/ What Is Web Security?
What Is Web Security?

Web Security vs. Web Application Security
Before we continue, let’s clarify these terms. Web security can also include web application security (also called website security), a subcategory of practices and tools that help secure public-facing websites. For the purposes of this article, we’ll be focusing specifically on web security solutions that secure servers or user endpoints as well as the traffic that moves between those and the internet.
What’s the Purpose of Web Security?
The massive importance of the internet for modern enterprises—and the accompanying growth in the sophistication, frequency, and impact of cyberattacks—has made web security critical to business continuity. It’s your first line of defense against threats that can lead to the exposure of sensitive data, costly ransoms, reputational harm, compliance violations, and a host of other consequences.
Once the domain of mostly small-time hackers, internet-borne threats have evolved into a massive black market business that touches the worlds of organized crime as well as state-sponsored espionage and sabotage. Some of the latest threats are incredibly sophisticated, able to easily fool the untrained eye or bypass legacy security. Plus, with an array of ready-made tools, exploit kits, JavaScript modules, and even fully developed campaigns for sale, even a novice actor can easily launch an attack.
Cybersecurity Ventures estimates that, by 2025, global cybercrime will cost US$10.5 trillion annually—a greater profit than the entire world’s major illicit drug trade—and half the world’s data will live in the cloud. Given what’s at stake, it’s easy to see why effective web security is so important today.
What Are the Benefits of Web Security?
For a modern enterprise, effective web security has broad technical and human benefits:
- Protect your business and stay compliant by preventing loss of sensitive data
- Protect customers and employees by securing their private information
- Avoid costly service interruptions by preventing infections and exploits
- Offer a better user experience by helping your users stay safe and productive
- Maintain customer loyalty and trust by staying secure and out of the news
Great strides in cloud and mobility technology let your employees and customers connect with you with unprecedented ease and flexibility. Unfortunately, that cuts both ways, and attackers have more ways to approach your organization’s wider attack surface. With the right web protections in place, you can spend more time taking advantage of the benefits, and less worrying about security threats.
What Does Web Security Protect Against?
Web security casts a wide net to protect users and endpoints from malicious emails, encrypted threats, malicious or compromised websites and databases, malicious redirects, hijacking, and more. Let’s look at a few of the most common threats in more detail:
- Ransomware: These attacks encrypt data, and then demand a ransom payment in exchange for a decryption key. In a double-extortion attack, your data is also exfiltrated.
- General malware: Countless variants of malware exist that can lead to anything from data leaks, spying, and unauthorized access to lockouts, errors, and system crashes.
- Phishing: Often carried out through email, text messages, or malicious websites, these attacks trick users into things like divulging login credentials or downloading spyware.
- SQL injection: These attacks exploit an input vulnerability in a database server, allowing an attacker to execute commands that let them retrieve, manipulate, or delete data.
- Denial of service (DoS): These attacks slow or even shut down a network device such as a server by sending it more data than it can process. In distributed DoS—that is, a DDoS attack—this is carried out by many hijacked devices at once.
- Cross-site scripting (XSS): In this type of injection attack, an attacker introduces malicious code to a trusted website by entering it in an unprotected user input field.
The ideal web security solution leverages multiple technologies to stop malware and ransomware, block phishing domains, restrict the use of credentials, and more—building a holistic defense.
Let’s look in a bit more detail at how this works.
How Does Web Security Work?
Web security functions sit between your environment’s endpoints and the internet. From there, they inspect traffic and requests traveling in both directions. No single technology monitors or inspects all traffic, but a “stack” of appliances—or a cloud-delivered platform of services, more effective today—provides holistic coverage to prevent policy violations, malware infections, data loss, credential theft, and so on.
Many solutions are available today, and some are more comprehensive than others. In a full stack, web security includes the following technologies:
- Secure web gateway (SWG) provides threat protection and policy enforcement for users accessing the web to prevent infections and block unwanted traffic.
- Firewall/IPS provides network security, app control, and visibility. Cloud firewalls stay up to date and scale to handle demand or encryption, making them a more practical option.
- URL filtering screens and blocks inappropriate access or content, also offering protection from web-borne malware.
- Sandboxing isolates software in an environment where it can be scanned and executed without the risk of infecting a system or other applications.
- Browser isolation loads webpages or apps in a remote browser and only sends the user pixels, preventing the downloading, copying, pasting, and printing of data or documents.
- DNS controls define rules that control requests and responses related to DNS traffic, allowing you to detect and prevent DNS abuses such as tunneling.
- Antivirus detects and neutralizes trojans, spyware, ransomware, and more. Many offerings also protect against threats such as malicious URLs, phishing, and DDoS.
- TLS/SSL decryption breaks open inbound and outbound encrypted traffic to inspect its contents, and then re-encrypts it to continue to its destination.
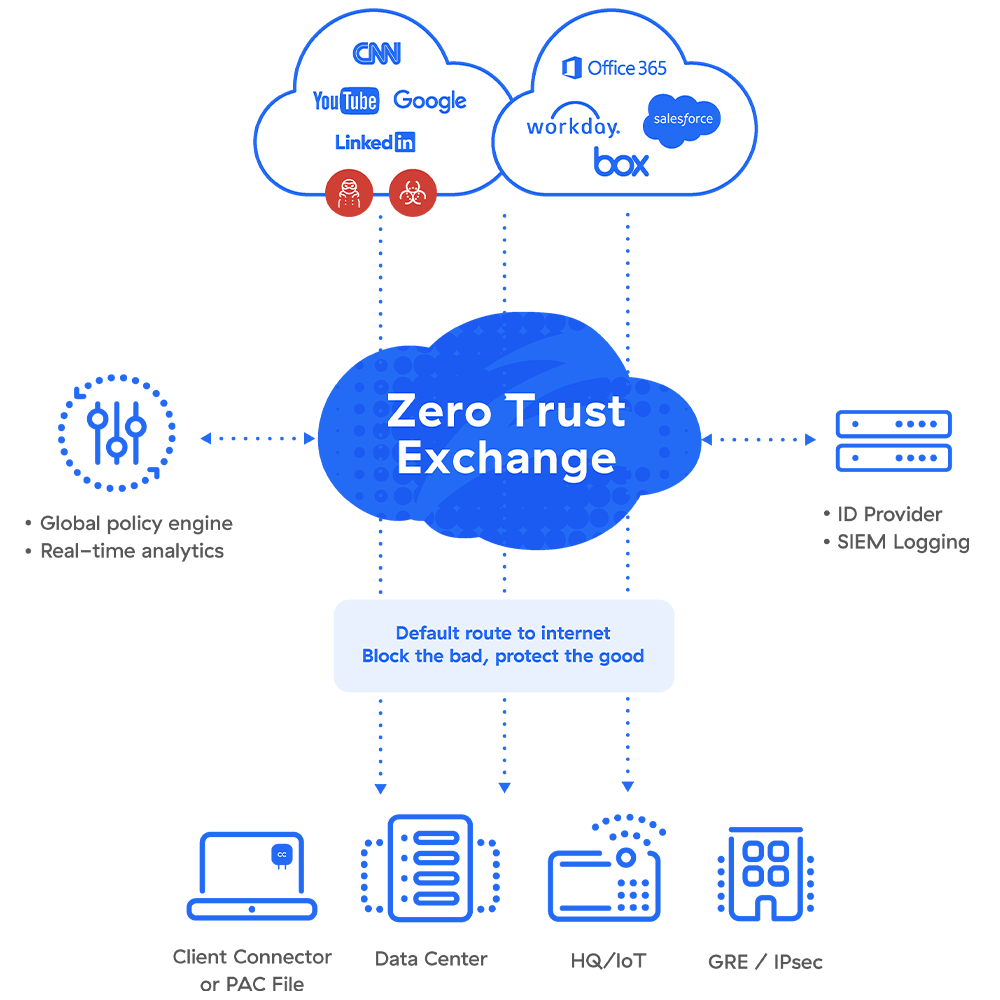
The Argument for Cloud-Delivered Web Security
As on-premises hardware, web security technologies would be housed in a SWG appliance in your data center. Your hardware stack could include firewalls, URL and DNS filters, sandboxing appliances, and many more to cover all functions.
The problem with a hardware-based approach is inevitable gaps. Appliances require ongoing patching to keep you safe from zero-day attacks, and if patching falls behind, you’re left with exploitable vulnerabilities. Appliances also have performance limitations—especially when it comes to TLS/SSL-encrypted traffic, which constitutes nearly all traffic today—meaning they can’t reliably root out hidden threats.
Moreover, far too many devices (often even from the same vendor) don't talk to each other, so correlating data between them is extremely difficult, even for highly skilled information security professionals.
A secure web gateway delivered as a cloud service, on the other hand, provides real-time threat protection and policy enforcement, preventing access to infected websites—even when your users are outside your corporate network—and blocking infected or unwanted traffic from entering your internal network.
How Zscaler Can Help
The Zscaler secure web gateway is 100% cloud-delivered, so it enforces security policies consistently, no matter where users connect, what endpoint devices they're using, or where applications are hosted. It’s built on a global multitenant cloud architecture for massive scalability, so it can inspect all encrypted traffic without degrading performance. Plus, our integrated, cloud native platform greatly reduces your operational complexity and costs compared to a hardware approach.
Zscaler Web Security Products
Far more than a single security service, Zscaler Internet Access™ includes cloud firewall/IPS, sandboxing, URL filtering, Cloud Browser Isolation, data loss prevention (DLP), cloud access security broker (CASB), and cloud security posture management (CSPM) to deliver airtight internet security across all your users, on- and off-network.
Zscaler was named a Leader in the Gartner Magic Quadrant for Secure Web Gateways for 10 consecutive years. In 2021, Gartner defined the security service edge—a new category that includes SWG—and subsequently recognized Zscaler as a Leader in the 2022 Gartner Magic Quadrant for Security Service Edge, with the highest “Ability to Execute.”