
Videos
Zero Trust as a Competitive Advantage with Zscaler and Microsoft
OVERVIEW
Zscaler and Microsoft enable the modern workforce with zero trust
DETAILS
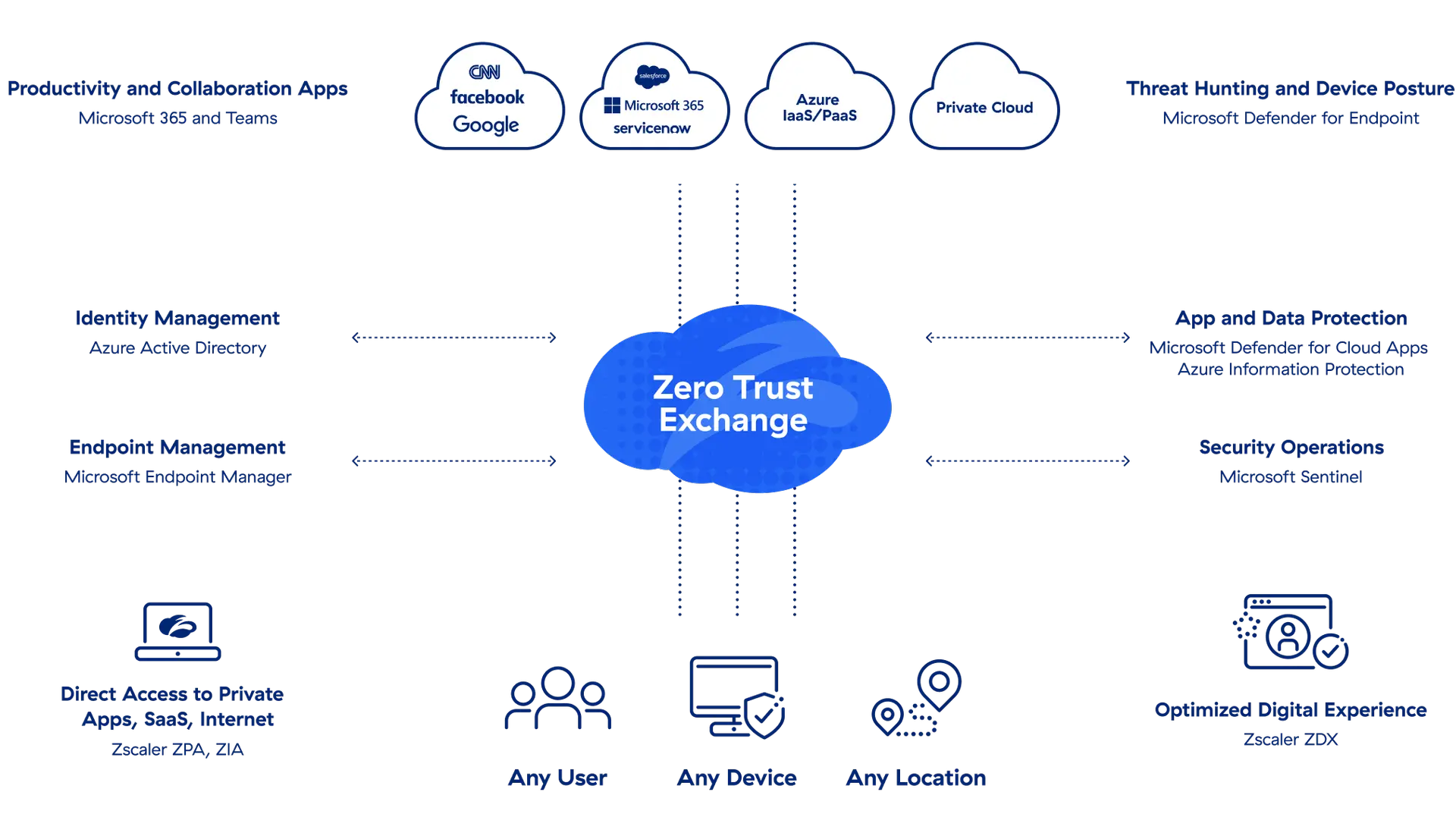
Deep integrations that deliver zero trust security
Fast, secure access to protect users, data, and apps
- Microsoft Azure Active Directory
- Microsoft Sentinel
- Microsoft 365 Defender
Simplified operations, reduced cost and complexity
- Microsoft 365 Networking Partner
- Microsoft Teams, SharePoint
- Microsoft 365 posture and threat protection
Exceptional digital experiences for improved productivity
- Global peering with the Microsoft network
- Traffic prioritization with bandwidth control
- Direct localized connectivity worldwide
Fast, secure access for all apps and security intelligence
- Leverage zero trust network access (ZTNA) to private apps with Zscaler Private Access™ (ZPA™) and Azure Active Directory
- Get ZTNA connectivity to SaaS and internet applications with Zscaler Internet Access™ (ZIA™) and Microsoft 365 Defender
- Minimize false positives and improve threat hunting, response, and mitigation times with Microsoft Sentinel
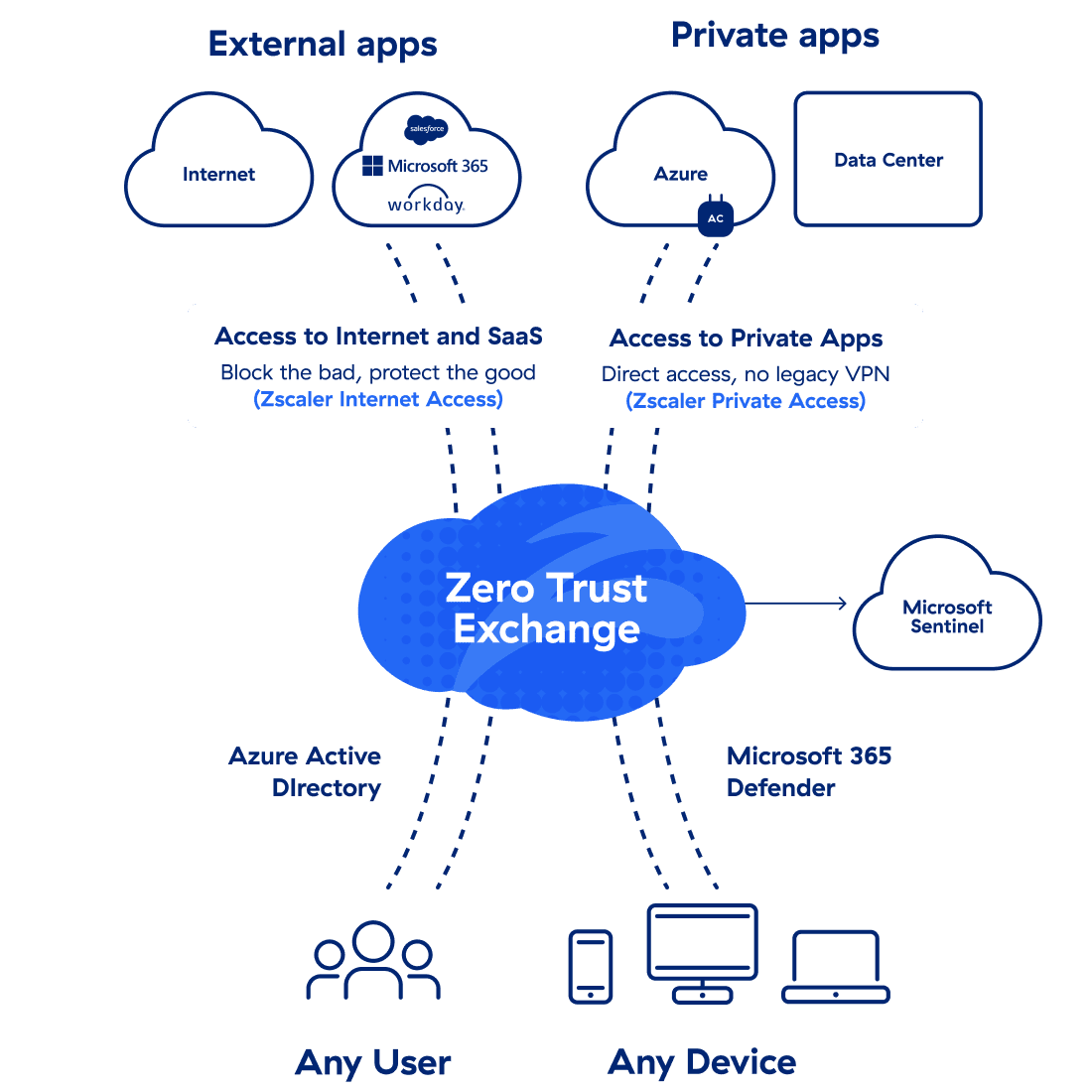
Seamless integration with Microsoft 365
Simplified operations, reduced cost and complexity, and improved user experience
One-click setup
- Microsoft 365 configuration for faster setup
Microsoft 365 enhancements
- Traffic visibility for bandwidth prioritization
- Tenant restrictions and TCP optimization
Improved user experience
- Deep integration with Zscaler Digital Experience™ (ZDX™) for Microsoft 365 performance signals

Optimized connectivity for exceptional digital experiences and improved productivity
Serving thousands of our joint Zscaler and Microsoft customers worldwide

160+ Zscaler points of presence and peering with the Microsoft network ensure minimal hops to Microsoft Cloud Services

ZDX provides cloud path visibility, making it easy to proactively identify and resolve connectivity issues
ZERO TRUST EXCHANGE
The Zscaler Zero Trust Exchange™ is the world's largest security cloud
160+
500B+
9B+
250K+
Recognition
Microsoft + Zscaler
Zscaler and Microsoft solutions are tightly integrated, providing our mutual customers with modern, cloud native zero trust security while increasing user productivity and accessibility. With thousands of customers benefiting from our platform solutions, it’s no surprise that Zscaler has been selected as the ISV Partner Winner of important Microsoft Awards such as Zero Trust Champion of the Year and Microsoft ISV Partner of the Year, and is a founding member of the Microsoft 365 Networking Partner Program and the Microsoft Intelligent Security Association.
Thousands of leading customers benefit from our integrations





































