As a cloud platform, ServiceNow delivers digital workflows that create great experiences and unlock productivity.. But it also consumes and distributes massive amounts of sensitive data, which in today’s world is typically accessed by users working from outside the corporate network and away from traditional security controls stuck in the data center. By extending a zero trust approach to cloud applications, such as those delivered on the Now Platform®, organizations can ensure that they remain secure from data loss and compliance violations while enabling faster responses to emerging security incidents.
In light of this, we’re excited to announce our new ServiceNow integrations which not only improve the platform's security posture against data loss and emerging threats, but also improves data visibility, data control, and security operations workflows within all areas of the Now Platform.
With Zscaler Data Protection integrations, ServiceNow customers can rest assured their most sensitive data remains secure from data exfiltration and compliance violations.
Let’s take a closer look at these integrations and some of the challenges they help ServiceNow customers solve.
Solving data threat challenges within the Now Platform:
Visibility into sensitive data and restoring compliance
Like any cloud application, visibility into sensitive data is a must when forming a comprehensive data protection strategy—especially when considering the need to uncover, remediate, and ultimately avoid compliance violations. By leveraging Zscaler CASB and DLP, ServiceNow customers can improve data protection across their ServiceNow instances. Zscaler scans the entire NOW customer deployment instance for sensitive data to identify risky exposure and compliance issues. In doing this, security teams can quickly understand where sensitive data lives, how it’s being used, and who is accessing it.
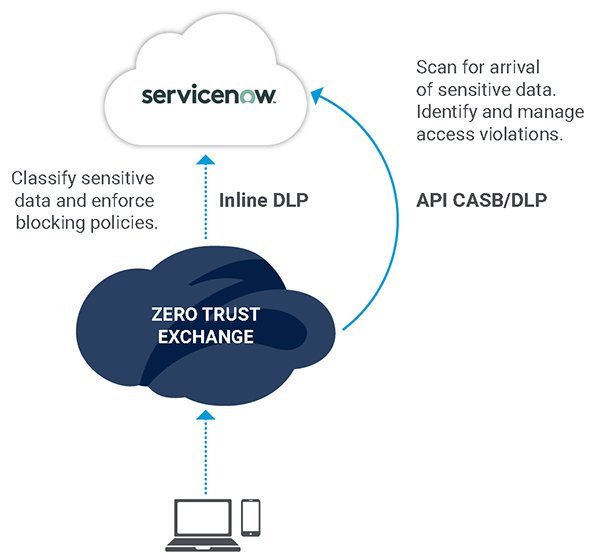
Figure 1: Restore data protection and compliance
Enabling work-from-anywhere and controlling unmanaged devices
With so many unmanaged and BYOD devices accessing the Now Platform, today’s businesses need more control on how this data is being accessed. Through the Zscaler Zero Trust Exchange, organizations can remove the risks associated with BYOD and unmanaged devices accessing ServiceNow data.
Zscaler Identity Proxy makes it easy for ServiceNow customers to authenticate unmanaged devices residing outside the corporate network by automatically restricting access from devices deemed too risky to access the platform. By redirecting to Zscaler, risky BYOD and unmanaged devices are prevented from accessing ServiceNow directly. Devices can only connect to ServiceNow through Zscaler to enforce security policies and access controls.
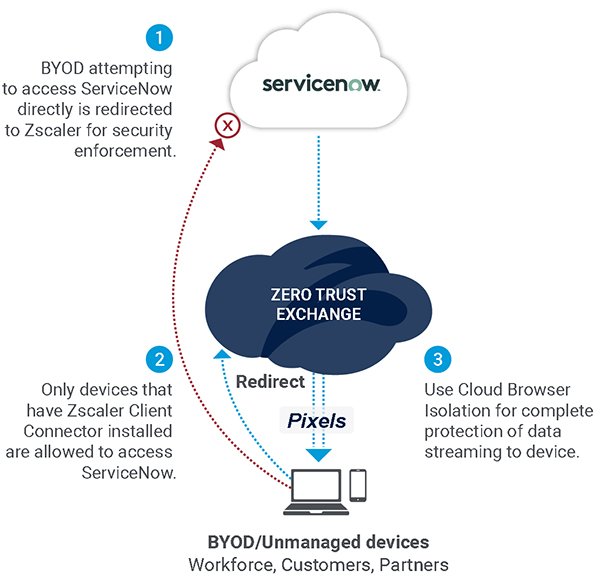
Figure 2: Securely enable work-from-anywhere
By preventing risky unmanaged and BYOD devices from accessing ServiceNow instances and sensitive data, ServiceNow customers can enable a more secure work-from-anywhere experience across secure managed devices only. Pair this with Zscaler Cloud Browser Isolation, which streams data to unmanaged devices via screen pixels, data can be accessed while preventing the downloading, copying/pasting, and printing of it.
Responding to data threats with closed-loop workflows
When security incidents that are logged lack context, it is extremely difficult to quickly triage and remediate threats in real-time. Together, ServiceNow Security Incident Response and Zscaler Threat Intelligence can automatically orchestrate response actions. By leveraging Zscaler threat intelligence and Cloud Sandbox, ServiceNow Security Operations (SecOps), you can accelerate security incident workflows. Risky IP domains and URLs can be blocked without manual intervention, while cloud misconfigurations can be corrected to help reduce the risk of a breach. Response time is reduced, and IT teams increase productivity. In addition, cloud misconfiguration can be logged in ServiceNow IT Service Management (ITSM) for further investigation and remediation.
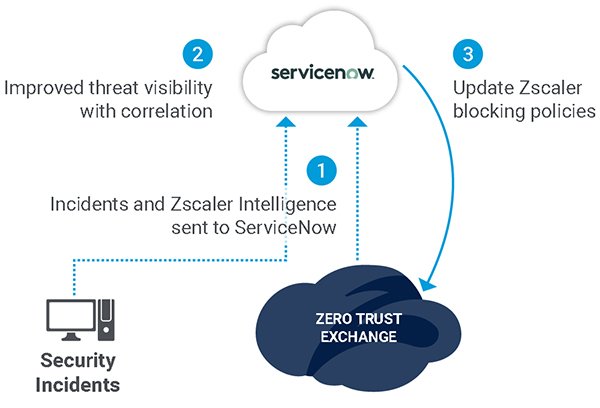
Figure 3: Improve security workflows
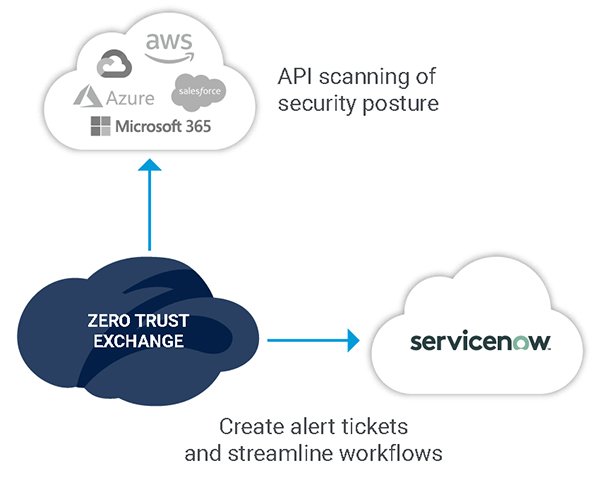
Figure 4: Quickly remediate cloud misconfigurations
Explore more
Learn more about Zscaler’s latest ServiceNow integrations with the resources below:
About Zscaler Data Protection
Zscaler Data Protection follows your users and the applications they are accessing, always protecting you against data loss. Zscaler inspects your traffic inline, encrypted or not, and ensures your SaaS and public cloud applications are secure, giving you the protection and visibility you need. The Zscaler Cloud Security Platform was built with compliance in mind, offering you an essential tool for complying with all major regulations and making data protection painless.





