Zero Trust SASE builds on the industry’s leading SSE platform with a fresh approach to SD-WAN that reduces business risk.
Prioritize your mission
Provide secure connectivity for your workforce and locations, so you can focus on your goals.
Improve cyberthreat protection
Better protect your crown jewels with superior security built for today's dynamic organizations.
Lay a strong base for IoT adoption
Securely adopt IoT and OT without widening your attack surface or complicating policy enforcement.
The Problem
Traditional SD-WAN overextends trust
Traditional SD-WAN helped reduce the costs associated with dedicated WAN circuits. However, it was built on network technology that extends trust between locations. As a result, it:
Expands the attack surface
by exposing more IP addresses to the public internet
Heightens ransomware risk
by letting attackers move freely across your network
Increases complexity
by requiring additional equipment to provide network security
Gartner projects that 60% of new SD-WAN purchases will be integrated into a single-vendor SASE offering by 2026. It’s time to ensure new deployments are fit for purpose in a world of greater cyber risk. A zero trust architecture provides the best foundation for securely connecting workforces and locations to their work.

Zscaler Recognized as a Leader in Forrester Wave™: Secure Access Service Edge Solutions, Q3 2025
Our innovative SASE approach earned the top placement on Strength of Strategy.
Solution Overview
The first SASE platform built on zero trust
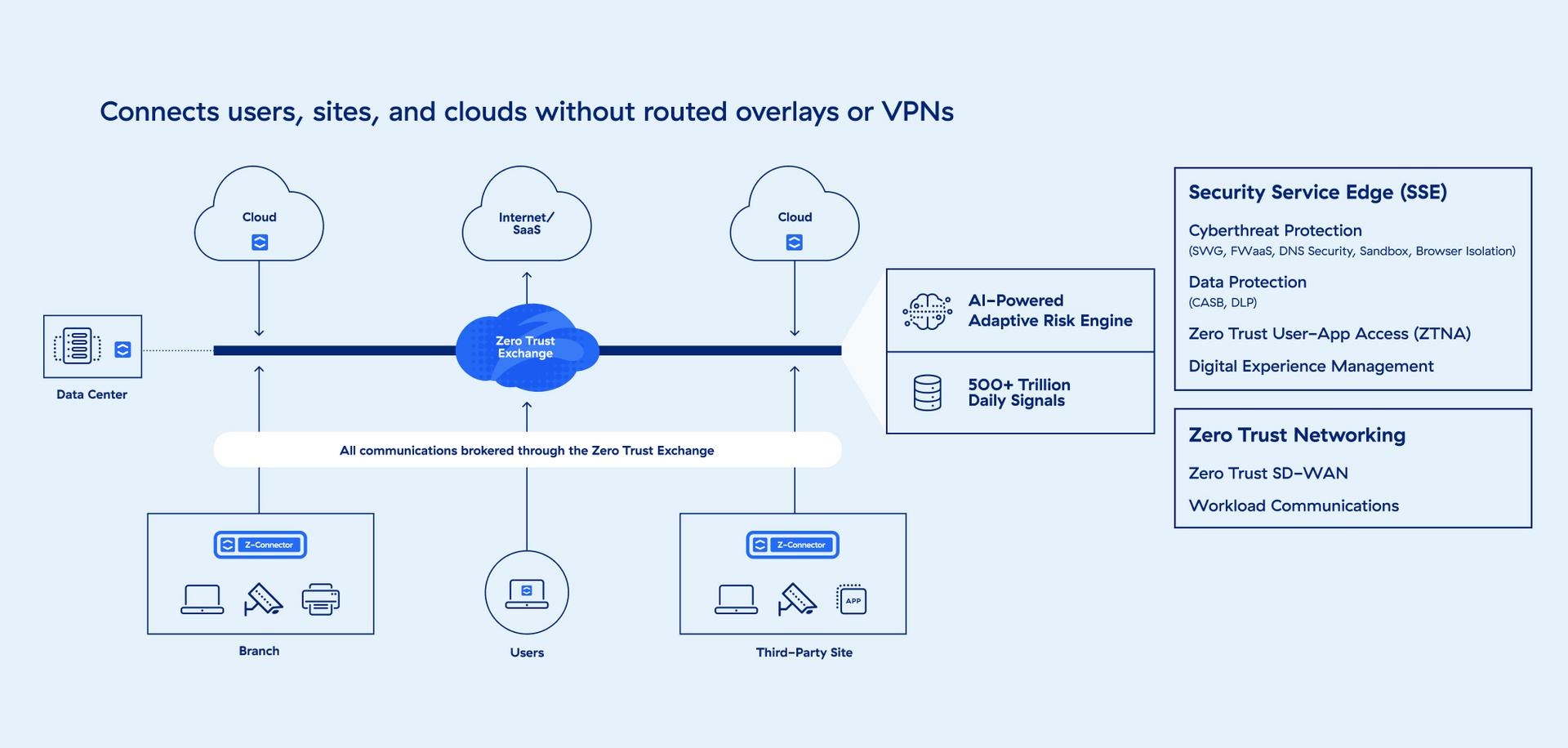
Zscaler Zero Trust SASE builds on the leading AI-powered security service edge (SSE) platform with a new approach to SD-WAN that securely and reliably connects users, locations, and cloud services via the Zscaler Zero Trust Exchange™.
Benefits
Simplify IT and security
Extend zero trust beyond workforces
Enforce zero trust security for IoT/OT devices, servers, and guests in branches.
Unify security and network access
Implement a single-vendor SASE framework with a simpler, proxy-based architecture.
Improve user experiences
Enforce security as close to users as possible, eliminate unnecessary backhauling, and optimize latency and bandwidth usage.
Reduce cost and complexity
Remove the need for multiple security point products by unifying security with zero trust.
solution Details
Prepare your organization for what’s next with Zero Trust SASE
Zscaler Zero Trust SASE provides least-privileged access for workforces, devices, workloads, and business partners across managed offices. Made up of six core technologies, it eliminates the need for complex and costly network-based security that fails to prevent breaches.
Zero trust software-defined wide area network (SD-WAN)
Optimize user experience and reduce complexity by auto-selecting the best route for traffic to cloud apps, the internet, and the data center.
Secure web gateway (SWG)
Prevent unsecured internet traffic from entering your network, shielding users and employees from cyberthreats, malicious traffic, and more.
Cloud access security broker (CASB)
Prevent data leaks, regulatory compliance issues, and malware infection by ensuring safe use of cloud apps and services. Increase visibility to help your team see policy violations.
Firewall as a service (FWaaS)
Replace physical firewall appliances with a cloud-based FWaaS that delivers advanced next-generation firewall (NGFW) capabilities, including access controls.
Zero trust network access (ZTNA)
Ensure trust is never assumed. Give remote users secure connectivity without placing them on your network by granting least-privileged access based on granular policies.
Digital experience management
Monitor performance end-to-end, providing smart AI-powered troubleshooting tools for your IT support team to help maintain an exceptional online experience.
Use Cases
Extend secure, dynamic connectivity

Extend cloud-delivered security out to workforces, applications, networks, and endpoints—no matter where they’re located.

Eliminate the need to backhaul traffic to a data center, and deliver a seamless user experience with security at the edge. Connections are brokered at 160+ points of presence worldwide.

Stay on top of threats, no matter how quickly they evolve. Zscaler operates the world’s largest security cloud, with more than 250,000 unique security updates per day.

Inspect and secure every connection. Zero Trust SASE defines security—including threat protection and data loss prevention (DLP)—as an integral part of the connectivity model.

Embracing AI-Powered Policy with Zscaler Zero Trust SD-WAN

our platform
The Zscaler Zero Trust Exchange
Secure user, workload, and device communication between and
within the branch, cloud, and data center.
Zero Trust Everywhere
Secure Data
- Find, Classify, and Assess Data Security Posture
- Prevent Data Loss Across All Channels
Secure AI
- Secure the Use of Public AI
- Secure Private AI Apps and Models
- Secure Agent Communications
FAQ
Zero Trust SASE redefines network security by integrating AI-driven security service edge (SSE) capabilities with Zero Trust SD-WAN. Unlike traditional SD-WANs, which rely on complex routing and additional appliances, Zero Trust SD-WAN focuses on connecting and securing users and locations without overlay routing or policy inconsistencies. It ensures simplified branch management, robust security, and seamless protection across distributed infrastructures.
SASE combines key networking and security technologies in a cloud-delivered framework. It includes software-defined wide area network (SD-WAN) for connectivity, secure web gateway (SWG) for web security, cloud access security broker (CASB) for cloud protection, zero trust network access (ZTNA) for access controls, and data loss prevention (DLP) for safeguarding sensitive data.
When evaluating SASE providers, focus on solutions that integrate robust SSE capabilities like SWG, CASB, and ZTNA with powerful SD-WAN functionality. Look for scalability, ease of deployment, and seamless integration with cloud services and zero trust frameworks. The ideal provider should offer proven performance, AI-driven threat detection, and centralized management for consistent visibility and control across distributed networks.




