ransomware attacks, lateral threat movement, and operational complexity. Zero Trust SD-WAN offers a simple, cost-effective, and secure architecture to connect campuses, factories, and branches while segmenting OT and IoT devices.
Speed up deployments and reduce complexity
Boost performance, agility, and user experience
Minimize costs and business risk
The Problem
Traditional SD-WAN facilitates the spread of ransomware
Your users and devices need secure access to critical applications across the web, public clouds, and private data centers. Traditional software-defined wide area network (SD-WAN) solutions achieve this by extending your network everywhere. Unfortunately, they also enable attackers to enter and move freely throughout your network.
Expanded attack surface
Remote branches create more entry points, making firewalls and VPN gateways potential enablers of zero day threats.
Lateral movement risk
Infected branch devices can spread ransomware across the network, causing outages in under an hour.
High costs and complexity
Managing firewalls, proxies, and IP-based policies increases operational costs and reduces agility.
Poor user experience
Traffic backhauling and redundant security checks degrade application performance and frustrate users.
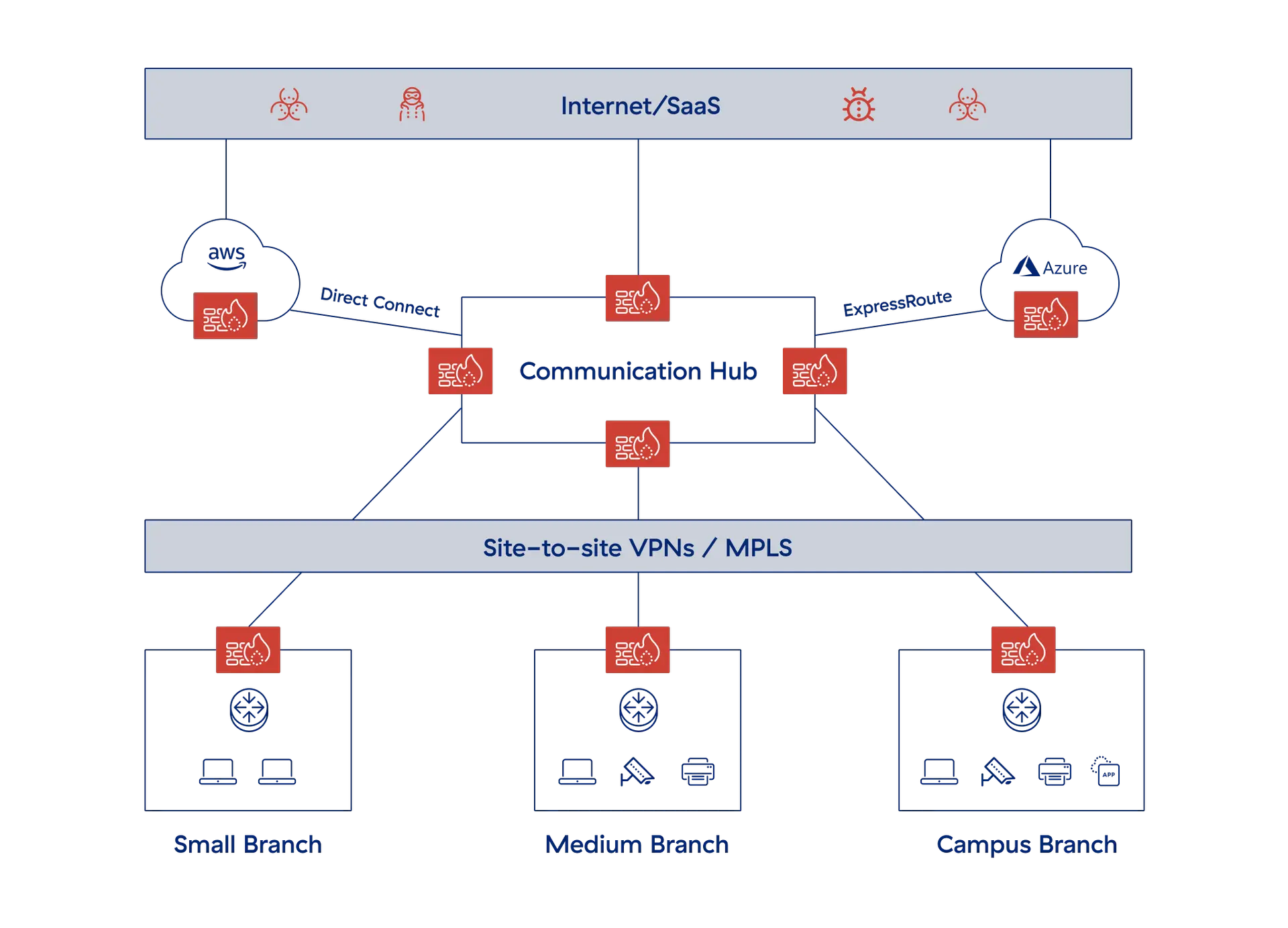
Product Overview
Zscaler Zero Trust SD-WAN securely connects users, devices, and workloads across branches, data centers, and the cloud. Unlike traditional architectures, branches are segmented and secured much like cafés, with traffic securely forwarded to the Zscaler platform over any broadband connection—eliminating VPNs and overlay routing complexity.
Built on the industry-leading Zscaler Zero Trust Exchange™, Zero Trust SD-WAN enforces granular, context-aware policies to ensure secure access, protect against cyberthreats, and prevent data loss. Branch traffic is inspected in real-time, delivering robust security and a seamless user experience.
Benefits
Connect and protect your entire ecosystem
Accelerate branch deployment
Deploy branches rapidly, with built-in segmentation to prevent lateral movement and secure legacy OT systems, ensuring fast and secure connectivity.
Segment without legacy firewalls
Eliminate the need for east-west firewalls and simplify IT infrastructure by removing VPNs, proxies, NAC switches, and unnecessary routing complexity.
Prevent lateral threat movement
Provide direct access to applications, not your network, unlike the open attack surface inherent in site-to-site VPN architecture.
Improve user experience and productivity
Replace complex site-to-site VPNs with a direct-to-cloud architecture that improves application traffic flow and performance.
Product Details
Accelerate connectivity to your branches, factories, and data centers without the complexity of VPNs or overlay routing. With a physical or virtual Zscaler Edge appliance deployed as a gateway or in one-armed mode, you can manage ISP connections and forward traffic to the Zero Trust Exchange.
- Zero touch provisioning with predefined templates
- Flexible traffic forwarding policy and selection criteria
- Unified zero trust policy for user-to-app, IoT device-to-app, and server-to-server
- Dynamic application-aware path selection
- Agentless zero trust device segmentation
Use cases
Zero Trust SD-WAN in action

Eliminate complex site-to-site VPNs or hub-and-spoke networks with a direct-to-cloud architecture, improving performance.

Enable branches in one IT environment to quickly connect to private apps in another, with no need to integrate networks, with zero touch provisioning.

Provide clientless browser-based access to SSH/RDP ports on OT assets for third parties while removing exposed ports or VPN endpoints, eliminating the attack surface.

Get deeper visibility and insights into IoT devices at the branch. Automatically classify devices based on traffic profiles, and easily manage policy controls for IoT traffic.

our platform
The Zscaler Zero Trust Exchange
Secure user, workload, and device communication between and
within the branch, cloud, and data center.
Zero Trust Everywhere
Secure Data
- Find, Classify, and Assess Data Security Posture
- Prevent Data Loss Across All Channels
Secure AI
- Secure the Use of Public AI
- Secure Private AI Apps and Models
- Secure Agent Communications
FAQ
FAQs
SD-WAN can replace MPLS in most cases, but organizations with certain compliance or privacy requirements may use both. MPLS circuits can also serve as SD-WAN routes when required. As such, MPLS circuits can remain during a migration and later be phased out as appropriate.
Zero Trust SD-WAN closes critical network security gaps left by traditional SD-WAN. It extends zero trust across the environment, enabling consistent policy enforcement for users, IoT/OT devices, and applications. By connecting users and devices to apps over a zero trust network overlay, it reduces network management complexity and eliminates lateral threat movement.
Yes, SD-WAN is well-suited for organizations with changing or temporary branches. It enables quick setup, easy management, and cost-effective connectivity using public internet, making it more flexible than traditional options like MPLS.
Request a demo
See how Zero Trust Branch can help you eliminate lateral movement and extend zero trust access to all users, devices, and servers anywhere.













